This is a follow up to the July edition published last month.
For this August edition of Phishing by the numbers, we’re presenting summary statistics along with a deeper dive into a specific customer.
Summary Statistics
In August, Cyren detected nearly 24,000 confirmed email threats that evaded detection by the customers’ secure email gateways or Microsoft Defender for Office 365 (FKA Advanced Threat Protection). The key takeaways include:
- While phishing continues to be the predominant threat arriving in users’ mailboxes, the number of BEC incidents nearly tripled. However, the larger number of BEC incidents is due to changes in detection logic because of customer requests to catch and eliminate scam attempts like the Nigerian Prince emails.
- 11% of incidents were classified as BEC compared to 4% in July
- 87% of malicious emails contained phishing URLs
- 2% of malicious emails included a malware attachment
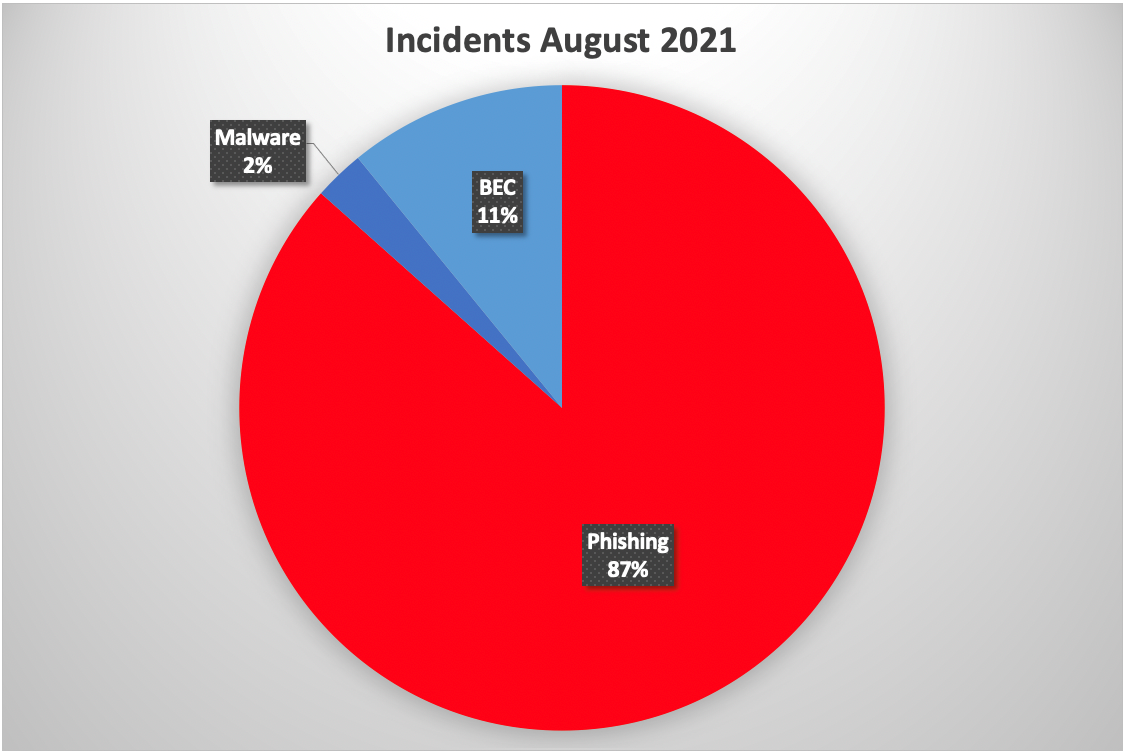
Figure 1 – Threats by type (all customers)
- Specialized detection and automated incident response are critical to eliminating threats before risky users do something they shouldn’t.
- 94% of threats were detected before the recipients read the messages.
- About 80% of the zero-day threats detected using real-time analysis while 13% were detected using Cyren’s threat intelligence databases.
- The remaining 7% were suspicious messages that required human analysis. Cyren Incident Response Services investigated and classified 3 times faster than customers without the incident response service.
- User education matters but organizations must put it to good use, especially since most employees think phishing is IT’s problem to solve. Providing the users with a tool for ad-hoc scans of emails before submitting them to the helpdesk/SOC greatly reduces the volume of phishing alerts.
- 7% of total of confirmed phishing threats were triaged by end users rather than bogging down helpdesk or SOC personnel with basic or initial analysis.
- Of the suspicious messages submitted to the IDR platform, only 1% were false positives.
