The Cyren Incident and Response research team continuously collects phishing data and identifies the most effective phishing attacks using Cyren Inbox Security (CIS), the company’s flagship Inbox Detection and Response* solution. CIS directly connects to Office 365, continuously detecting and automatically capturing phishing attacks that evade secure email gateways and arrive in a user’s inbox. This data provides insights about the scale and nature of evasive and targeted phishing threats, and why phishing continues to be a problem for many organizations despite investments in email security best practices and security awareness training.
In July, the Incident and Response team identified nearly 20,000 confirmed email threats, which contained malicious content, and defied detection by third-party email security engines and the native security capabilities of Office 365. Key takeaways include:
- Phishing continues to be the predominant email threat arriving in users’ mailboxes. Ransomware and business email compromise attacks are costly, but the data clearly illustrated that they are symptoms of previous successful phishing attacks.
- 93% contained phishing URLs
- 4% were business email compromise (BEC) or impostor emails
- 3% of messages included a malware attachment
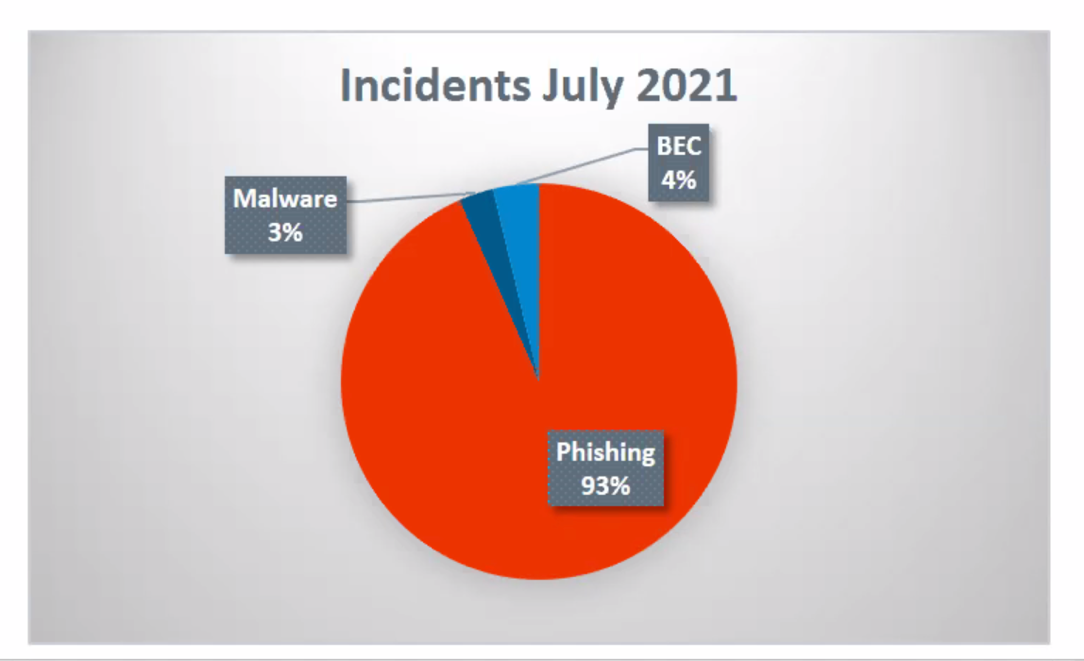
Figure 1
Types of email threats beyond the SEG
- Specialized detection and automated incident response are critical to eliminating threats before risky users do something they shouldn’t.
- 97% of confirmed malicious incidents were detected before users read the messages.
- 94% of evasive threats were detected by Cyren’s specialized engines and threat intelligence rather than helpdesk or SOC analysts.
- Threat intelligence is important but real-time analysis is critical for detecting evasive and zero-day email threats.
- 88% of evasive threats were detected with real-time techniques like machine learning.
- 6% were netted with proprietary threat intelligence or readily matched patterns of previous attacks (heuristics).
- The remaining 6% were suspicious messages that required human analysis to confirm the detection
- User education matters but organizations must put it to good use, especially since most employees think phishing is IT’s problem to solve. Providing the users with a tool for ad-hoc scans of emails before submitting them to the helpdesk/SOC greatly reduces the volume of phishing alerts.
