Locky is a new form of ransomware which has made headlines by holding three hospitals’ data hostage recently and encrypts a broad range of document and media formats before displaying ransom screens to infected users with payment instructions. A typical decrypt ransom is around $200 per infected system, with the Hollywood Presbyterian Medical Center in Los Angeles paying the equivalent of $17,000 in Bitcoin.
Overview: Explosive Growth
In the first few weeks of its emergence in February, Locky was spread using malicious document attachments. Users who activated the macros in these documents unknowingly downloaded the main malware component from servers which have been linked to the botnet used by infamous banking Trojan Dridex (as reported by Trustwave’s SpiderLabs).
Locky’s delivery method has quickly changed to JavaScript. JavaScript is lightweight and highly dynamic, which makes it easier for cybercriminals to quickly obfuscate and manipulate their code to evade anti-malware products.
Growth has been phenomenal – on March 31st, CYREN’s honeypots saw 1.5 million unique samples in a 24-hour period. Analyzing in depth a data sample from CYREN’s honeypots covering a seven hour period, we see a huge volume of malware email traffic with Locky JavaScript variants representing 90% of malware attachments. Although the attachments slightly differed from previous ones, they contained the same type of malware. On average over the last four weeks, 40% of all malicious emails contained a Locky JavaScript variant.
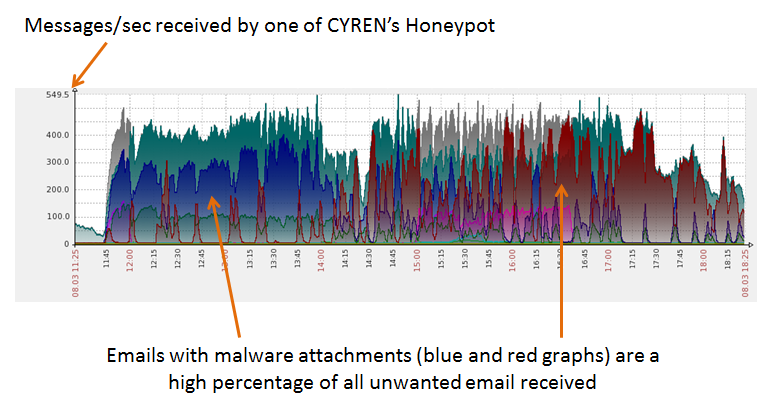
Similar graphs from honeypot traffic collected in February when Locky was first reported in the wild also show surges in the volume of emails containing JavaScript attachments:
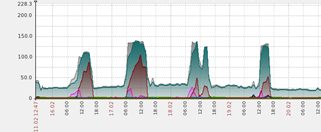
A review of the outbreak history shows multiple new variants on a daily basis. The frequency of these scripts being mutated and obfuscated in short periods of time shows that the group behind this campaign is very active, and also suggests that the group regularly checks if their scripts are being detected by anti-malware products.
The JavaScript initiates a download of the encryption malware and a large amount of compromised websites have been used to (unknowingly) host the malware. Some examples:
- artlatex.avantesoftware.com.br
- artsavy.com
- azshop24.com.vn
- baiya.org
- baromedical.hu
- behrozan.ir
- beltshoesnmore.com
- bindulin.by
- biosoftbelgium.com
- bitmeyenkartusistanbul.com
- bnw.net.vn
- buyfuntees.com
Main Target: European and American Businesses
As shown in the graphs above, the surge of emails occurred during weekdays and between working hours (attacks are usually 12:00 – 20:00 UTC), which would suggest that this campaign targets email recipients who are most likely to open messages while at work in European and American companies. This means that there is a high probability that victims of the attack would execute the malicious attachment on a company device resulting in encryption of highly valuable data and files. In this scenario, businesses would more likely pay the ransom to recover precious data.
How It Works: Executable Unpacking
To further evade detection, the main Locky binary components, which are downloaded by the JavaScript component, arrive as packed executables making them unique for each wave. After unpacking, further inspection shows that the core components are practically the same.
Upon execution of the core component, it disables the file system redirection by calling Wow64DisableWow64FsRedirection.
Before proceeding with its malicious routines, it checks the language identifier for the system locale.