Example Customer Statistics
This financial services organization has offices in the US and UK. While the term “financial services” can conjure images of giant Wall Street banks with hundreds of security staff and a billion-dollar IT budget, this company is a medium-sized business with a complex organizational structure – multiple subsidiaries, locations, and Office 365 tenancies. It’s worth noting they have a Secure Email Gateway from a very established vendor. Like the July report, these threats evaded the gateway and arrived in users’ mailboxes.
- The first interesting detail is the above average rate of BEC incidents, possibly caused by changes in detection logic. Phishing continues to be the predominant email threat arriving in users’ mailboxes.
- 83% of incidents contained phishing URLs
- 14% were BEC attempts, compared to 3-5% on average
- 3% of messages included a malware attachment, the normal rate
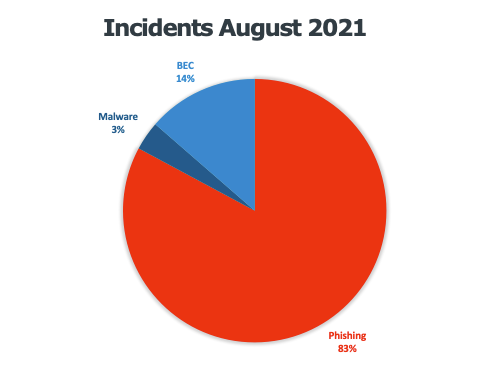
Figure 2 – Threats by type (financial services customer)
- This organization appears to be subject to numerous targeted attacks. Cybercriminals target money or credentials. It’s easy to assume the bad actors targeting this organization focus on the former.
- The company’s three most targeted users account for 48% of all malicious email incidents
- 30% of all incidents targeted the CFO of one of its subsidiaries.
- 11% of all malicious incidents targeted the Vice President of Finance of the same subsidiary
- The remaining 7% were targeted at the CFO of another subsidiary
- Threat intelligence is important but real-time analysis is critical for detecting evasive and zero-day email threats.
- 94% of evasive threats were detected with real-time techniques including machine learning or matched patterns of previous attacks (heuristics). This is higher than the August number for all customers, but in keeping with the theory about targeted attacks. Put another way, if most of these threats are unique to this organization, external threat intelligence may be less useful for detecting them.
- The remaining 6% were suspicious messages that required human analysis to confirm the detection
- User education is a critical part of an enterprise security program. This company uses KnowBe4 which is one of the SAT platforms Cyren has integrated with. User training is required for most regulated organizations, but user engagement in the day-to-day fight against phishing is next level.
- 6% of total of confirmed phishing threats were triaged by end users rather than bogging down helpdesk or SOC personnel with basic or initial analysis.
Phishing Attack of Note
Starting Aug 4, 2021 @ 18:32 UTC a phishing attack took place targeting employees of a real estate company. The phishing emails slipped past the email server defenses and were delivered to the ‘inbox’ folder.
- This phishing attack was received by 170 employees.
- The email subject was ‘New Message for [email protected] – From com’, where xxx is an email address of the recipient.
- The email body was crafted to appear like a potential client inquiry from the realtor.com website and included a hyperlink to read and reply to the message. The link led to a phishing page designed to harvest realtor.com credentials.
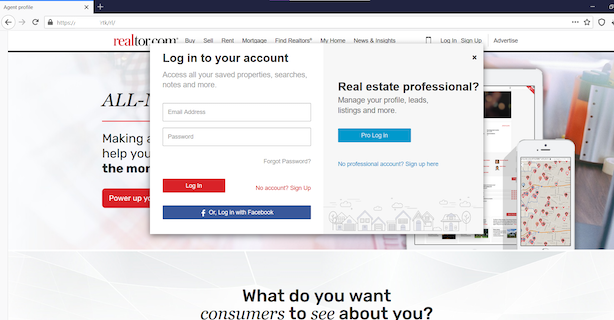
Figure 3 – Phishing attack targeting realtors
This attack is another example of bad actors that can execute targeted attacks at scale. If the attackers could craft a campaign targeting realtors and then launch an attack against 170 unique individuals in a single firm, they most likely attacked other real estate firms that aren’t Cyren customers. Armed with login credentials to realtor.com, scammers could have conducted any number of follow-on attacks and fraud:
- Many realtors re-use passwords across systems so the credentials for realtor.com can be used to access other platforms
- The ability to impersonate listing agents allows criminals to launch social engineering attacks targeting would-be renters and home buyers, bilking them for security deposits and extracting sensitive personal data.