Today we came across an e-mail with an Excel Workbook attachment, which upon first inspection appears to be password-protected. The presence of the EncryptedPackage stream in an OLE2 document indicates that it is protected by a password, which obviously would require the user to enter one in order to open the document properly. Or at least that’s what the bad guys would like email or AV scanners to think.
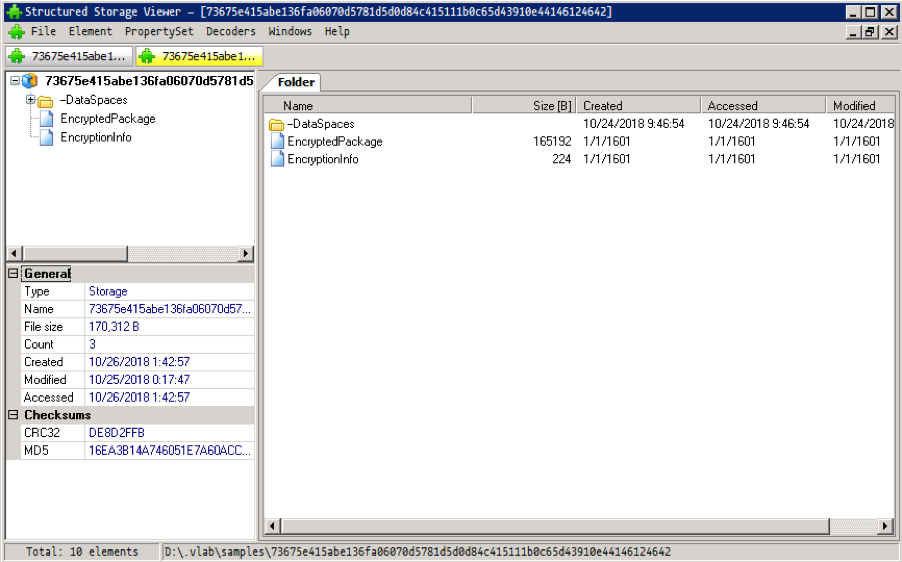
Figure 1
Looking at the e-mail, which is couched as a very generic price quote request, the sender did not provide any password for the attachment, so what gives?
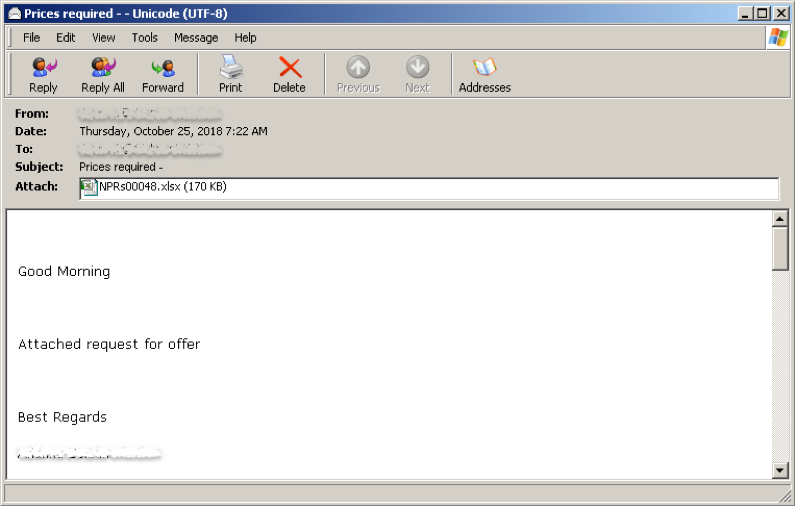
Figure 2
Sounds like something we’ve already seen a few years back, six years to be exact. Do you remember VelvetSweatshop and the infamous CVE-2012-0158 exploit which took advantage of the Microsoft Excel default password hidden feature to evade detection? Well, this malware campaign will surely bring you back to those old days.
First let’s try to open the document to see if Microsoft Office will be able to load it properly.
