A little design in the phishing world
What do bright and catchy presentations, laconic documents, and perfect CVs have in common?
- Everyone can easily create it by using online graphic design platforms without wasting time.
- Almost everyone already knows about such services and have used at least one time before.
For the last several months, the popularity of such platforms is consistently high. According to Alexa.com web-traffic statistics, graphic design and document editing platforms such as “canva.com”, “adobe.com”, “quip.com”, and “joomag.com” are firmly established in the top 10K of global internet traffic scores.
Along with ordinary users, who are using the services mentioned above in their daily routines, phishers also do not stand aside from the modern Internet trends. Creation and distribution of phishing emails through graphic design platforms provide a lot of privileges for intruders and help to avoid detection engines and mailbox filters.
More details about danger of phishing hosted on high Alexa domains you can find following by the link below:
Phishing hosted on high Alexa domains: another dangerous trick in Web
Platform capabilities allow scammers to create and host fake files, which redirect end users to other phishing landing pages aiming to steal personal credentials. To catch multistage phishing attacks like these, security engines should be armed with additional and more sophisticated detection logic. At the same time, it is hard to recognize fake documents for inexperienced users, so they should be on the lookout for not getting hooked.
Steal like an Artist
For the last few months, Cyren Inbox Security users have been exposed to several attacks originating from graphic design platforms. According to our traffic statistics, the most common graphic design and document editing platforms used for phishing distribution are Canva, Quip, and Adobe, which account for 90% of similar phishing transactions. The remaining 10% are divided among Genially, Flipsnack, Bannersnack, and Joomag.
Usually, targeted recipients receive an email with information about missed or unread faxes, emails, or documents. There are presented document or fax details such as sender, dates, reference etc. in the email body. At the bottom of the email there is a clickable hyperlink or button, which the recipient can click to view documents. Once the attractive button is clicked, it takes users to an ordinary fax or document, hosted on services mentioned above, with one more button and request to push on it to view the document. Only after passing all of the ruses and steps above will users reach the cherished phishing page, which requires their credentials or other personal information: O365 account information, bank data, etc. The lifetime of such phishing attacks is short, due to policies of the host-services, but it is enough for the phishers to steal important personal information and use it for malicious and selfish purposes.
A picture is worth a thousand words, let’s review a few examples that Cyren Inbox Security users encountered recently.
- Phishing attack created on “canva.com”
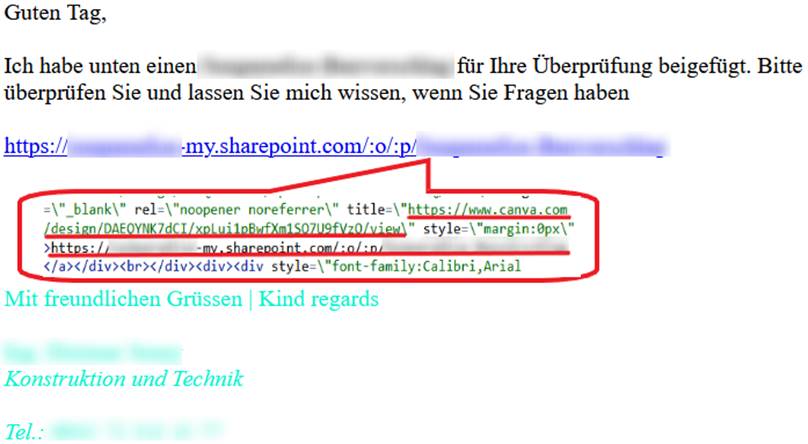
Email body of phishing email detected by Cyren Inbox Security
As was mentioned above, after clicking on the hyperlink, users will see an intermediate page with one more button to view the relevant document.
