Business Email Compromise (BEC) – also known as email account compromise (EAC) – is a type of phishing or social engineering attack intended to scam organizations out of money through the impersonation of executives.
Business Email Compromise Scams (BEC) Techniques
How does BEC work? The most effective BEC campaigns begin when criminals gain access to your corporate systems via a spear-phishing attack or malware design to steal login credentials. The criminal then researches the organization’s vendors, finance systems, and the executive’s email style and schedule. Often when the executive is away, the criminals send a fake email from the executive to a targeted employee (usually in finance), with a request for an immediate wire transfer to a trusted vendor. However, the wire transfer is, in actuality, directed to an account controlled by a criminal group.
Since BEC attacks heavily rely on social engineering, they can be executed with a few tools and tradecraft. Since these techniques are accessible and repeatable, BEC is a very popular tactic among attackers. Here are the most common types of BEC attack techniques:
Mimicking Email Accounts and Websites
Slight variations to legitimate addresses ([email protected] vs. [email protected]) fool victims into thinking fake accounts are real – also called typo squatting. These could not only trick a user into thinking the email is coming from a popular company, but also from their own company.
Replicating Common Workflows
An endless number of business workflows are executed on a daily basis by organizations and its employees. These typically rely on automation and are conducted over email. The more employees are exposed to these workflows, the quicker they typically execute tasks from muscle memory. Business email compromise attacks attempt to replicate these day-to-day workflows so victims act before they think.
Compromised common workflows include:
- Password reset request
- Sharing files and spreadsheets
- Commonly used apps asking for users to grant them access
Spearphishing
A spear phishing attack is when an email is believed to be coming from a trusted sender. They then use this trust to prompt victims to reveal confidential information, such as credit card information, to BEC perpetrators. This can pose a massive problem because, with credit card or banking logins, much financial damage can be done to single users, as well as enterprises.
Malware Attacks
Malware is used to infiltrate networks so they can gain access to internal data and systems. Typically, that internal data is emails regarding the finances of the company. Once this information is retrieved, it is then used to submit fraudulent wire transfers. Malware also allows criminals to gain access to victim’s sensitive data to expose and/or encrypt it with ransomware.
Types of BEC Scams
Though BEC makes up a small amount of all phishing attacks, it has caused a significant amount of losses. While these attacks have been known as those of a financial nature, they often exceed just that. This could include interruption to business, loss of data, reduced productivity, regulatory fines, as well as brand damage.
CEO Fraud
Attackers are known to sometimes pose as the CEO or executive of a company and send emails to employees in finance. The fraudsters then request that the employees transfer money to an account that the attackers control. This could also be an email to an employee from another department that may be tricked because they trust an email coming “from the CEO”.
Account Compromise
Account compromise occurs when executives’ or employees’ email accounts are accessed by an unauthorized individual, often as a result of credentials exposed by a previous targeted phishing campaign. This access is then used to request invoice payments to vendors listed in their email contacts. Afterward, the payments are sent to fraudulent bank accounts. This not only damages the vendors financially but can ruin the reputation of the company itself.
Attorney Impersonation
Attackers have also been known to impersonate lawyers or other representatives from law firms responsible for sensitive matters. This type of attack often occurs through email or phone, during the end of the business day when the victims do not question the validity of the communication.
Data Theft
HR and bookkeeping employees are often targeted to obtain personal or otherwise sensitive information about the employees or executives. This data can then be used for future attacks.
How Do BEC Attacks Work?
In BEC attacks, attackers pose as someone the recipient likely trusts—this is typically a colleague, boss, or vendor. The sender will then ask the recipient to make a wire transfer, change banking details, divert payroll or something else.
1. Email List Targeting
The criminals begin their attack by building a large list of targeted email accounts. Common tactics for this include scraping Linkedin profiles, mining business email databases, purchases lists on the dark web, or even going through various websites in search of contact information.
