A researcher at Cyren has found that a malicious Google Chrome extension is spreading nude celebrity PDFs to Facebook groups. A user is uploading a PDF document to groups with the name:
”Jessice_Alba_Leaked-sextapeVide_oSun_Dec_4_2016_22_99.mp4.pdf“
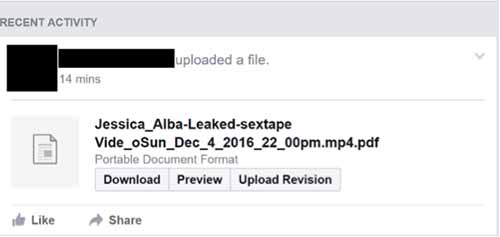
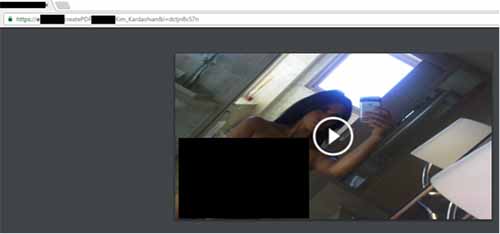
Opening the PDF reveals a nude picture with a ”Play“ button in the middle.
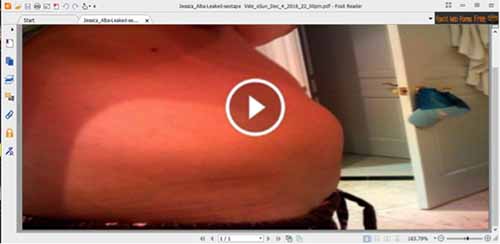
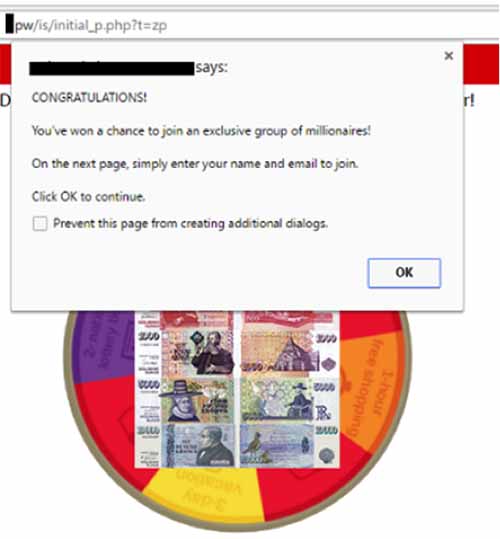
Clicking on the picture opens up a Web browser for “viewing” the video. If the browser is IE, FireFox, or Safari then the user will be taken to an aggressive advertising webpage (nudity, fake lottery).
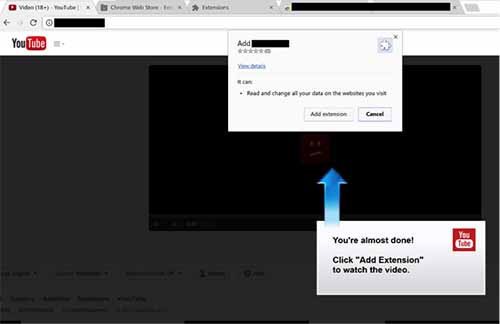
However, if the user is using Google Chrome, the link opened is “hxxps://rb-xxxxxx.xxx/gxxxxo.php“ and shows a phony YouTube site. Clicking the play button brings up a pop-up window inviting the user to install a Google Chrome extension. After installing that extension, the browser opens up a Facebook.com login page. The extension is able to read the user’s friend list, Facebook groups, plus all personal information and upload the PDF to groups, posts, and to friends in private chat.
A JSON config file is downloaded from: hxxp://xxxxxx[.]com/jquery[.]php?<random string> that has URL to another script as shown in the JSON format. The Google Chrome extension has a JavaScript file called background.js that acts as the initial downloader for that script, ba.php. hxxps://xxxxxx.xxx/2017/ba[.]php?<random value>
<snip>
{
“mundet”: “1”,
“d”: “https://xxxxxx.xxx/2017/”,
“f”: “ba.php?”