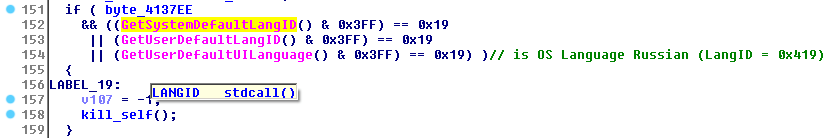
If the language identifier matches the Russian LangID, it moves itself to %temp%sys<random>.tmp, before deleting itself via the following command and terminates its own process:
cmd.exe /C del /Q /F <path to temp filename>
Otherwise, the following registry key is created…
HKEY_CURRENT_USERSoftwareLocky
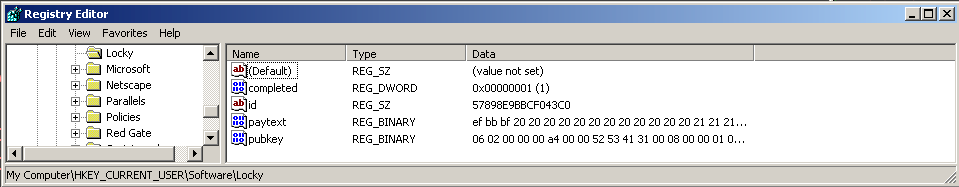
…and checks for the following registry entries under the Locky registry key:
id
pubkey
paytext
completed
It would then drop and execute a copy of itself in %temp%svchost.exe, and gather system information that it sends to its command and control server (C&C), which includes a unique ID generated for the affected system. The raw data sent to the C&C looks like this (with modifications per infected system):
|
id=57898E9BBCF043C0&act=getkey&affid=5&lang=en&corp=0&serv=0&os=Windows+XP&sp=3&x64=0 |
The ID is generated by retrieving the first eight bytes of the MD5 hash of the affected system’s volume path GUID.
Listed in the table below are CnC server IP’s from some of the Locky variants that we have analyzed.
|
Variant |
CnC |
Location |
|
W32/Locky.H |
195.154.241.208 |
France |
|
W32/Locky.H |
46.4.239.76 |
Germany |
|
W32/Locky.Q |
188.138.88.184 |
Germany |
|
W32/Locky.Q |
31.41.47.37 |
Russian Federation |
|
W32/Locky.Q |
91.121.97.170 |
France |
|
W32/Locky.Q |
185.46.11.239 |
Russian Federation |
|
W32/Locky.S |
188.138.88.184 |
Germany |
|
W32/Locky.S |
31.184.197.119 |
Russian Federation |
|
W32/Locky.S |
51.254.19.227 |
France |
|
W32/Locky.S |
5.34.183.195 |
Ukraine |
|
W32/Locky.S |
185.14.29.188 |
Netherlands |
|
W32/Locky.U |
5.34.183.195 |
Ukraine |
|
W32/Locky.U |
185.14.29.188 |
Netherlands |
|
W32/Locky.U |
91.219.29.55 |
Ukraine |
|
W32/Locky.V |
151.236.14.51 |
Netherlands |
|
W32/Locky.V |
149.154.157.14 |
Italy |
|
W32/Locky.V |
37.235.53.18 |
Spain |
|
W32/Locky.V |
89.108.85.163 |
Russian Federation |
|
W32/Locky.V |
212.47.223.19 |
Estonia |
|
W32/Locky.V |
192.121.16.196 |
Netherlands |
|
W32/Locky.W-X |
78.40.108.39 |
Kazakhstan |
|
W32/Locky.W-X |
91.195.12.131 |
Ukraine |
|
W32/Locky.W-X |
149.154.157.14 |
Italy |
|
W32/Locky.W-X |
151.236.14.51 |
Netherlands |
|
W32/Locky.W-X |
37.235.53.18 |
Spain |
|
W32/Locky.Y |
91.234.32.192 |
Ukraine |
|
W32/Locky.Y |
31.184.196.75 |
Russian Federation |
|
W32/Locky.Y |
91.219.30.254 |
Ukraine |
|
W32/Locky.Y |
31.184.196.78 |
Russian Federation |
|
W32/Locky.Y |
78.40.108.39 |
Kazakhstan |
To prevent the user from restoring files from backup, Locky executes the following command:
|
vssadmin.exe Delete Shadows /All /Quiet |
An auto start entry is also added in the registry to ensure its execution every time the system starts.
This ransomware searches for files having file extensions listed in the table below and encrypts them, renaming the files using the generated system ID from the affected machine appended with a random 8-byte hash value and ‘.locky’ file extension.
