Last week, CYREN detected interesting emails that contained links to fake video pages. We have included a screenshot of the email. The rough translation of the subject line is “hidden camera in their house”, and the Youtube link looks like it might deliver the goods – but of course the only hidden part is the Rovnix banking Trojan.
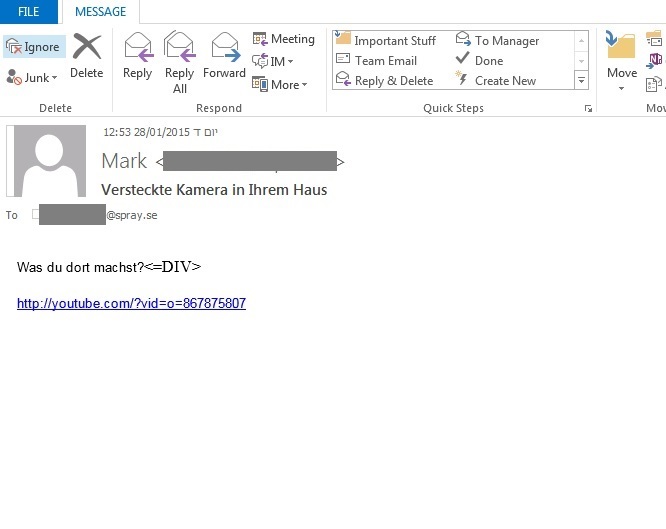
Clicking the link in the email will lead to one of several “youtube.com” links – but the actual domain is “beizhanliu.com”. The malicious URL’s vary and we gathered the following list:

The YouTube link that opens a Vimeo page should be a giveaway that all is not well but we assume enough users proceed to the next step. Once the page opens it suggests download of a “Missing Adobe Flash Plugin” which is actually a Rovnix BankingTrojan.
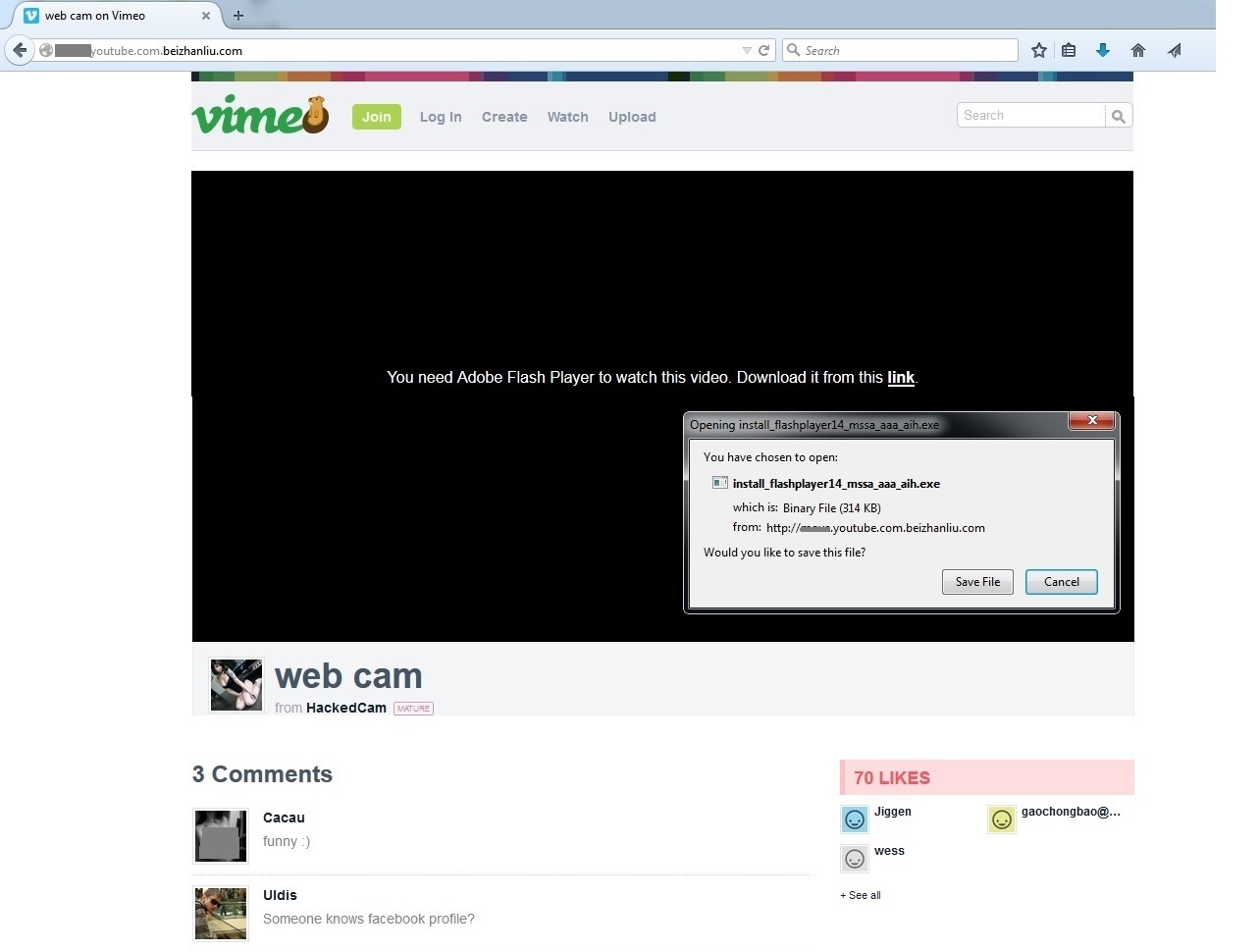
The downloaded file named “install_flashplayer14_mssa_aaa_aih.exe” is already detected by our heuristic signature “W32/Rovnix.A.gen!Eldorado “. Upon execution, it creates a copy of itself to the following location:
%System%[randomchars].exe
It also creates the following autorun registry entry so that it will run at windows startup:
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun
[randomchars] = “%System%[randomchars].exe”
This new variant of Rovnix connects to the following C&C Servers that is hardcoded in the decrypted “.reloc” section of the malware:
![]()
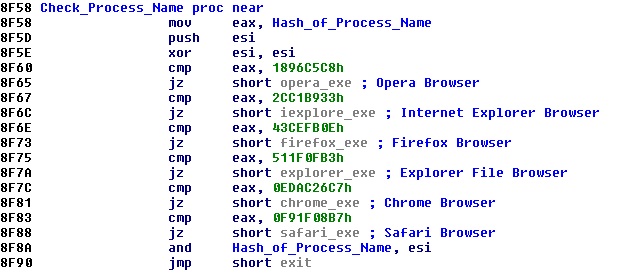
In order to hide itself from the process it injects malicious code into the normal process “explorer.exe”. It also injects code into the following browsers to steal data, keystrokes, usernames and passwords:
In this Rovnix variant, the information data to be sent to C&C is encrypted with pseudo-ramdom algorithm and encoded with base64 in order to avoid detection in the traffic network.
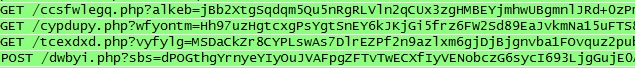
Legend:
“/c[random_chars].php” – stands for /config.php
“/t[randomchars].php” – stands for /task.php
“/d[randomchars].php” – stands for /data.php
Decrypted Information Data:
![]()
The Rovnix Bot Version is 2.13.425.
Rovnix poses a critical security risk to computers. Keeping your antivirus definitions up to date, will protect you from Banking Trojans such as this.