Figure 3
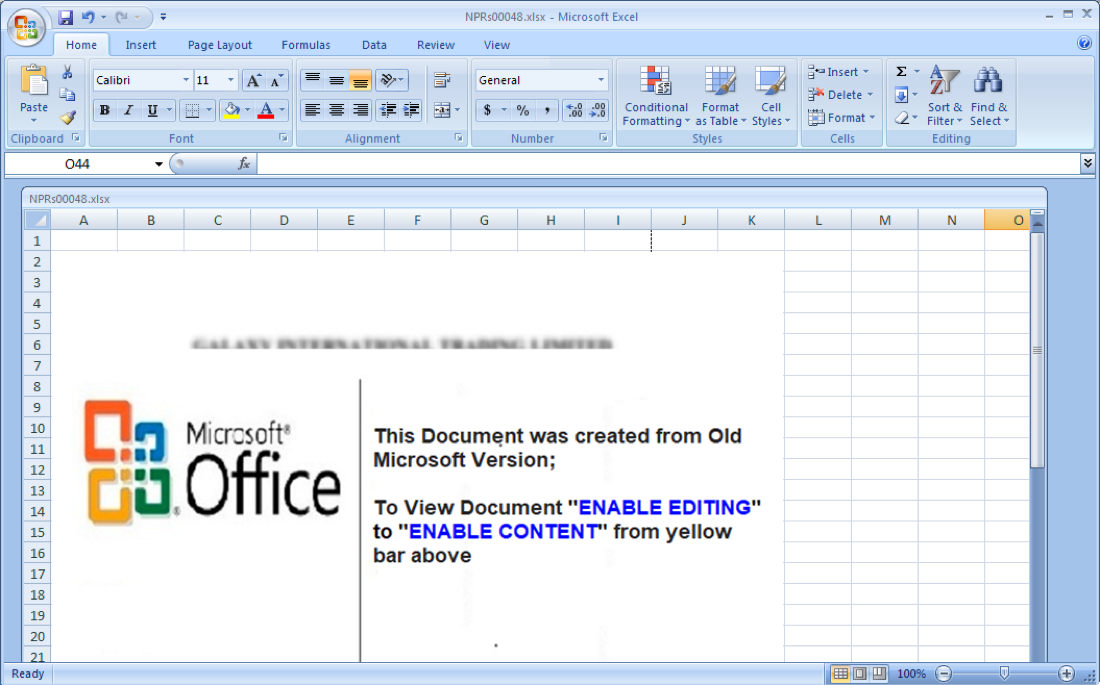
Figure 4
And sure thing, Microsoft Office Excel was able to open the document with no problems at all—and no request to enter a password. So let’s take a look at what’s happening in the background.
Exploits Office Vulnerability CVE-2017-11882
The first thing you’ll notice is the presence of EQNEDT32.EXE being loaded by svchost.exe. This behavior indicates a possible exploitation of CVE-2017-11882(Microsoft Office Memory Corruption Vulnerability).
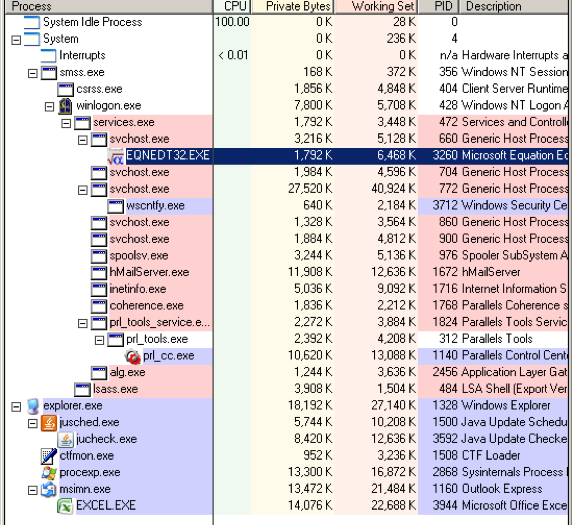
Figure 5
Digging a little deeper, we debugged the exploit shellcode to see what this document really does in the background. Sure enough, this sample does indeed exploit CVE-2017-11882 and attempts to download and execute an executable payload (supposedly saved as %PUBLIC%vbc.exe in the affected computer’s system), as shown in the screenshots below.