|
Ex. [system id][random 8 byte hash].locky |
|
.m4u |
.m3u |
.mid |
|
.wma |
.flv |
.3g2 |
|
.mkv |
.3gp |
.mp4 |
|
.mov |
.avi |
.asf |
|
.mpeg |
.vob |
.mpg |
|
.wmv |
.fla |
.swf |
|
.wav |
.mp3 |
.qcow2 |
|
.vdi |
.vmdk |
.vmx |
|
.gpg |
.aes |
.ARC |
|
.PAQ |
.tar.bz2 |
.tbk |
|
.bak |
.tar |
.tgz |
|
.gz |
.7z |
.rar |
|
.zip |
.djv |
.djvu |
|
.svg |
.bmp |
.png |
|
.gif |
.raw |
.cgm |
|
.jpeg |
.jpg |
.tif |
|
.tiff |
.NEF |
.psd |
|
.cmd |
.bat |
.sh |
|
.class |
.jar |
.java |
|
.rb |
.asp |
.cs |
|
.brd |
.sch |
.dch |
|
.dip |
.pl |
.vbs |
|
.vb |
.js |
.h |
|
.asm |
.pas |
.cpp |
|
.c |
.php |
.ldf |
|
.mdf |
.ibd |
.MYI |
|
.MYD |
.frm |
.odb |
|
.dbf |
.db |
.mdb |
|
.sql |
.SQLITEDB |
.SQLITE3 |
|
.asc |
.lay6 |
.lay |
|
.ms11 (Security copy) |
.ms11 |
.sldm |
|
.sldx |
.ppsm |
.ppsx |
|
.ppam |
.docb |
.mml |
|
.sxm |
.otg |
.odg |
|
.uop |
.potx |
.potm |
|
.pptx |
.pptm |
.std |
|
.sxd |
.pot |
.pps |
|
.sti |
.sxi |
.otp |
|
.odp |
.wb2 |
.123 |
|
.wks |
.wk1 |
.xltx |
|
.xltm |
.xlsx |
.xlsm |
|
.xlsb |
.slk |
.xlw |
|
.xlt |
.xlm |
.xlc |
|
.dif |
.stc |
.sxc |
|
.ots |
.ods |
.hwp |
|
.602 |
.dotm |
.dotx |
|
.docm |
.docx |
.DOT |
|
.3dm |
.max |
.3ds |
|
.xml |
.txt |
.CSV |
|
.uot |
.RTF |
|
|
.XLS |
.PPT |
.stw |
|
.sxw |
.ott |
.odt |
|
.DOC |
.pem |
.p12 |
|
.csr |
.crt |
.key |
Locky does not encrypt files that are found in paths listed in the table below to prevent the system from crashing.
|
tmp |
winnt |
|
Application Data |
AppData |
|
Program Files (x86) |
Program Files |
|
temp |
thumbs.db |
|
$Recycle.Bin |
System Volume Information |
|
Boot |
Windows |
Furthermore, Locky can also encrypt files from network share even if these shares are not mapped to a local drive.
After encrypting files, it sets the ‘completed’ registry entry’s value to 1 and fills up the other registry entry values:
It then changes the desktop wallpaper to a ransom note giving the instructions the user should follow to recover the encrypted files. Along with this, a text copy of the ransom note with a file name of _Locky_recover_instructions.txt is also dropped in every folder where files have been encrypted.
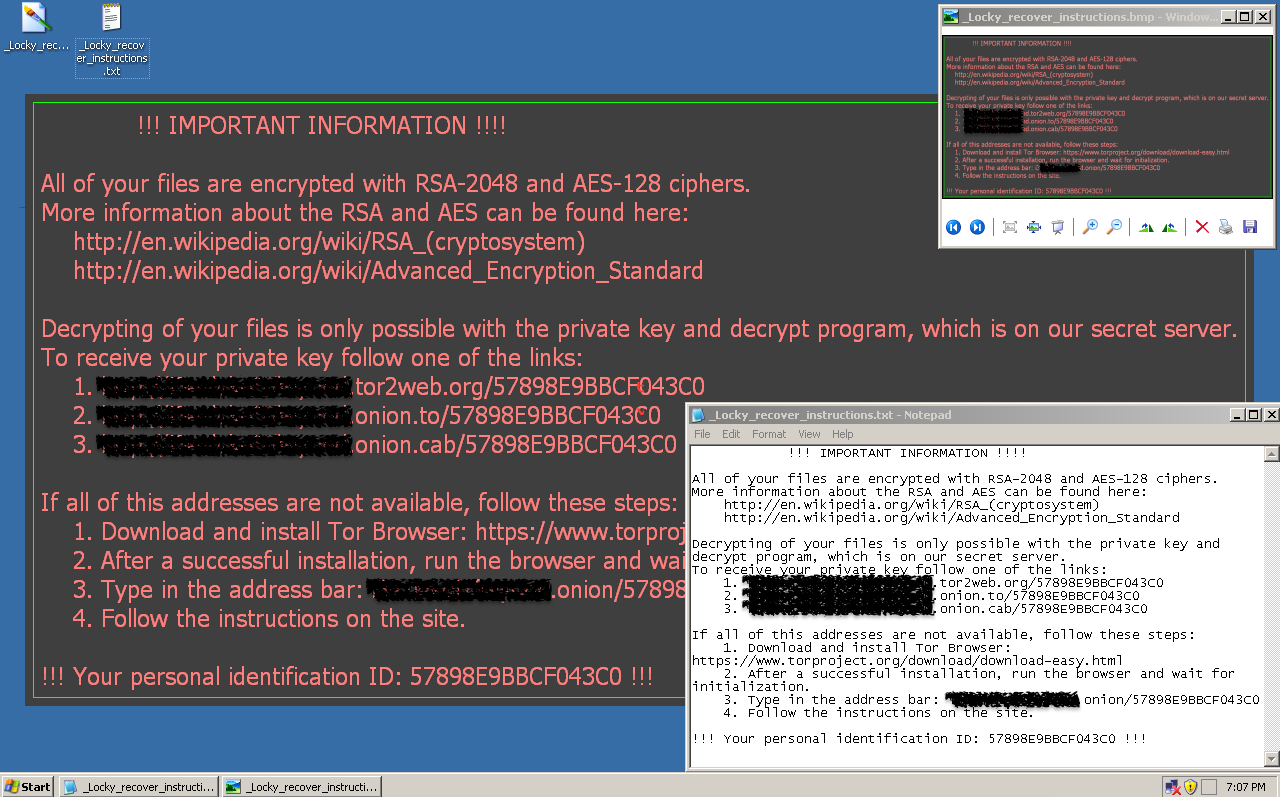
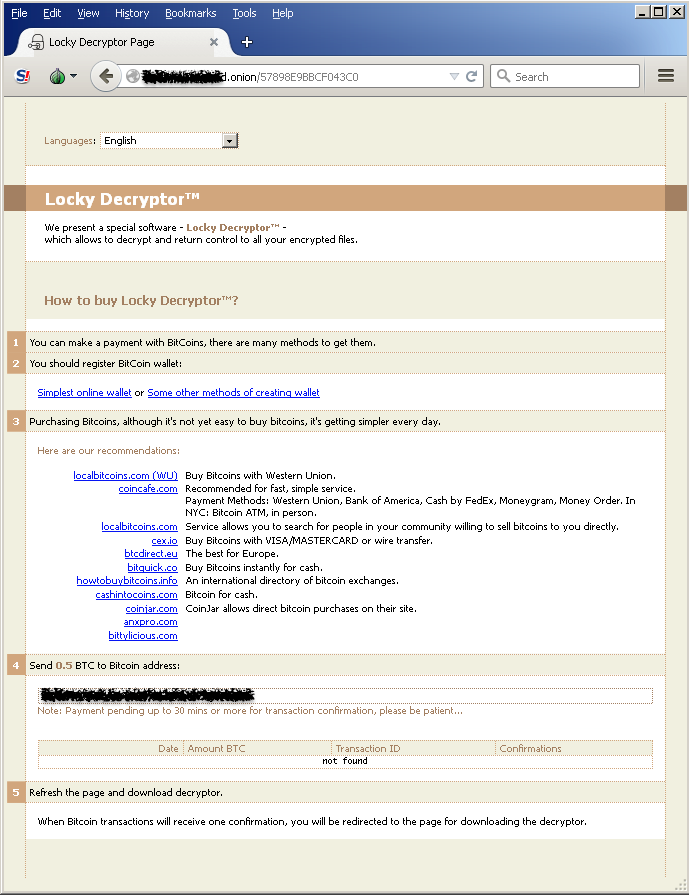
Strong Gateway Protection
The JavaScript attachments and the downloaded Locky variants are all detected and blocked by CYREN’s security cloud. CYREN provides customers with strong gateway-level protection from Locky ransomware across all of our cloud-based Internet security services:
- Cyren Web Security detects and blocks outbound web connections to malicious Locky URLs, hosts, and domains trying to download the ransomware payload. Enterprise customers will also be protected by CYREN WebSecurity 3.0, which will be released on March 31, 2016. It includes a new Advance Threat Protection capability that utilizes a multi-sandbox array to identify, analyze, and block new, never-before-seen Locky variants.
- Cyren Email Security detects and blocks this malware for enterprise customers by identifying Locky virus outbreaks in email, as well as identifying and blocking messages containing the Locky polymorphic Javascript or Office documents containing malicious macros
- Cyren Cyber-Intelligence detects Locky-related threats in both email and web traffic, enabling OEM customers to deliver strong ransomware protection to their end users and customers.
Other Best Practices
In addition to Internet security protection at the web and email gateway, businesses should implement a multi-layered security approach that includes strong endpoint protection, and a robust data backup capability to ensure that ransomware infections don’t cripple your business. This needs to include strong end-user education about cyber security, training users to be very vigilant when opening emails from unknown sources and avoiding opening attachments that are executable. Microsoft Office macros should always be disabled (which they are by default).