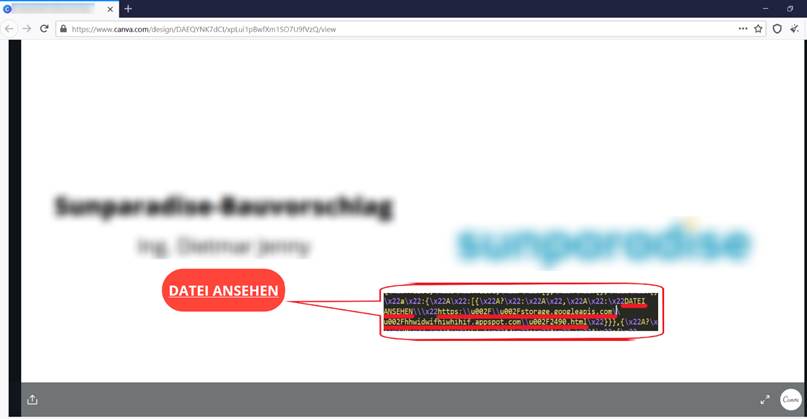
Fake document hosted on “canva.com” : hxxps://www.canva.com/design/DAEQYNK7dCI/xpLui1pBwfXm1SO7U9fVzQ/view
After clicking the “DATEI ANSEHEN” (VIEW FILE) button, the user will be exposed to one more redirect to the phishing landing page, where he/she will then be asked to insert their own credentials or personal data.
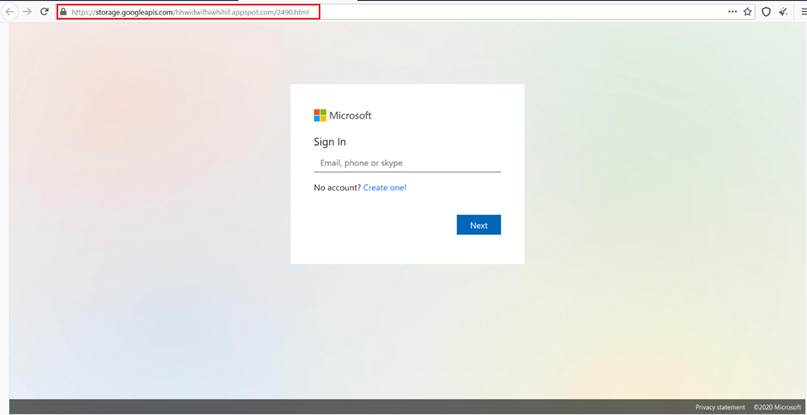
Phishing Microsoft o365 login page: hxxps://storage.googleapis.com/hhwidwifhiwhihif.appspot.com/2490.html
From the example above, the scammer’s target has experienced a long journey to reach the last stage of such sophisticated attack. That means, detection engines should predict and be ready to react and avoid twisty tricks of attackers to protect their users. Unfortunately, because of phishing multistage, it is almost impossible out of the box with your email service provider.
- Phishing attack hosted on “quip.com”
Another, no less refined and difficult-to-detect example of phishing attack was distributed on the platform “quip.com”. Why it is dangerous for users and challenging for detection side? First of all, it is widely used platform for day-to-day business routines. That means it has a huge amount of traffic and processed data. It is difficult to divide into legitimate or not for both sides, due to diversity of the content. So, it is easy for understanding, that such traffic will be ignored by detection tools, and, at the same time, such traffic is highly trustworthy for users themselves.
In this example, the potential victim received an email, which informed him about a shared document. To view the document, the user should click on the hyperlink “02PLANNING|RFI|2020|12|21”.
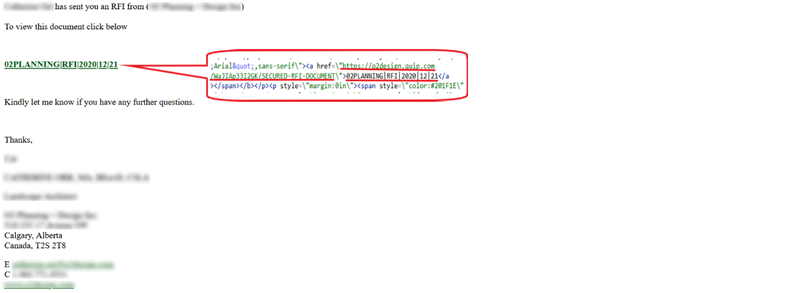
Email body of phishing email detected by Cyren Inbox Security
After the “click”, user will be redirected to the Quip-based document, which contains information about the secured file with an access button and some instructions.
