This isn’t a story of Halloween costumes and candy. It’s a story about a cyberattack in which the victim always pays for the trick. This type of story almost never has a happy ending.
What is Ransomware?
Ransomware is a type of malicious software that uses encryption to hold a targeted victim’s information at ransom. Over the last few years, this type of cyberattack has become increasingly popular despite the complexity of its implementation. To execute a ransomware attack, the fraudster needs to be proficient in many areas, from social engineering through cryptography to programming.
Ransomware is one of the most dangerous cyberattacks today and it always entails a loss of money or data. You may have heard of the recent high-profile ransomware cyberattacks known as Petya or WannaCry. Both give a very accurate idea of the scale and damage involved.
Ransomware, Step by Step
As already mentioned, ransomware is an evasive cyberattack that requires advanced skills to be executed. Such attacks are well prepared not just technically – they also use principles of social engineering.
A ransomware attack is much like a delectable cake with orange-flavored base layer, creamy chocolate frosting and a cherry on top. Let’s disassemble the cake to analyze its ingredients. To do this, we will use the data of a recently attempted ransomware attack that was prevented by Cyren Inbox Security.
A malicious email was sent from an external webmail domain, gmail.com. The short, one-word subject line (“docs”) indicates that the attachment includes a document.
Indeed, the email had a zip attachment: that’s our cake’s base layer. The file was denoted by Cyren’s malware detection engine as JS/Ransom.O!Eldorado JavaScript; this type of file executes a PowerShell command, which uses a link to download the ransomware and execute it. The script is highly obfuscated, with lots of meaningless, randomly generated words, making the trick harder to detect, which is even more dangerous to the user. Clearly, the cake’s base layer wasn’t orange flavored – rather, it was well spiced.
The JS/Ransom.O!Eldorado JavaScript program was supposed to download the chocolate frosting: a so-called Buran ransomware detected as W32/FakeAlert.DX.gen!Eldorado. When run on the user’s computer, Buran goes through files and folders, encrypting them and adding an extension.
Once data is encrypted successfully, the ransomware drops a .txt note, the cherry on top:
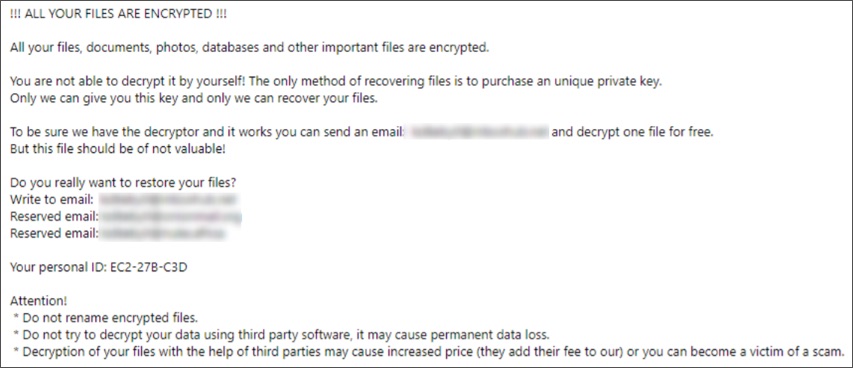
Predictably, the victim would only have two choices: pay the ransom or have the cake and put up with the data loss.
Detected and Protected by Cyren Inbox Security
Fortunately, Cyren Inbox Security was able to scan and automatically detect this suspicious evasive attack. Our 24×7 Incident Response Service immediately investigated all incoming and received emails and confirmed them as malicious for all Cyren Inbox Security customers.