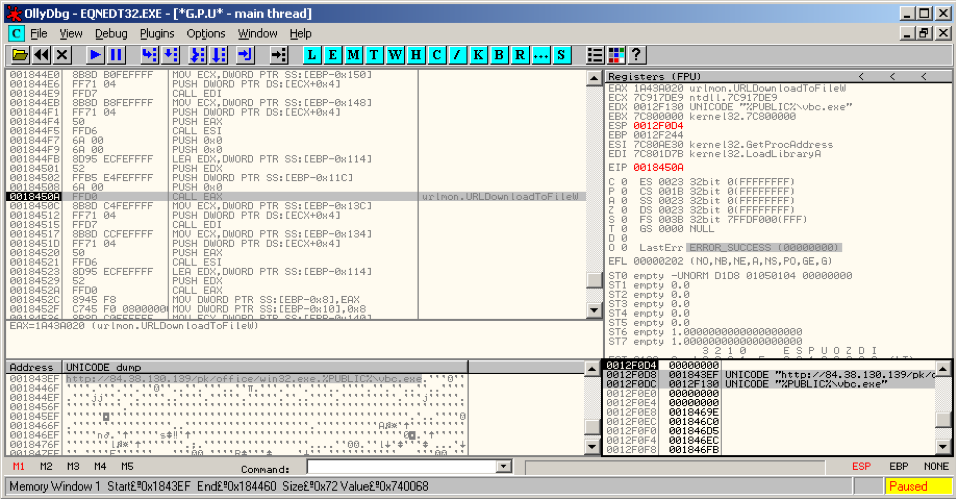
Figure 6
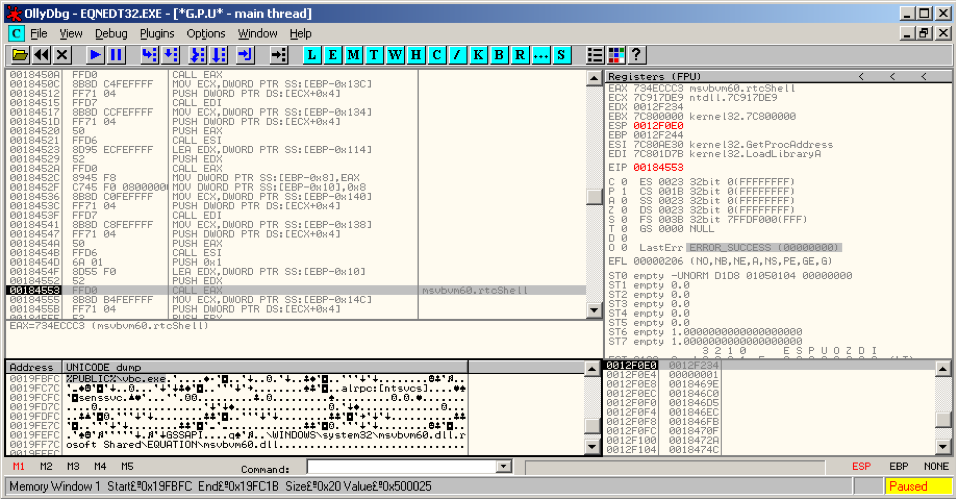
Figure 7
VelvetSweatshop Default Password Ploy Still Being Used
We also decrypted the email attachment and confirmed that this document is taking advantage of the old Microsoft Office hidden “feature” that uses a default password to load encrypted documents, as shown in the lines of code in the screenshot below.
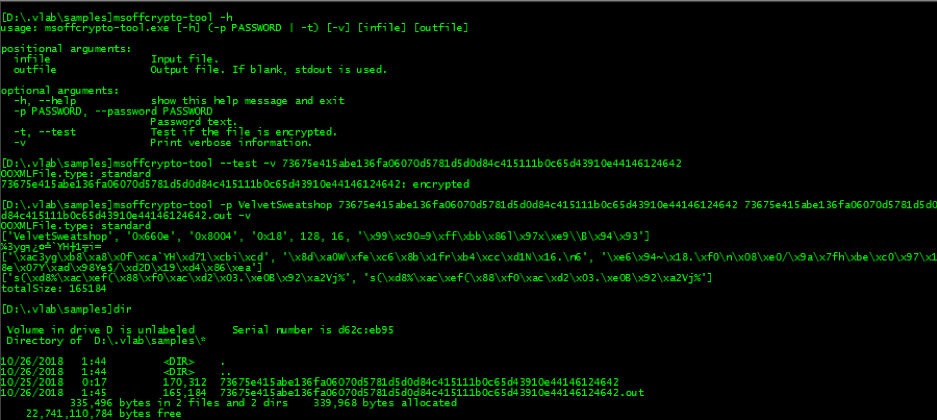
Figure 8
Unfortunately, the download link from this exploit sample was inaccessible as of this writing, so we are not able to provide an analysis of its payload.
Indicators of Compromise and Cyren Detection
|
SHA256 |
Object Type |
Remarks |
Cyren Detection |
|
04ee59add6c2df247f97a17eab8594a2a28b7e17e7ce3e9cc5c334ae0ac265de |
EML |
Subject: Prices required – |
CVE1711882 |
|
fe5568568d4930866d29699b46e11711c462bfcefd05589e98c6b5250da074ff |
EML |
Subject: Prices required – |
CVE1711882 |
|
73675e415abe136fa06070d5781d5d0d84c415111b0c65d43910e44146124642 |
XLS |
Password-protected: VelvetSweatsho[ |
CVE1711882 |
|
http://84.38.130.139/pk/office/win32.exe |
URL |
Saved to: %PUBLIC%vbc.exe Payload: Inaccessible as of this writing |
Prevention and Mitigation
We remind readers that Microsoft issued a patch for the CVE-2017-11882 exploit in 2017. Outdated software, operating systems, browsers, and plugins are major vectors for malware infections.