Cybercriminals constantly evolve their phishing tactics and use them as precursors for ransomware and business email compromise attacks.
Despite investments in secure email gateways, Microsoft 365 Defender, and security awareness training, an increasing number of phishing attacks penetrate enterprise email defenses every day…
Leaving security teams overwhelmed by alerts and users at a higher risk of compromising the business.
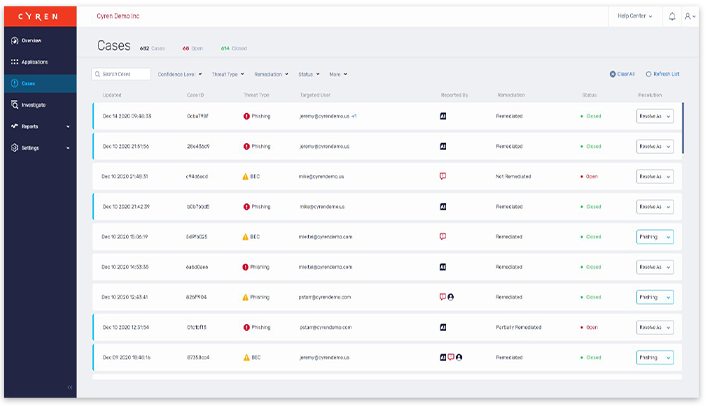
Cyren Inbox Security eliminates the time it takes to investigate and contain phishing threats in users’ mailboxes.
- Continuously scans mailboxes for latent threats
- Groups similar incidents into single cases
- Automated phishing incident response playbooks
- 24x7x365 managed incident response service
Case Study: The Keyes Company
Operating since 1926, The Keyes Company is Florida’s #1 independent brokerage. Still family-owned after 94
years in business, the company provides real estate services to customers in six Florida counties and sales
expertise to clients in several foreign countries.
With 3,500+ agents working across 58 offices, Keyes takes pride in its deep first-hand knowledge of Florida
real estate and commitment to the well-being of its employees, agents, and customers
“We had an email gateway solution in place and were providing email security training, but we were still riddled with phishing scams”
Wendi Iglesias, CIO at The Keyes Company
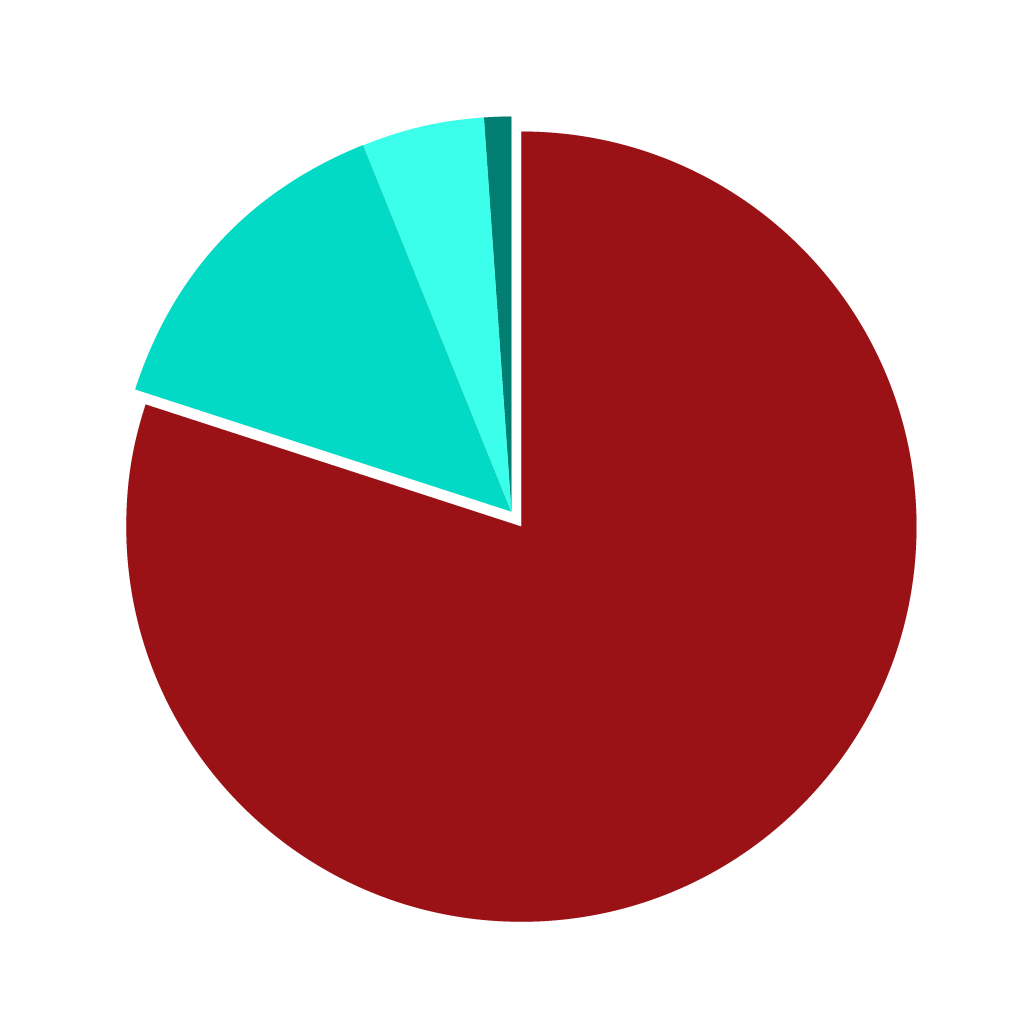
Types of Inbox Threats: 80% Phishing, 14% Spam, 5% BEC, 1% Malware
89% of organizations experienced at least one successful phishing breach during the past 12 months

It takes an average of 175 hours to remediate and recover from a successful breach
You Might Also Find This Interesting
Web Security
Relevant and accurate categorization of URLs to identify web threats like hosts serving malware and other malicious content.
Threat Intelligence
Real-time feeds of the latest malicious files and web hosts connected to active malware campaigns. Enrich incident data and block emerging malware attacks.
Email Security
Integrated solutions to protect your users from the latest malware campaigns and malicious attachments.