With tremendous money to be made in a short period of time, phishing has become commonplace within the cryptocurrency exchange world, particularly at the moment when a new currency comes along and debuts with its initial coin offering (ICO), an event not unlike an initial public offering with corporate stock. Initial coin offerings are happening with frequency as there are now over 1,200 (and counting) cryptocurrencies out there. Phishers are exploiting the ICO frenzy by first hacking into these participant email databases and then sending phishing emails to ICO participants, with instructions to deposit funds into the phisher’s cryptocurrency account.
One new case came to light on Wednesday, January 31, when the startup currency BEE found itself the focus of a tried and true criminal attack—its email database appears to have been hacked (although BEE has not officially confirmed this), and over 600 auction participants were duped into sending over $1 million to the phisher. This is one-third of the amount of actual tokens sold by BEE thus far.
Stampede Them When Pandemonium Hits
This “phish” has the social engineering elements of many successful phishing attacks, but of particular note is the timing of the phish, which applied the principle of attacking victims when they are hurried, distracted, or under duress. The phishers timed their emails to coincide with the start of the ICO auction, which is a moment when participants are looking to move extremely quickly.
Many currency speculators are drawn to Initial Coin Offerings as they allow buyers to scoop up new coins at typically lower prices before they hit exchanges. Coins often debut on cryptocurrency exchanges at 2 or even 10 times the paid ICO price. This type of return on investment has resulted in popular ICOs selling out within minutes, creating a buying pandemonium at the ICO start time.
The process of purchasing an ICO involves sending existing cryptocurrency (such as Ethereum (ETH) or Bitcoin (BTC)) to an ICO address or “wallet” held by the company running the ICO. To prevent early cryptocurrency purchasing, until the time of the ICO the address is often a closely guarded secret, being revealed with much fanfare and countdown timers at the ICO time.
