Do you keep seeing phishing emails getting through to users, and wish you could quantify how effective your email security is—or isn’t?
Email is the main vehicle for introducing malware into an organization, and is practically synonymous with phishing these days, so it is a sensible idea to get a grasp on whether your security is doing its job well or poorly — but lots of people don’t. Here at Cyren we know how eye-opening such an evaluation can be, as the email security “gap analyses” that we performed for a series of organizations in 2018 showed that an average 7.2% of email protected by a number of email security products, but still reaching users, was spam or contained a threat.
How to find out: Do a Gap Analysis
Cyren has been helping organizations assess their email security in the only way that is effective—real-life, live testing—and we’ve now expanded the availability of the free service. The Cyren Email Security Gap Analysis assessment is a non-intrusive mechanism for evaluating an existing email security infrastructure. In 2018 we ran Gap Analysis tests with a number of companies and processed a total of 2.7 million emails. These had all been scanned by the in-place email security solution, were considered clean, and were delivered to users. We found that 6.9% were spam, which is an annoyance for users, but of greater concern was the number of phishing (7,014 emails) and malware threats (978 emails) reaching users. Even though only a small percentage of total email delivered is malicious, considering the tremendous volume of email at any organization, having hundreds or thousands of malicious emails getting through is not really an acceptable risk—and is certainly something you should try to get a handle on.
We’ve made available a full report with aggregated email security assessment results from the 2018 statistics, or feel free to visit our Gap Analysis web page or download our Gap Analysis data sheet for more information on having your own test done.
Your Mileage Will Vary
While the average statistics cited above are a useful rule-of-thumb, one key takeaway from our studies is that the results vary considerably, and that several factors influence email security performance at any given organization, as the chart below illustrates (taken from the gap analysis report linked above):
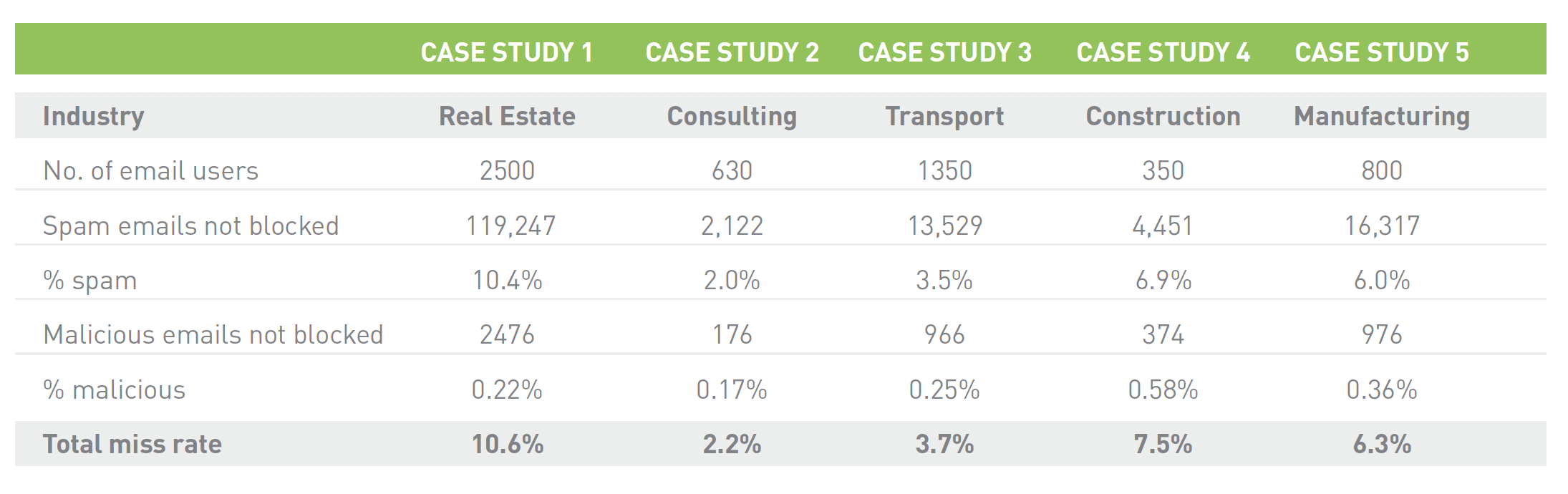
Results in the past have even varied when organizations have essentially the same secure email gateway vendor or hosted email service, as real-world factors influence performance. The bottom line: Do your own gap analysis to understand your own situation.
What You Don’t Know Can Hurt You
Many IT security professionals assume their email security is performing reasonably enough, until a user reports (or several…) that he has received a phishing email or his endpoint protection has detected a threat. Worse, of course, is when your security incident and event management (SIEM), endpoint detection and response (EDR) or data loss prevention (DLP) solutions alert you that your network has been breached. (Which is pretty common—according to Osterman Research, 70 percent of all organizations, and 78 percent of all organizations using Office 365, suffered a successful attack of some kind last year.) That is if you are lucky enough to have the budget for this type of defense-in-depth, and the people to make sense of all the alerts and respond to them.
If you are among the lucky minority that hasn’t seen an attack recently, and assume that your email security is just fine because an attack has not been discovered, do keep in mind the statistics that indicate that 25% of breaches remain undiscovered for a month, during which time the bad guys are helping themselves to your sensitive data.
Email security got “commodotized” and industry lost focus
Is the email security industry doing enough to protect organizations, their employees and information, or have many of the players in this space become complacent? Recent successful, high-profile ransomware attacks suggest the latter, but how did we get here?
Just over a decade ago, the email security industry was growing, buoyant and ready for a spate of acquisitions. Larger information security vendors, wanting to broaden their portfolios, acquired many of the appliance and SaaS companies.
The major change in the industry came when, to add protection to their services, the largest hosted email providers acquired some of the larger email security SaaS providers. They integrated the technologies, and because of the scale of these businesses, they were able to offer the security element at a fraction of the then-current market price. The upshot was that email security quickly became a commodity.
Around the same time, email threats were well understood and under control, so vendors, no longer able to realize much of a monetary return from email security, moved their innovation efforts and R&D budget elsewhere. Many security vendors shifted focus to other, higher growth security technologies, and the few remaining pure-play email security SaaS companies switched to complementary higher-value services, such as email archiving.
Paying the price for lack of security investment
This brings us back to present day, where this lack of investment is obvious. The world has changed and cyber criminals have found easy, low-risk ways of monetizing attacks through ransomware and phishing. Every week there are reports of another successful attack, and these are just the ones that are discovered and reported. The malware authors and attackers are constantly evolving their evasion techniques to try to beat even the most sophisticated defenses, and traditional email security infrastructures have been struggling to keep up—with evident consequences.
Want to learn more about cloud-based email security and archiving? Contact us here!