Movie and TV watchers who download pirated content have long been warned of the potential for malware that might accompany their chosen media. Now use is again being made of Digital Rights Management (DRM) functionality — designed to prevent piracy — to distribute malware.
The new attack, brought to Cyren’s attention by security researcher Amitay Dan, abuses a DRM popup message function that is built into Windows Media Player.
In normal legitimate operation the feature works like this:
- A content provider embeds an authorization URL in their DRM protected content that will be displayed in the Media Player window, to allow the user to acquire a license to play the content
- A content user opens (the legitimately downloaded) content in Media Player
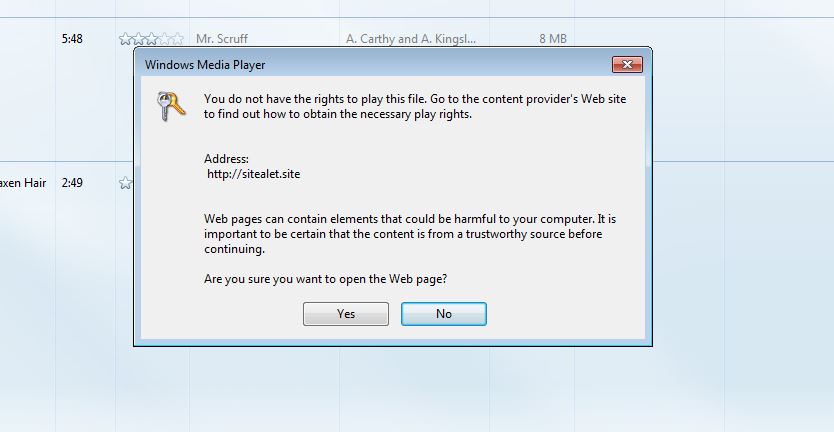
- Media Player pops up a message “You do not have rights to play this file” along with the authorization URL and a security warning.
- The user needs to click on “OK” to open a window to the authorization URL, so that the user can enter credentials or pay to acquire the content
- The content owner authorizes the content and the content user can now watch/listen to the legitimate content
The abuse of this DRM link functionality was first reported over 10 years ago (and it resurfaces every few years) – but it appears that the threat is little known and is now being used once again. The malware version goes like this:
- User downloads infected media – in this case “War-Dogs-2016-720p-BrRip-x264-SiNNERS”. In this case the media was downloaded using BitTorrent – but could come from any download source.
- When the .wmv file is opened in Media Player the DRM warning message pops up listing the URL of the malware distributors
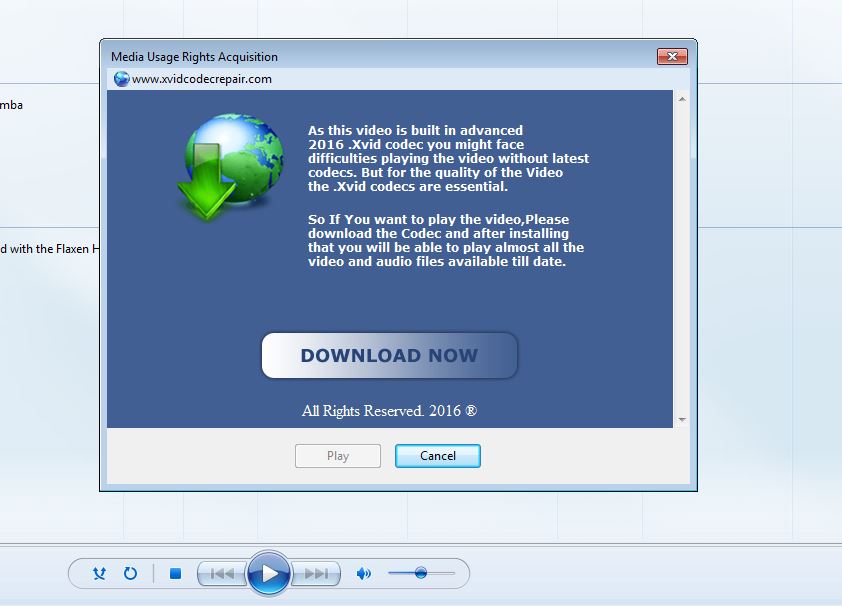
- Clicking on “Yes” opens up a similar small window, this time showing content created by the malware distributors with the message (given verbatim here), ”As this video is built in advanced 2016 .Xvid codec you might face difficulties playing the video without latest codecs. But for the quality of the Video the .Xvid codecs are essential. So If You want to play the video, Please download the Codec and after installing that you will be able to play almost all the video and audio files available till date.”
- As shown, the window for “xvidcodecrepair.com” includes a prominent “Download Now” button. Clicking on “Download Now” results in download of an executable file “codecfix.exe”. Codecfix.exe is detected by Cyren as dropper/downloader malware. In addition to installing the dropper, the process also retrieves the latest Divx install — from the legitimate Divx servers — and starts a real Divx install, apparently to give the victim the impression that an actual codec is being installed.