Android Malware “GhostPush”
Already discovered packaged into 39 different Android apps, “GhostPush” (sometimes also called “Rootnik”) malware turns an infected device into a platform for the installation of adware, unwanted homescreen links, and further malware. Victims have found the malware to be deeply entrenched and difficult to remove.

Malicious Code via Popular Flashlight App
The malicious code is initially installed when the Android user downloads an infected version of a popular application, such as a flashlight app or a popular game from a 3rd party app store.
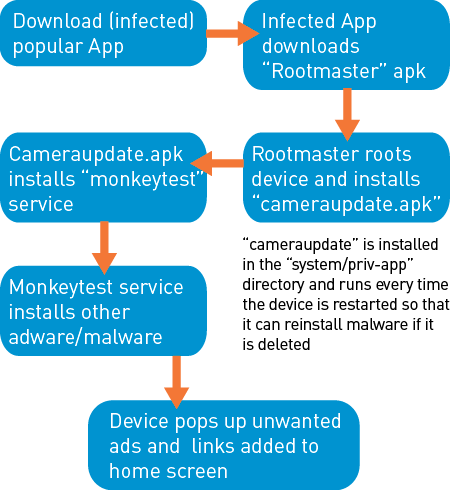
While the infected app is functional, it also gathers information about the host device and sends it to a command and control (C&C) server. The server then replies by sending an Android Application Package (.apk) file tailored to root the specific device type. After rooting the device, the malware replaces and modifies system files and installs a malicious service called cameraupdate.apk into the root system folder (“system/priv-app”). Installation files present in the “priv-app” directory are run every time the device starts. In this way, the malware can reinstall itself if removed, ultimately making it very hard to uninstall.
A Service Called “MonkeyTest”
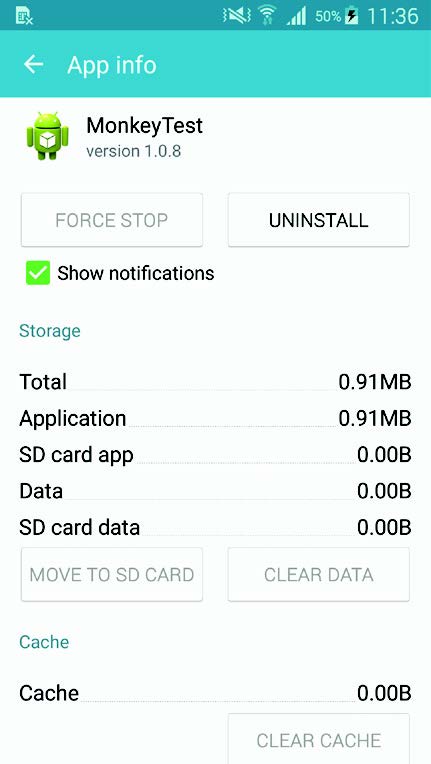
Cameraupdate.apk then installs a service called “MonkeyTest” (other names, such as TimeService, might also be used). MonkeyTest is able to install unknown applications (primarily adware-related) without the user’s knowledge, turn off WIFI, and use the mobile data to download other malicious applications, potentially costing the victim excessive amounts in data charges. The malware also drains the battery and slows the device. MonkeyTest gathers device information, such as the International Mobile Station Equipment Identity (IMEI), International Mobile Subscriber Identity (IMSI), and app packages installed.
Malware Originates from Non-GooglePlay Store Sources
Based on the code and app signatures, CYREN believes the source of the malware to be China. GhostPush is detected by CYREN as AndroidOS/Rootnik.A.gen!Eldorado. As the malware originates from non-GooglePlay store sources, we once again caution users about downloading apps that require enabling the “Unknown Sources” check box.
This infographic summarizes the whole GhostPush procedure:
Further information on malware detection can be found in CYREN’s Q3 Cyber Threat Report.