I can’t remember the last time I read the news where I didn’t see a headline that involved a business becoming a victim of cybercrime due to phishing. Both big and small organizations are targets, with CEOs falling victim to “whaling” (phishing targeted at executive staff) as often as regular employees. A recent Osterman Research survey conducted on behalf of Cyren found phishing to be the top threat category for small- to medium-sized businesses (up to 3,000 employees), with 43% suffering a phishing breach in the last 12 months.
The reasons for the dramatic rise in phishing are fairly obvious. Driven by a constant desire to maximize revenue, cybercriminals realize that phishing is a relatively inexpensive way to obtain sensitive personal and financial information that can then be resold on the black market or used directly for monetary gain. The prominent use of PayPal in business transactions, as well as the increase in cloud-based business and productivity tools, such as Google Apps or Microsoft’s Office 365, provide a simple and effective hook for criminals to use in their attempts to lure victims into clicking fake links. Combined with an overall lack of password management at many companies, the likelihood that organizations will be targeted with phishing and ultimately be hacked is increasing dramatically.
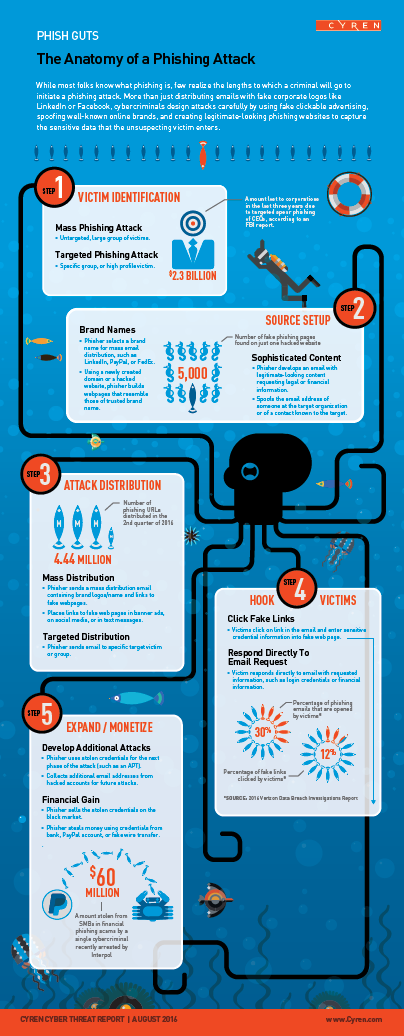
Because Cyren is uniquely positioned to observe, analyze, and halt phishing attacks as they happen, we’ve decided to focus our new quarterly trend report on the topic of phishing. We discuss how phishing happens and why, review the anatomy of a phishing attack (see infographic), provide insight into the mind of a phisher, analyze the level of phishing protection you receive from various browsers, and examine the life cycle of a phishing site. Effective protection against phishing certainly begins with employee education, but the continuing shift to cloud-based services and mobility, and the increasingly sophisticated nature of these phishing attacks, requires innovation in security with the kind of real-time detection and blocking of suspected zero-hour phishing sites Cyren’s security cloud provides.
Download a free, complimentary copy of the full Cyren Cyberthreat Report on phishing.