I recently came across a piece of malware that is being distributed as an email attachment, posing as a PDF document with a fake file name and icon. It seems like a usual executable malware or botnet client being spammed that does its thing when executed, but after looking into it further, I find it very interesting how simply it was written and how it uses some network administration tools to effectively steal users sensitive info from its computer.
The file was received as zip file attachment to an email and inside the zip file, it contained the file named “document.exe” with a fake PDF file icon.
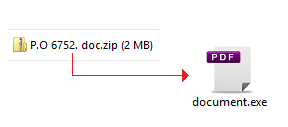
The file “document.exe” is actually a self-extracting RAR file, and this RAR file contains 7 files as shown in the image below:
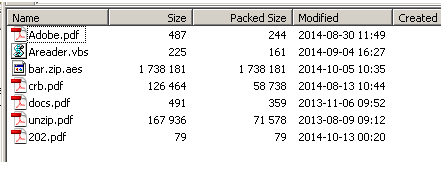
As you can see from the image, the file contains a .vbs script file, an .aes file and a couple of .pdf files, but these .pdf files are actually not real PDF document files. They are just renamed to .pdf files to trick users into thinking that they are not malicious. Each file will be explained as we go along.
Since the “document.exe” file is a self-extracting RAR file, it is able to extract the files automatically and it can also be set to automatically execute or open any of the files after extracting. In this case, when document.exe file is executed, it will extract the files to the folder “C:userspublicPublic DocumentAdobe” and after extracting, it will run the file “Areader.vbs” which is obviously a VBS script file. This vbs file will then rename the file “Adobe.pdf” to “Adobe.bat”, and then opens a command shell to execute the “Adobe.bat” file which is obviously a Windows CMD Batch file. Now that we know that the “Adobe.pdf” file is actually a Batch file, I will go over the rest of the files and explain what they are.
Adobe.pdf – a renamed Windows CMD batch file. It contains the main commands to install this malware to the system.
bar.zip.aes – this is an encrypted zip fils. It contains other files that hold the password-stealing capabilities of this malware.
crb.pdf – a renamed Windows executable file which is actually an AES Encryption/Decryption tool. This is used to decrypt the file “bar.zip.aes”.
docs.pdf – this is a real blank PDF document which will be opened by the batch file.
unzip.pdf – a renamed Windows executable file which is actually the “unzip.exe” tool that is used to unzip the decrypted “bar.zip.aes” file.
202.pdf – this is a renamed text file which contains FTP scripts that is used for uploading stolen data to the malware authors FTP server.
As mentioned, the Adobe.bat batch file will first open the real pdf file 202.pdf, so that users will think that they are opening a real PDF file. But in the background, it installs the malware to the system by first decrypting the file bar.zip.aes using the mentioned AES Encryption/Decryption tool. When decrypted, the contents of the zip file (shown below) will be extracted in the same directory.
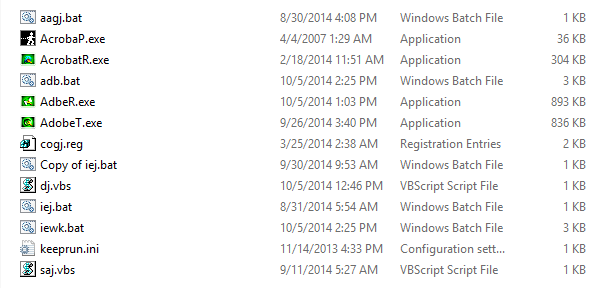
After the files are extracted, the batch file will then call and execute the file “saj.vbs” which will then call the “adb.bat” file. And this “adb.bat” file is the actual script that does the password stealing functions of this malware.
As shown above, there are 4 executable files (.exe), which already look malicious by just looking at their filenames. However, they are not actually malicious but they are some of the Network and System administration forensic tools that can be downloaded from http://securityxploded.com. This is a community based website that focuses on Information Security R & D, and on this site you can find some helpful write-ups, research articles and downloadable tools. These tools are explained as follows:
AcrobatR.exe – this is a command-line base tool called Internet Explorer Password Decryptor Tool. It is used to recover all passwords that has been stored in the Internet Explorer (IE) browser from its Autocomplete and Basic HTTP Authentication.
