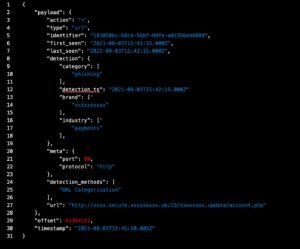
We have reported about executable malware files that masquerade as PDF files to trick users into opening them – but can PDFs actually contain viruses?
Yes, Adobe PDF documents can, unfortunately, carry different types of viruses or even malicious executable code. Many users dismiss suggestions that these can be dangerous since they are “just text and images”. PDF malware is typically hidden within multimedia content, hyperlinks, JavaScript code, or even system commands. These malware attacks execute when users open files or interact in any way with the embedded content after it is opened. These files can include static items such as images or text plus other dynamic details like forms. While PDF elements can make the document understandable, as well as visually appealing, they can also be corrupted to carry out malicious functions.
An Example of PDF Malware
Have you ever made a request to Bank of America regarding ACH CashPro? If not, you should ignore any email messages from Bank of America (BoA) and put them straight into your junk folder. On the other hand, if you are using BoA online services then be sure to validate and be vigilant about the content.
In 2014, an email from Bank of America reached one of my mailboxes (see image below). At first, it looked legitimate especially considering the message content. In reality, the email was from a malicious email hacker.
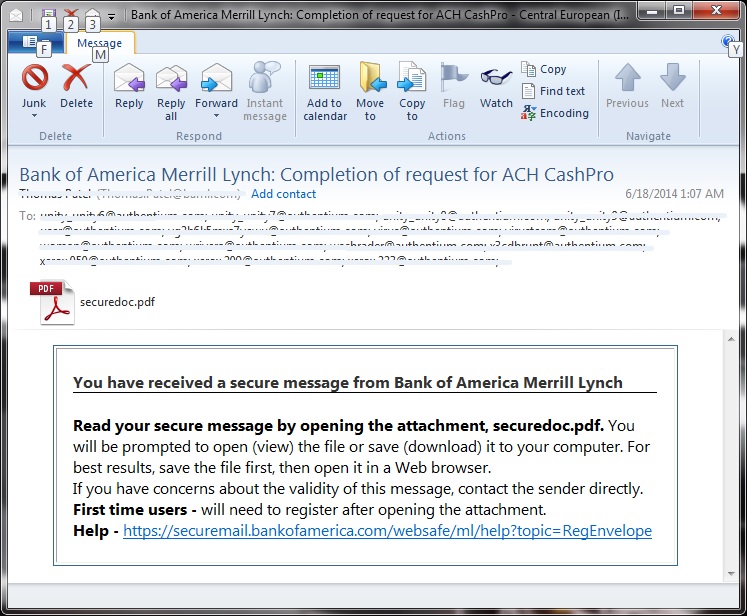
This maliciously crafted email message contains a link that points to a valid site from Bank of America. What is worrisome about this email is the PDF attachment (securedoc.pdf). The email says it is a secure message, so many email users were tricked into believing it was really one but it was not.
The email attachment was a specially crafted PDF malware which Cyren detects as exploit CVE100188. The PDF malware attachment attcked a known vulnerability (CVE-2010-0188) of Adobe Reader. When the affected user attempted to open the attached PDF file, the embedded script in the PDF file then validated the version of the target Adobe Reader. The malware attempted to attack the following specific versions of Adobe Reader as seen in its code:
9.303, 9.304, 9.4, 9.401, 9.402, 9.403, 9.404, 9.405, 9.406, 9.407, 9.5, 9.501, 9.502, 9.503, 9.504,10.101, 10.102, 10.103, 10.104, 10.105, 10.106, 11, 11.001
(The current version is 11.0.07)
If successfully exploited the malicious PDF then executes an embedded shellcode that downloaded another malicious executable Backdoor from the following link which Cyren detected as W32/Androm.AQ:
http://88.{–masked—}5.44/images/banniers1/Andr.exe
After successfully downloading the file, it then executesed and installed the downloaded file into the affected system to further compromise the user and system. The new malware is a backdoor and a remote attacker can take full control of the affected system from anywhere, at any time without the user’s knowledge.