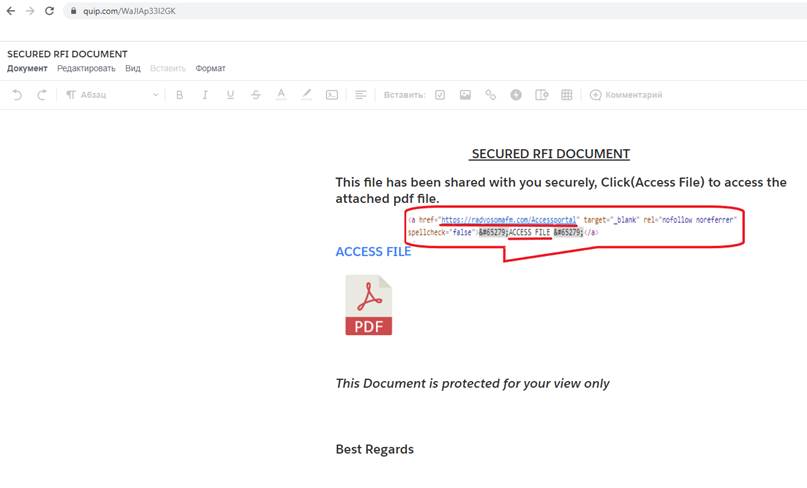
Fake document hosted on “quip.com”: hxxps://quip.com/WaJIAp33I2GK
For inexperienced users, document above could be common-looking and does not arouse any suspicion. But if we are more curious and want to inspect what is hidden under the page, we will find, that “ACCESS FILE” button covers one more redirect. After clicking on the “ACCESS FILE” button, the user will reach final destination and main purpose of Phishers: a spoofed o365 Microsoft login page to capture their credentials.
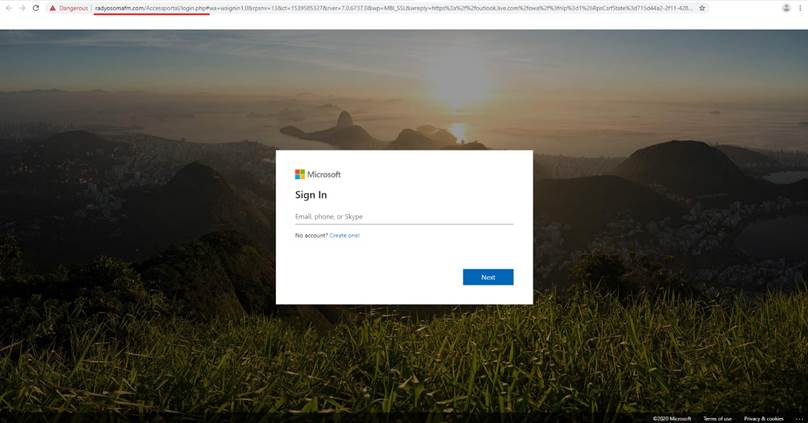
Phishing Microsoft o365 login page: hxxps://radyosomafm.com/Accessportal/login.php#wa= wsignin1.0&rpsnv=13&ct=1539585327&rver=7.0.6737.0&wp=MBI_SSL&wreply= https%3a%2f%2foutlook.live.com%2fowa%2f%3fnlp%3d1%26RpsCsrfState%3d715d44a2-2f11-4282-f625-a066679e96e2&id=292841&CBCXT= out&lw=1&fl=dob%2cflname%2cwld&cobrandid=90015
The successfulness of the attack depends on user awareness and logic compliance of all phishing attack stages, or from reliability and readiness of the security system to react and confront such shenanigans.
How to be a rocket in Cyber Security
Despite these difficulties to detect such artful kinds of attacks based on graphic design and document editing platforms, Cyren Inbox Security’s elaborated logics and detection models using accumulated knowledge base allows us to protect our users without excess noise.