AdobeT.exe – this is a command-line base tool called Browser Password Dump. Just like the file AcrobatR.exe, but this can now recover passwords stored on different browsers such as IE, Firefox, Google Chrome, etc.
AdbeR.exe – this is a command-line tool called “All-in-One Email Password Recovery Tool. It is used to recover email passwords from popular email and chat applications such as MS Outlook, MS Outlook Express, Thunderbird, MSN Messenger, etc.
AcrobaP.exe – although this is not from the “Securityxploded” website, this is a patched version of the tool called “Keep Running” (keeprun.exe) which is developed by a company called JPElectron. It is a tool that can launch an application and ensures that it stays running. In this case, it uses the configuration file keeprun.ini.
As for the rest of the files:
keeprun.ini – the configuration file for the “Keep Running” (AcrobaP) tool. It is set to make sure that the file “iej.bat” will run every 3600 seconds.
Adb.bat and iewk.bat – These are the same files but just with different file names. As mentioned, these are the main scripts for this malware.
aagj.bat – a batch file that runs the “AcrobaP.exe” and registers the registry file “cogj.reg”.
cogj.reg – a registry file that is used to set the malware to run every time the computer starts. It also changes some email settings.
This registry file will create the following registry entries:
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRun
“stat”=”c:\Docume~1\AllUse~1\Msn\Msn2\aagj.bat”
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun
“stat2″=”c:\Docume~1\AllUse~1\Msn\Msn2\aagj.bat”
These entries will automatically execute the batch file aagj.bat which will then execute the file AcrobaP.exe (Keep Running Tool) to make sure that the malware will execute every 3600 seconds.
dj.vbs – a vbs script file that calls and runs the file “iewk.bat” when executed.
Iej.bat – a Windows CMD batch file that runs the file “dj.vbs”.
Saj.vbs – a vbs script file that calls and runs the file adb.bat.
To continue, when the adb.bat is executed, it will first try to rename all .pdf files to .exe files (e.g. AcrobatR.pdf to AcrobatR.exe). This is because at the end of this script, all .exe files will be renamed to .pdf, thus on the next execution, these .pdf files need to be renamed back to .exe. It will then create the folder “%systemdrive%Documents and SettingsAll UsersMsnMsn2” and copies all the files to it.
It will then run the command “ipconfig /all” and save the output to a text file called adip.klc. This is to get the network info of the infected machine and it will be part of the data to be stolen.
It will then run the file AcrobatR.exe (IE Password Tool) to get all stored IE passwords and stores the output to the text file wmsn.klb.
After getting the IE passwords, it will now run the AdbeR.exe (Email Password Tool)to recover and gather all stored email accounts and passwords and stores the output to the text file amsn.klc.
It then runs the file AdobeT.exe (Browser Password Dump Tool) to get all stored password from all other browsers installed on the system and stores the output to the text file “wmsn.klc”.
