by Dor Nabet
We’ve all experienced the typical phishing site where the attacker asks that you enter your credentials while the sketchy Microsoft logo on top of the page makes you feel comfortable doing so. Those phishing sites used to be easy to recognize: the simple behind-the-scenes code would reveal the site’s identity, functions, information delivery methods and where the data was being sent to.
The detection tools have evolved and become more sophisticated, but so have the phishing creators. For this reason, securing Microsoft Office 365 has become harder. One of the strategies the attackers use to elevate the complexity of a phishing site and evade detection by existing organizational mechanisms is obfuscation of the phishing site code. This includes using an obfuscated redirection site whose sole purpose is to redirect the user to the actual phishing site while avoiding detection. The most common method to do so is JavaScript obfuscation: the code of a phishing attack is made obscure and unintelligible so it cannot be read easily.
Let’s see how the attacker creates an obfuscated redirection site. Sidenote: this task is typically performed using a phishing kit, but we will be looking at the manual process.
First, a regular phishing site with a common login (Office 365, for example) is built. Then the source code and the functions are written, just like for any other website. When those are ready, the attacker obfuscates JavaScript to scramble the code. As a result, the regular function names are replaced by random numbers and letters, creating an array of loops to confuse the detection tools and pass the defense, eventually reaching the victim.
That’s not all, however. The attacker will not just send the site’s URL directly to the victim – they would create another site, either with its own domain or with a compromised one, employing multiple functions and loops (usually implemented using base64) to redirect the victim to the actual phishing site. This creates yet another layer of evasion from the detection tools.
Let’s go over this process step by step.
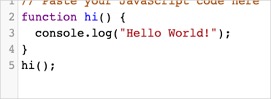
The phishing source site can be something as simple as one function:
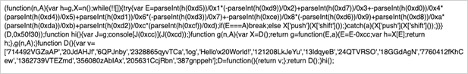
When obfuscated, the code becomes unreadable and hard to understand:
Initially, the victim won’t get the original URL but rather a redirecting one: when clicked, it will take the victim to a phishing site. If you encounter a site with similar characteristics, you would be well advised to close it and report the email sender.
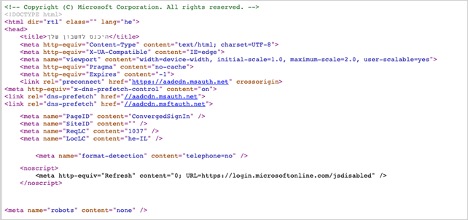
Legitimate sites wouldn’t use a scrambled code that has loops and meaningless JavaScript functions. Let’s demonstrate this using the Office 365 login source code:
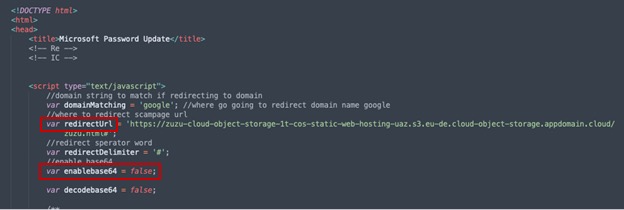
The code from the Microsoft site is easily readable and well organized, no weird functions or parameters are found. On an obfuscated site, however, the code is not so easy to interpret. In the example below, note the suspicious var enablebase64 parameter that we know is part of the obfuscation functions and the var redirectUrl parameter of the redirection URL that takes you to the actual phishing site:
Let’s summarize some basic practices that will help you identify a phishing site, stop a potential phishing attack, and stay safe.
- Stop. Do not open links from any sender. Always check the sender’s address and not just what the email subject and title say.
- Observe. You have checked the sender’s email address and it seems okay. Now ask yourself if you are supposed to be getting emails from that sender.
- Suspect. The sender looks legitimate, but you are not sure if you were supposed to receive anything from him or her. STOP. Don’t click. Take a good look at the URL and the site name. Do they look suspicious to you? Is the site name spelled correctly? Does the URL look real and related to the email sender’s domain?
- Interrogate. Everything looks right, but you are not fully convinced. Check the source code and re-read this blog article to identify the possible suspicious code indicators.
Always keep in mind the golden phishing prevention steps: Stop, Observe, Suspect, and Interrogate. If you’ve taken all four, you should be fine. Read this other blog for more tips and additional detail.