- 6% of total of confirmed phishing threats were triaged by end users rather than bogging down helpdesk or SOC personnel with basic or initial analysis.
- Of the messages submitted to the IDR platform, less than 2% were false positives.
Phishing Attack of Note
From July 16-17, Cyren’s Incident and Response analysts noticed an attack that affected 192 users across 16 of our customers but with a few hallmarks of a highly targeted effort. This shows that some attackers have refined their tactics so they can automate attacks that used to require a high amount of manual effort.
- The sender’s name was spoofed and varied based on the target company. This is a typical trick used to associate the sender with an entity the users are likely to trust.
- The email subject related to an incoming voicemail. Again, this is typical. Phishing email subjects tend to mention voice messages, shipments, invoices, password resets, etc. – anything that creates some urgency but is also in keeping with our digital, mid-pandemic lives.
- There was no body text, just an attachment containing javascript. Criminals are increasingly putting phishing URLs or javascript in files to avoid the time of click protection offered by the SEG.
- The attachment contained code that would open an Office 365 phishing page that displayed the target company’s logo and pre-completed the login form with the user’s email address. The fact that attackers were able to customize the look of the phishing page for each company is not something we see every day, at least not for an attack targeting so many companies at once.
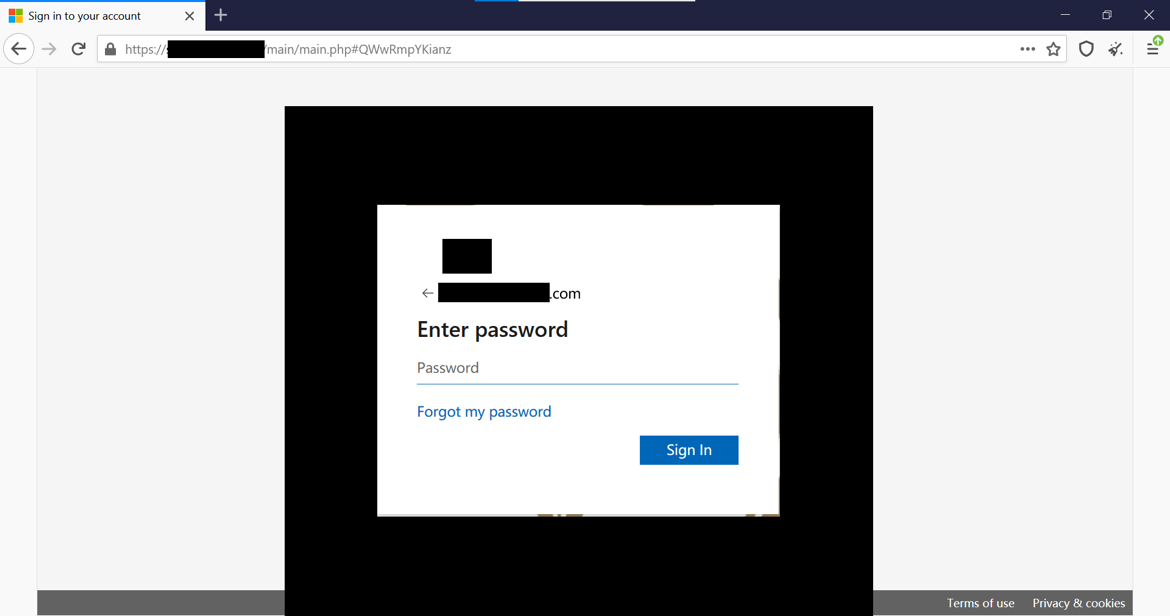
Figure 2
Targeted Office 365 phishing attack.
The logo images and other identifying information have been redacted.
This attack is a good example of the ability of bad actors to execute targeted attacks at scale through automation and abusing services and technologies designed to accelerate and secure digital transformation. Like many phishing attacks, this one targeted Office 365 credentials. Valid credentials would have allowed the attackers to access a variety of Office 365 services to launch devastating or email account compromise attacks and steal volumes of sensitive data.
*Inbox Detection and Response is a new category of anti-phishing solution designed to continuously detect and automatically respond to phishing, business email compromise, email account compromise, and other targeted email threats. Gartner’s name for IDR is Cloud Email Security Supplement (CESS) and Forrester calls it Cloud-native API-enabled Email Security (CAPES).