}
</snip>
The random value is computed using the following code:
<snip>
Math.floor(Date.now() / 1000);
</snip>
The downloaded chrome extension script, contains several chrome event handlers, which includes the following:
- chrome.webRequest.onBeforeRequest. This handler is used to observe and analyze traffic and to intercept, block, or modify requests in-flight. This handler contains a long list of AV’s and AntiSpam domains (shown below) which this malicious chrome extension blocks or prevents from being opened
- chrome.tabs.onUpdated:
- This handler is used to monitor opened tabs and also intercepts or blocks specific tabs from being opened.
- It also blocks the chrome extensions and chrome devtools tabs from being opened, preventing the user from uninstalling the malicious chrome extension
<snip>
if(tab.url.indexOf(“chrome://extensions/”) > -1 || tab.url.indexOf(“chrome://chrome/extensions”) > -1 || tab.url.indexOf(‘chrome-devtools’) > -1) {
chrome.tabs.remove(tabId);
if((tab.url == “chrome://extensions/” || tab.url == “chrome://chrome/extensions”) && changeInfo.status == ‘loading’) chrome.tabs.remove(tabId);
</snip>
- Prevents the user from opening herokuapp.com
- Force opened tabs with specific attributes to redirect automatically to vk[.]com/away[.]php?to=facebook.com
- Opened tabs with the string “#id:1g345hh”, apparently this tab refers to the fake youtube vide page tab
- Opened tabs with URLs containing the string “allactivity”
- Download and execute another malicious chrome extension script from hxxps://xxxxx[.]com/2017/main[.]php?<random string>

The ba.php script file has hardcoded URL‘s of many anti-virus and anti-spam companies and blocks their webpages if the infected user tries to access them.
The third chrome extension script main.php contains the code which makes this malicious chrome extension propagate through facebook. This behavior alone makes this malicious chrome extension a new breed of web-based Worms.
The PDF that is uploaded to Facebook is generated by selecting the name of a celebrity randomly from the script file and combining this with random characters.
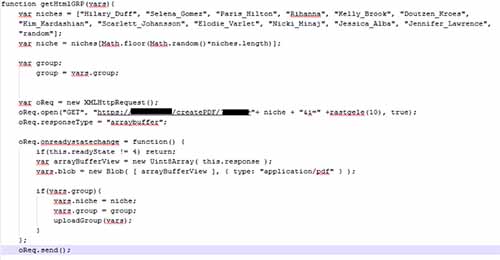
For example this link would generate a PDF with a picture of Kim Kardashian with a play button „hxxps://xxxxxxx/createPDF/?xxxx=Kim_Kardashian&i=dctjn8v57n“.
If the PDF is accessed from a mobile device the user will get this message if there is no PDF viewer on the mobile device: “found it on youtube… if you are on mobile you need to install Google PDF viewer from play store to watch this video. OMG it’s really you”. The message is translated into 25 different languages depending on the user’s locale. Opening the PDF on a mobile device and clicking on the play button leads the user to a mobile version of the spam advertising site.
After opening the PDF on the mobile device the play button scrolls through multiple links and ends up opening one of them. Spinning the wheel then opens up more fake spam windows.
So to summarize, this advertising campaign is able to create a sort of botnet to spread via a combination of nude celebrity pictures, a chrome extension, and Facebook posts – which all ultimately lead to an aggressive spam/advertising page.
Facebook runs on all kinds of devices, although this malware campaign targets the Chrome web browser platform, it is not impossible for the malware writers to find ways to propagate through other browsers, as all the other browsers also have their own browser plugins/extensions.
The fact that this malicious Chrome extension was hosted in the Google Chrome Extension Store, tricks users into believing that the Chrome extension came from a trusted source/publisher and are probably safe to install. Google has removed the extension from the webstore. Cyren detects the Chrome extension scripts as, JS/Vekikrom.A!Eldorado for ba.ph and JS/Vekikrom.A1!Eldorado for main.php and background.js as JS/Agent.XL.
Removing the extension from Chrome
To remove this extension the infected user would have to delete the Regestry key from the Registry Editor and also the folder in AppData.
This is the path to the Registry Editor:
HKEY_LOCAL_MACHINESoftwareGoogleChromeExtension
This is the path to the extension folder:
C:UsersUSERAppDataLocalGoogleChromeUser DataDefaultExtensions
Information about uninstalling Chrome extension manually can be found here!
Want to learn more about cloud-based web security? Contact us here!