2. Attack Launched
Attackers start sending out mass emails as they begin rolling out their BEC attacks. It’s hard to identify malicious intent at this stage because attackers will utilize tactics like spoofing, mimicking domains, and using fake email names.
3. Social Engineering
At this stage in a BEC scam, attackers impersonate individuals within a company. This could include CEOs or other individuals within a finance department. It’s common that these emails will request urgent responses.
4. Financial Gain
If attackers can build trust with an individual successfully, this is the phase where financial gain or data breach is made.
| TYPICAL BEC ATTACK
STEP 1: Research a target company’s organization structure using online resources. STEP 2: Send an email impersonating a manager with a request to make changes to payment details. STEP 3: Use a disposable free email account to receive replies in hope that a victim will respond. STEP 4: Build trust and gather additional information to enable more sophisticated attacks. |
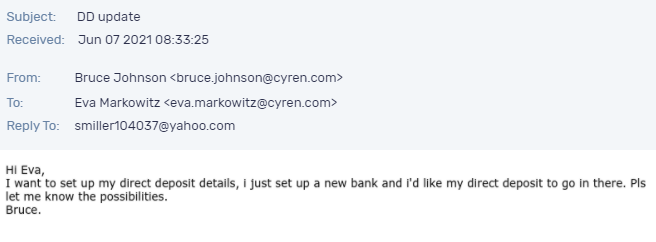
Figure 1. An example of a BEC attack received (and blocked) by Cyren. |
How to Protect Yourself from Business Email Compromise (BEC) Attacks
While BEC attacks can sometimes involve malware, most utilize social engineering techniques. Unfortunately, when social engineering is involved, antivirus, spam filters, and email whitelisting are ineffective. The most useful thing that you can do is decrease the time it takes to recognize and eliminate BEC emails in users’ mailboxes. Educate your employees but recognize and deploy inbox detection and response solutions to automate the detection and management of this threat—this is especially important for frontline staff who are the most likely to receive initial phishing attempts. Below are some strategies for self-protection that your business can employ:
- Adaptive Warning Banners: Flagging emails from sender domains that are similar to your company email or otherwise have indicators of spoofing can help alert users to possible threats.
- Email Rules: It’s important to also flag email communications where the “reply” e-mail address is different from the “from” email address (Figure 1).
- Color Coding: Color coding your virtual correspondence by making emails from employee/internal accounts one color and e-mails from non-employee/external accounts another is a simple way to help users spot basic BEC attempts.
- Payment Verification: Require additional two-factor authentication or some other dual-control on changes to account information or financial transactions above a cetain threshold.
- Confirmation Requests: Confirmations may require that company directory numbers are used, as opposed to numbers provided in an email. You will also want to verify payment and purchase requests in person if possible, or even by calling to make sure it is legitimate. You should verify any change in an account number, or payment procedures, with the person that is making the request. Of course, this requires people to always do the right thing so expect that this control will eventually fail.
- Careful Scrutiny: Deploy next generation detection solutions that continuously examine all email addresses, URLs, and spelling used in correspondences. Scammers typically use slight differences to trick the eye and gain your trust. Do not click anything in an unsolicited email or text message, especially when they are asking you to update or verify account information. You can also look up the company’s phone number on your own. You will want to make sure not to use the one a potential scammer is providing. Then, call that company to ask if the request is legitimate.
- Online & Social Sharing: Be careful with the information you share online and on social media. Openly sharing things such as birthday dates can give a scammer the information they need to guess your passwords or to answer your security questions.
- Be Careful What You Download: Always be wary of email attachments forwarded to you.
Final Thoughts
Phishing emails, and BEC attacks in particular, are built to purposefully impersonate someone your user’s trust – tricking them into sending money, financial credentials, or other personal information. Unfortunately, the sophistication of these attacks helps them to avoid perimeter detection.
Learn more about Cyren Inbox Security for 365, and how it can help your business avoid BEC attacks.