Cyren Threat Intelligence Feeds
Spot cyber attacks before they hit.
Cyren protects 1.3 billion users against emerging threats













Security teams play a constant cat-and-mouse game with rapidly evolving phishing attacks.
Cyren’s Threat Intelligence Feeds provide unique, high-fidelity,
actionable threat intelligence before other vendors.
You get what you pay for
Most threat intelligence vendors purchase data from similar sources before repackaging and selling it. Valuable information gets buried within mountains of old information and false positives.
Cyren’s unique and fresh threat intelligence is gathered by analyzing, processing, and correlating billions of daily transactions across email content, suspicious files, and web traffic to provide timely and accurate insights.
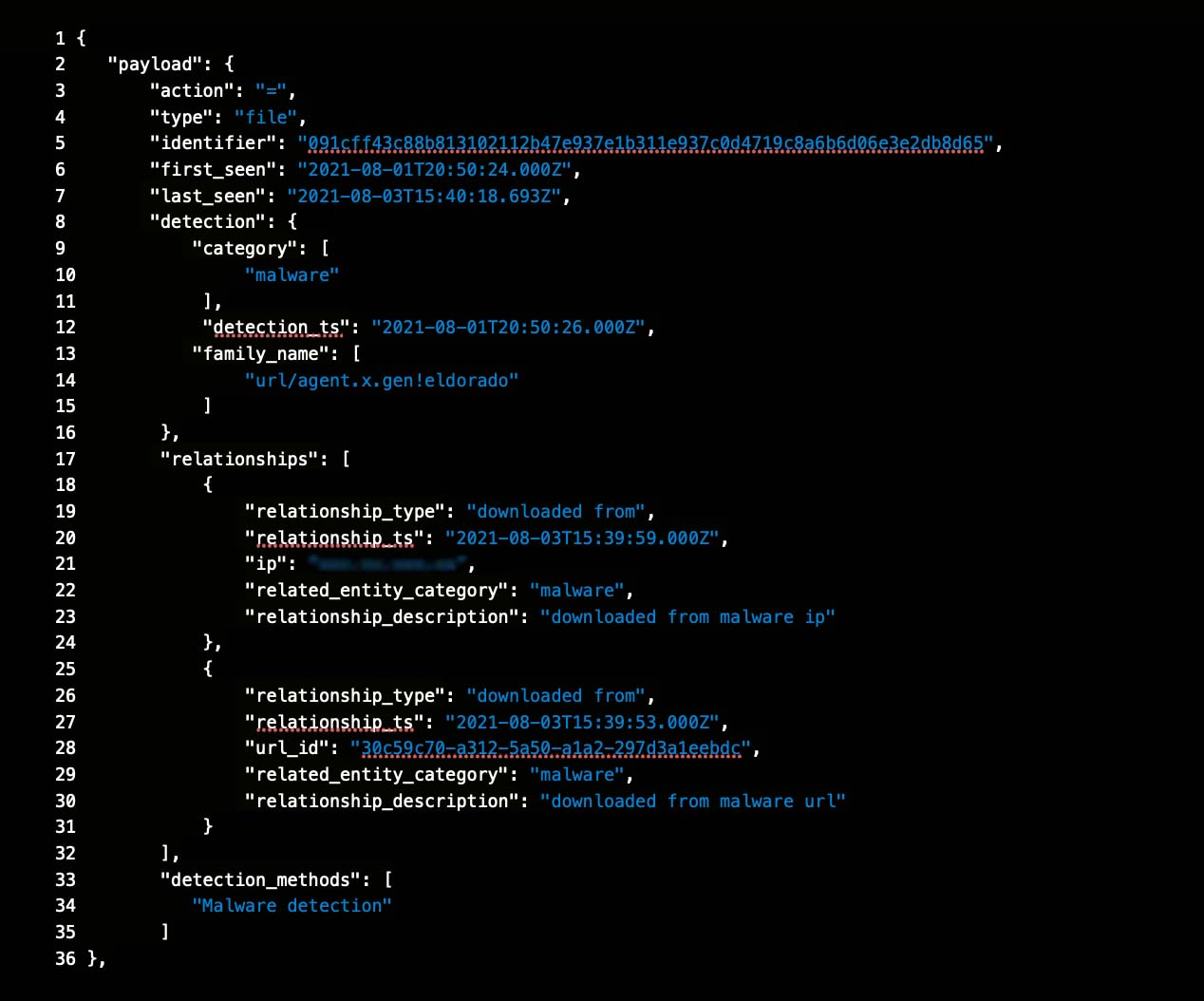
Malware File and URL Intelligence
Real-time information about ongoing and emerging malware threats
Analyze millions of suspicious files to detect hundreds of thousands of new malicious files daily