Then, output files amsn.klc and adip.klc will be combined into one output file msn.klc. This file now contains the network info and the email accounts with the username and passwords gathered. Lastly, the output files will be uploaded to the malware author’s ftp server. But before that, it will first rename the output files as follows:
“msn.klc” = “001_<current_date>_<current_time>.036” ex. 001_201415We_072944.036
“wmsn.klb” = “001_<current_date>_<current_time>.037” ex. 001_201415We_072947.037
“wmsn.klc” = “001_<current_date>_<current_time>.038” ex. 001_201416Th_080635.038
The contents of the output files will look like this:
- Output file with stolen Email address
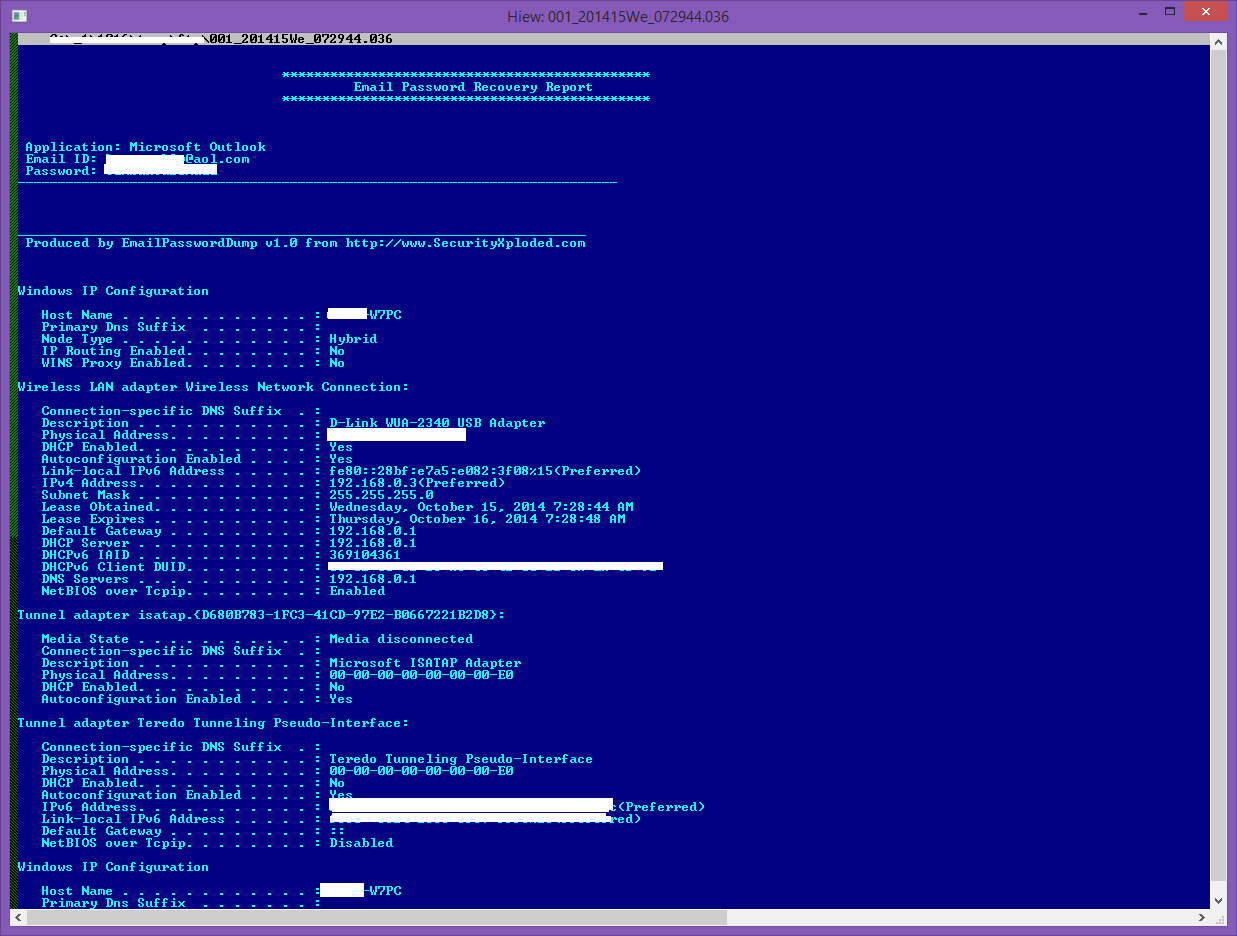
- Output file with stolen passwords from Internet Browsers.