To join an ICO, interested buyers typically need to sign up and provide at least an email address. But in most cases, the cryptocurrency company also requests extensive personal data (such as birthdate, address, phone number, and pictures of photo-ID) in order to comply with anti-money laundering requirements. These databases of confidential information have proven to be quite hackable as some of the companies are evidently not prioritizing or lack the resources to implement significant security.
Phishers Offered Better Terms
This scenario played out Wednesday, January 31st during the ICO crowdsale for BEE token. Aware of the potential for their database to be hacked and the possibility of preemptive phishing emails sent with fake ICO addresses, the BEE team posted the contribution address along with a video of their CEO reading and displaying the address.
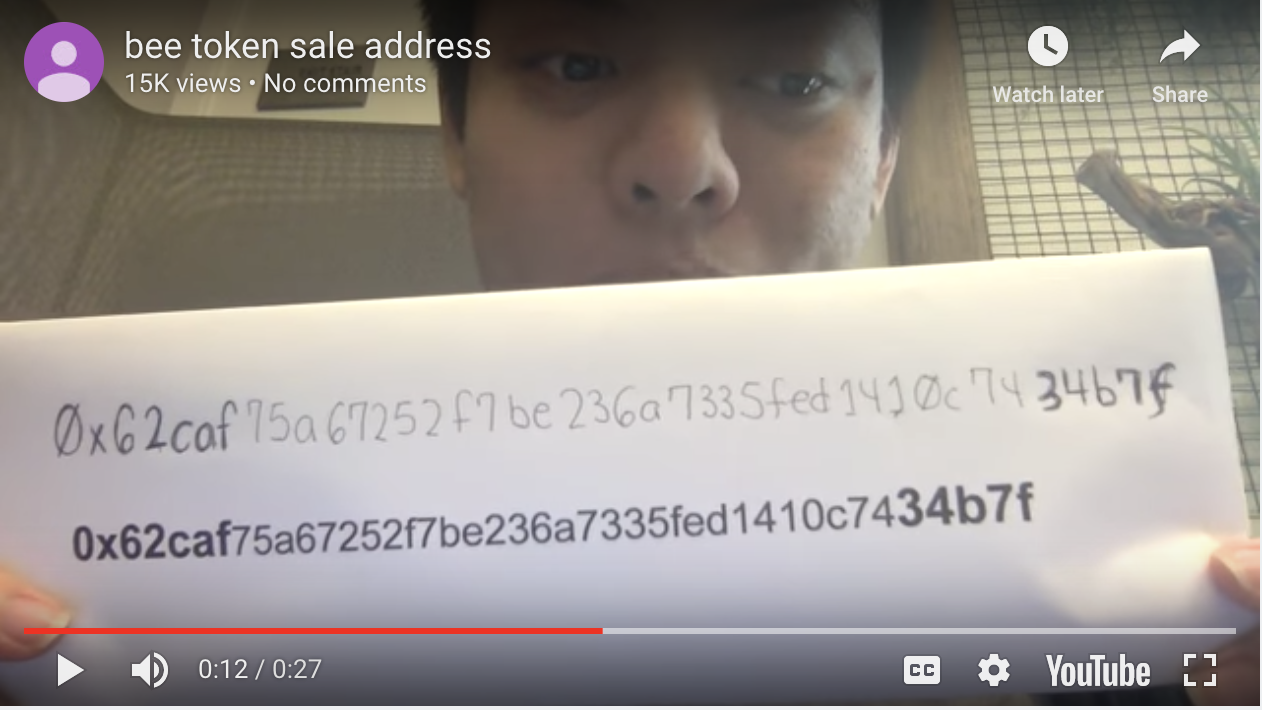 BEE CEO video warning potential ICO participants to only use the funding address on the screen.
BEE CEO video warning potential ICO participants to only use the funding address on the screen.
However, it seems that the BEE database had already been hacked and emails were already on the way to all BEE ICO participants as the ICO was about to commence.

Image of fake phishing email sent to cryptocurrency auction participants
The rules of the official BEE ICO crowdsale stipulated relatively low contribution limits of up to 0.2 ETH (about $210). This number was criticized as too small by most investors. The phishers promised much higher contribution limits (over 104 ETH), a new partnership with Microsoft, and a 100% bonus to purchasers. Many buyers were obviously swept along by the better terms, failing to apply the “too good to be true” rule. And of course the wallet address provided in the phishing email was not the real BEE address, but instead belonged to the phishers.
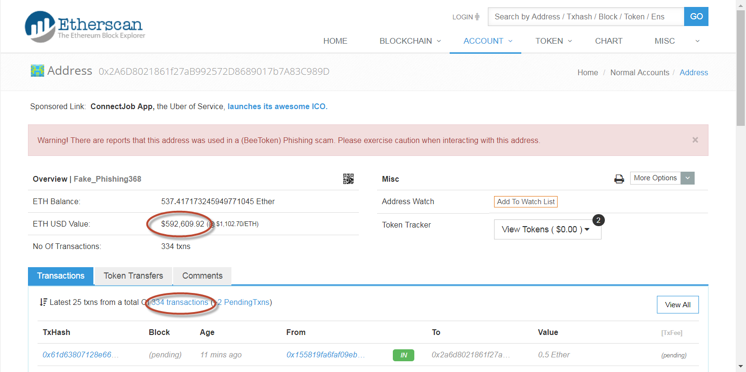
A review of funding addresses belonging to phishers shows tremendous financial gains from the BEE ICO hack.
According to Etherscan, the scam Ethereum account address included in the phishing email revealed nearly $600,000 in deposits from 334 transactions, with new victims continuing to deposit funds. Other fake addresses have also been reported with the BEE token phishing total now exceeding one million USD from over 600 victims.
Hacking, phishing, and cryptocurrency are three words that are increasingly converging. If you are thinking of investing in an existing or new cryptocurrency, remember to be wary of any emails purporting to come from that cryptocurrency company. Visit our phishing resource page for an overview of the phishing threat.