Contextual information includes malware family and relationships to IP addresses, download URLs, and other IOCs
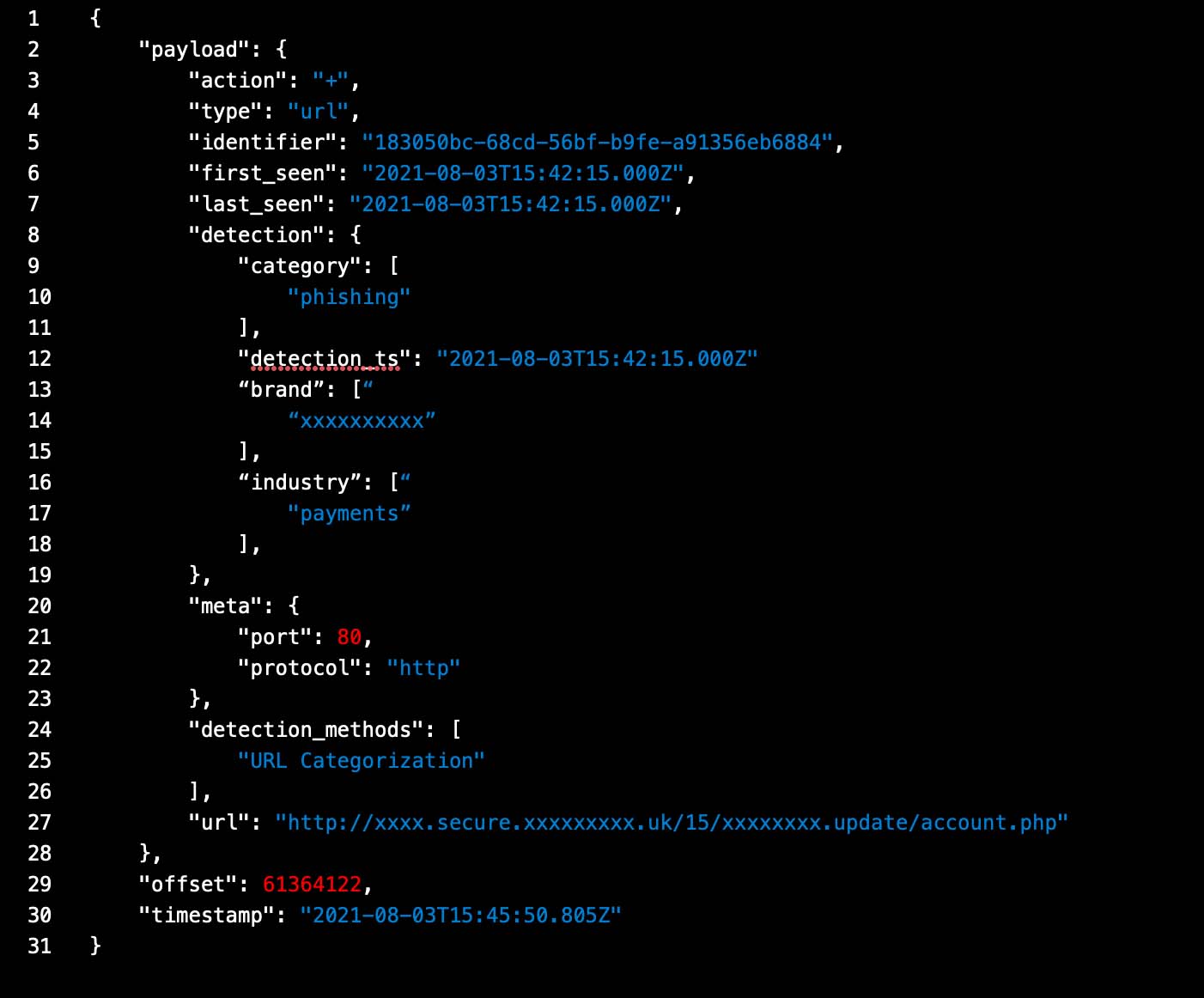
Phishing and Fraud URL Intelligence
Visibility of over 1 Billion URLs each day. Analyze URLs strings and web content to detect zero day and other phishing attacks.
Over 9,000 new phishing URLs per day
Context includes brand and industry information and is correlated to IP addresses that host the pages and files that contain phishing links
IP Intelligence
Analyze billions of web and email transactions in real-time to expose high-risk IP addresses that serve spam, phishing, and malware
Apply unique technologies and algorithms to quickly identify botnets and zombie hosts, and their activity
Contextual information includes threat intensity, risk score, geolocation, and relationships to other threats

A buyer’s guide to actionable email threat intelligence
By providing security analysts with actionable threat intelligence, organizations can better understand – and prevent – threats.