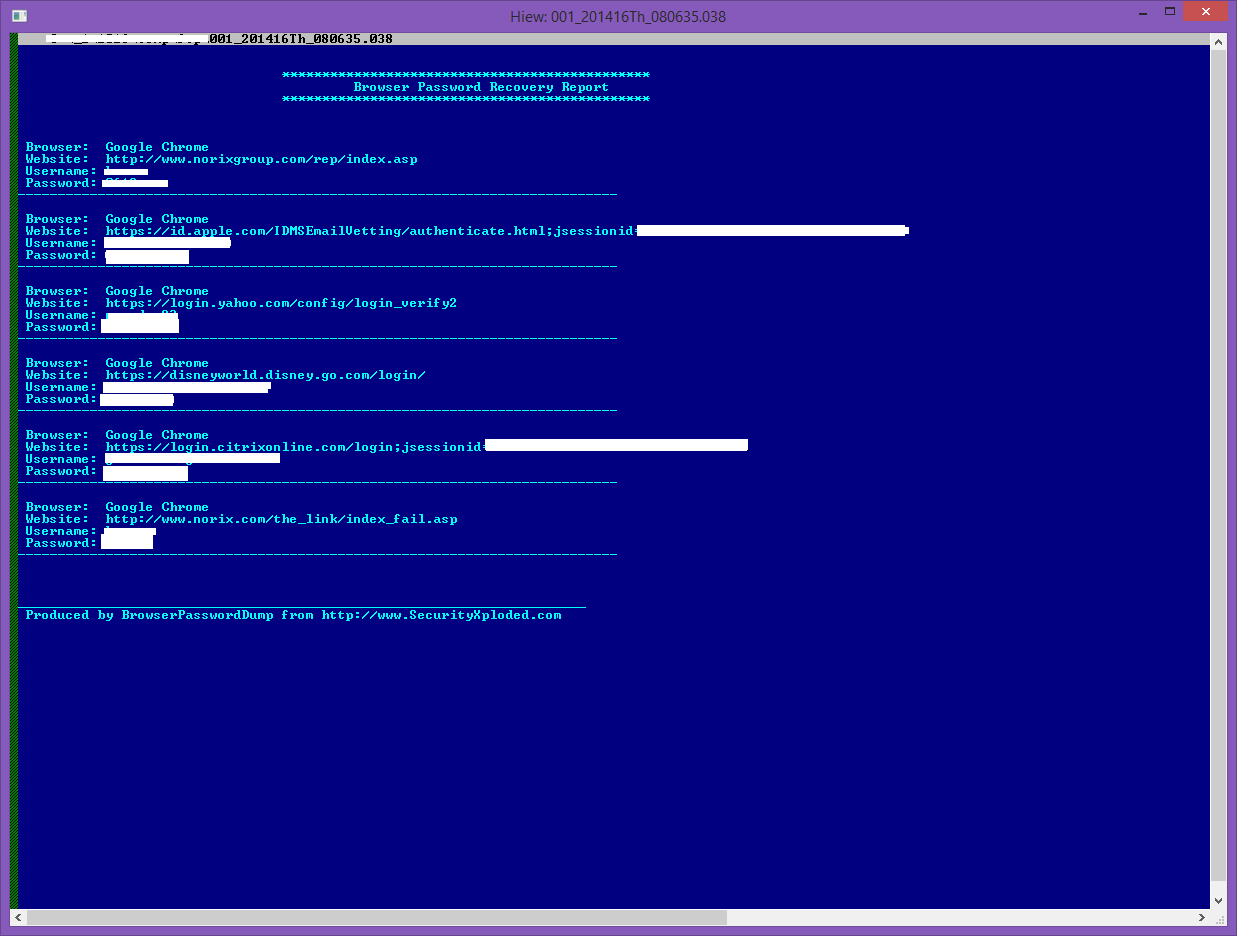
As clearly seen from the above, the user’s Outlook Email account and passwords as well as the user’s accounts on different websites were successfully retrieved by these tools from SecurityXploded and are now ready to be uploaded to the malware author’s FTP site.
Finally, these files will be uploaded to an FTP site being hosted from freehostia.com. And to do this, the malware will just use the FTP script file contained in the file 202.pdf mentioned earlier. I tried accessing the said FTP server and found hundreds of these files in there.
To summarize, with the readily available and easy access to these so-called Network Admin / Forensic Tools, and by just using simple scripts, anyone with malicious intent will be able to easily steal any users Email and Website accounts and passwords.
CYREN Inc.’s AntiMalware scanner engine detects these malicious scripts and tools as:
Password Stealing Trojan VBS/SecXploded.A and BAT/SecXploded.A and Security Risk Tool W32/SecXploded.A.