The BoA email was probably sent out by another malware using gathered email addresses and could be received by any recipient. It made use of clever social engineering in order to entice unsuspecting users into opening the attachment.
There are a lot of malicious emails out there and you may be a recipient of one containing a malicious attachment (even a “plain old” PDF). As a precaution, never open potentially dangerous email attachments of any form especially from unknown senders. Should the email come from a known sender, don’t hesitate to verify the validity of the email from the sender and report it to IT administrators if it is unsolicited.
What To Watch Out For with PDF Malware
Multimedia Content
PDF documents containing multimedia content, such as Adobe Flash, video, or audio, can easily be corrupted by using malware embedded into the multimedia files. Typically, in this type of attack, you can download or play video and audio successfully. That said, if no malware protection is in place, a virus can launch and begin to carry out its background tasks. You should always use antivirus scanners in order to check embedded multimedia content. These files may contain hyperlinks which redirect you to malicious sites or even code that attacker use to manipulate your system remotely.
Hyperlinks
PDF documents carry a different level of trust than webpages. Hyperlinks in PDF text can be extremely harmful. Since it is normal to find resource links within PDFs, attackers can use this to lead you to malicious sites. Hackers can then compromise your system with downloads or manipulate you to provide information you would not otherwise give.
Destructive JavaScript
JavaScript is the programming language that is responsible for the creation of many dynamic elements and graphics on the internet. It is typically used on website pages in order to control the functionality and appearance of content. Attackers, however, use JavaScript to exploit PDF reader vulnerabilities, which then initiates the malware. The easiest way to tackle any malicious JavaScript files is by disabling JavaScript within your PDF reader. Doing so can unfortunately reduce the document’s functionality, so you may want to check for a virus first.
Code-Manipulated System Commands
PDF files can have code that instructs your computer to execute specific commands. If this code is infected with a virus, the command will launch malware and then compromise your system. It is crucial to use the official Adobe Reader and also keep it up to date in order to guard against these command-level attacks – protecting your system.
Protecting Against PDF Attacks
Update Your PDF Reader
The reason software updates are important is for improving the functionality and patching identified vulnerabilities in the software. It is also best to use Adobe Acrobat Reader directly. Additionally, instead of following links to update your reader from a third-party website, a popup notification, or a link, you will want to make sure you update your PDF editor or reader from within the actual application itself. Alternatively, visiting the official website and downloading the latest version is another way to ensure safety.
Disable JavaScript on Your PDF Reader
It’s also crucial to disable JavaScript when you are opening PDFs from untrusted sources. This is to avoid an infected document executing destructive JavaScript code.
Keep Systems and Applications Up-to-Date
Your PDF reader is not the only software that is susceptible to attacks within PDFs. All software will need to be updated regularly so malware does not slip through any potential cracks. The security measures of browsers or PDF readers might not be enough. Also, an antivirus scanner may not catch malware before you open a PDF. This leaves you depending on your operating systems to protect themselves.
Use Your Browser’s Built-in PDF Reader
Most popular browsers such as Google Chrome, Firefox, Safari, or Microsoft Edge have built-in PDF readers. These readers have a sandbox that provides device protection from threats that may be present in a PDF. In order to use browsers when reading PDFs, you will need to set the browser reader as your default software for that file type. Alternatively, you can also uninstall any other PDF reader programs so the browser reader becomes the default.
Avoid Email Attachments Sent By Unknown Senders
PDFs are typically sent by email since it has become the defacto standard for providing view-only documents. When you know the sender, be skeptical because some viruses can leverage your contacts’ trust in order to spread. For that reason, when you see an unknown sender’s emails, make sure to not open any attachments with a PDF file extension.
Final Thoughts
To get further up to speed on everything related to PDF Malware, discover Cyren’s malware protection services, or download our report on all things malware.