Lately, among the myriad phishing attacks we observe and detect via Cyren Inbox Security, attacks that are distributed via email delivery services (like SendGrid, MailChimp, and MailJet) are increasingly common.
How Attackers Take Advantage of Email Delivery Platforms
- Email magnitude – Email delivery services don’t usually limit the total number of mail recipients. This enables an attacker to send large volumes of targeted emails.
- Tracking and personalization – Attackers can visualize and measure the impact of sent emails on the targets, enabling them to launch customized spear phishing attacks afterwards.
- Bypassing email filtering capabilities – Attackers distribute phishing URLs that are hosted on legitimate and trustworthy domains that belong to real email delivery platforms. This makes it almost impossible for Microsoft 365 and SEGs to detect and filter the attacks.
Related: Spear Phishing, Whaling, and Delayed Detonation, Oh My!
SendGrid Phishing Attacks on the Rise
SendGrid is a relatively popular cloud-based platform. Additionally, businesses use this platform to send more than 70 billion transactional emails per month. These could include:
- Shipping notifications
- Sign-up confirmations
- Password resets
- Email newsletters
- Nurture tracks
- Other automated or campaign-based messages
SendGrid provides the digital signatures and authentication that companies utilize to validate incoming emails, helping to deliver an average 95% deliverability rate. Unfortunately, if those emails came from compromised SendGrid accounts, they are particularly dangerous because they are not likely to be blocked by email security services.
Phishing attackers oftentimes purposely exploit the branding of global companies, such as SendGrid, within their scams. Since those brands have such a good reputation, the attackers can lull victims into a false sense of security. With such a large number of these trusting users, they are an easy, attractive target for phishing scams.
Unfortunately, on August 28 of 2020, KrebsonSecurity.com reported an unusually large amount of SendGrid customer accounts having been hijacked and used to distribute massive amounts of phishing and malware attacks.
A typical phishing URL would consist of a legitimate SendGrid domain along with a unique subdomain. Together, a targeted query redirects the user directly to the phishing landing page. The use of ‘sendgrid.net’ domain along with the query string allows phishers to evade the existing filtering capabilities and to reach the recipients’ mailboxes en masse.
SendGrid.net Phishing Tactics
A typical phishing URL would consist of a legitimate SendGrid.net domain along with a unique subdomain. Together, a targeted query redirects the user directly to the phishing landing page. The use of the ‘sendgrid.net’ domain along with the query string allows phishers to evade the existing filtering capabilities and to reach the recipients’ mailboxes en masse.
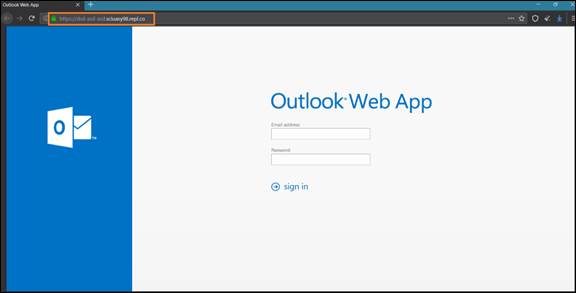
SendGrid phishing page example: URL in the email body ‘hxxps://u14869500.ct.sendgrid[.]net/ls/click?upn=’
through the query opens fake Outlook Web App login page ‘hxxps://dsd-asd-asd.sciuasy98.repl[.]co/’
Between July and August 2020, the phishing attacks sent through SendGrid email delivery service doubled. Today, SendGrid phishing attacks represent 10% of overall phishing attempts.
Mailjet & MailChimp Phishing Attacks
SendGrid is not the only mail delivery solution used for phishing email attacks. Cyren Inbox Security also detected the same phishing pattern distributed by another mail delivery solution, Mailjet. The structure of the phishing URL is almost the same: a random subdomain and unique path hosted on the official ‘mailjet.com’ domain make the phishing link highly evasive.
SendGrid, MailJet & Mailchimp Phishing Attack Examples
URL in the Email Body
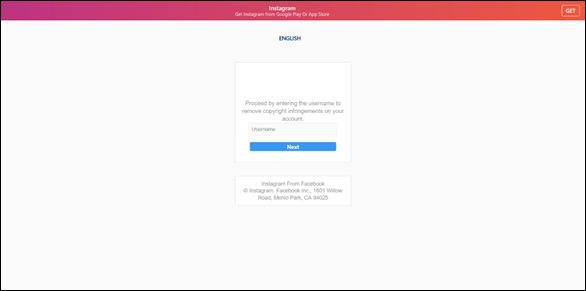
Phishing page example: URL in the email body ‘hxxp://xioo1.r.mailjet[.]com/lnk/AU4AAAfJE_AAAAAAAAAAAAQDRD0AAAAAof8AAAAAABTBagBfIalBY0Gf9aKgRk-JnDPhs5US0AAUlUQ/1/TfMa8721bZVD_0s8AxyZcQ/aHR0cHM6Ly93d3cuYmluYmFzcy5jb20vc3VmZi5odG1s# – o365’ redirected to the scam Instagram support page ‘hxxps://instagramtechsupport[.]com/help/copyright.php’
Spoofed Login Pages for Mailchimp
In addition to traditional phishing attacks via links, attacks via spoofed login pages continue to grow and attempts to steal login credentials of email delivery platform accounts are no exceptions.
On Saturday, September 05, several employees from different Cyren Inbox Security customer organizations received an email from a fake ‘Mailchimp Account Services’ sender. The attacker used the look-alike domain < accountservices@mailchinp.co >
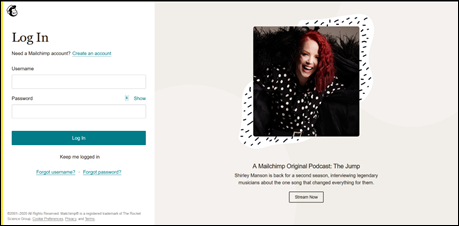
Phishing Mailchimp login page
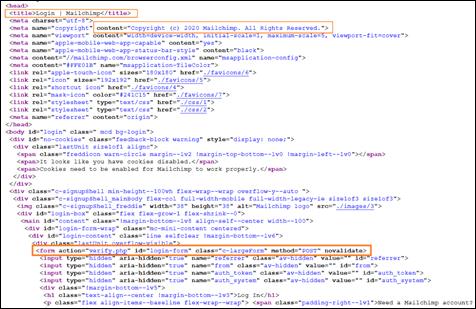
Phishing Mailchimp login page source code
Email Headers
In order to ‘verify the account’ the targeted recipient would click on the phishing URL ‘hxxp://login.app.mailchimp.session.id1552443.m-breden[.]de/Login/login.php’ which opened a very believable but fake Mailchimp login page:
Final Thoughts: Detect and Protect with Cyren Inbox Security
Although these phishing attacks were highly evasive, Cyren Inbox Security was able to scan and automatically detect these suspicious emails. We successfully removed every copy of these masquerading emails from the employees’ mailboxes.
Learn more about how Cyren Inbox Security for Microsoft 365 can help to make sure you stay safe from SendGrid.net phishing attacks.
