Despite investing a record $3B in Secure Email Gateways (SEGs) in 2019, US companies still lost $1.7B to phishing. As threats grow in sophistication and number, traditional defenses frequently fail to detect and remediate phishing, business email compromise, and targeted ransomware attacks. This is not to say SEGs and their native cloud equivalents like Microsoft Defender of Office 365 (ATP) are obsolete. SEGs and ATP play a key role in keeping users’ mailboxes free from spam, most malware, and well-known phishing threats. However, businesses need to complement these technologies with specialized detection and automated remediation to solve the currently unsolved problems associated with targeted phishing.
SEGs Aren’t Foolproof
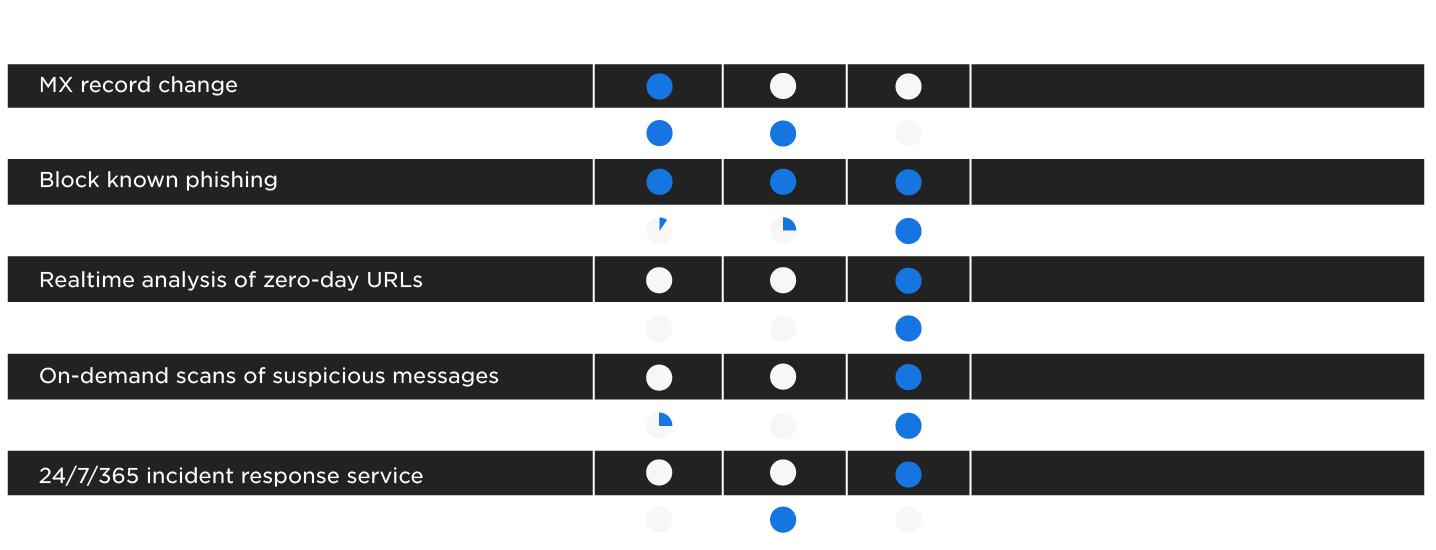
SEGs scan incoming messages once, by referencing a database of known threats. Many SEGS add Time-of-Click Protection (URL rewriting) to give them a second chance as users click links in messages post-delivery. But this measure still relies on databases of known threats–and attackers easily evolve.
While the trusty Secure Email Gateway filters spam and known threats, it can’t detect sophisticated email attacks. Meanwhile:
- Spear phishing and business email compromise (BEC) attacks don’t contain URLs or attachments, so they appear harmless to the SEG
- Cousin domains are used to obfuscate URLs – i.e. saleforce.com (intentional typo)
- Attackers serve up local versions of a spoofed site, so the domain looks legitimate.
- Cybercriminals abuse trusted cloud services to deliver and host their campaigns
- And attackers are constantly iterating and launching new threats
What about Microsoft ATP?
Even the most expensive subscription to Microsoft 365’s native Advanced Threat Protection and Exchange Online Protection, collectively called Defender for Office 365, isn’t enough to defend against targeted attacks. Additionally, features of this software, such as Safe Attachments and Safe Links, are also not enough on their own. Employees must still flag suspicious messages for the security operations center or IT helpdesk to investigate. In fact, even Microsoft insists sophisticated attacks have to be solved by “a community approach.” In their Digital Defense Report, they write:
Our contribution will only be a small piece of what’s needed to address the challenge. It requires policymakers, the business community, government agencies and, ultimately, individuals to make a real difference, and we can only have significant impact through shared information and partnerships.
The Solution: Continuously Search for and Remediate Evasive Threats. Organizations using Microsoft 365 need to complement the gateway-based single-pass inspection model with continuous email monitoring and detection.
In real customer environments, Cyren Inbox Security can detect and remediate 100% of evasive phishing threats the SEG misses. That’s because, unlike the one-time pass done by SEGs that relies on a database of known threat indicators, Cyren Inbox Security continuously looks for threats using specialized techniques like machine learning and real-time analysis of email, web, and file content delivered to users’ mailboxes.
Cyren Inbox Security:
- Continuously scans inbound, outbound and delivered emails in all folders
- Analyzes URLs, web pages, attachments, and shared files in real time
- Looks for anomalies and threat indicators in email sender/recipient behavior
- Applies similarity logic to confirmed threats to aggregate all related incidents
- Automatically “claws back” malicious messages from all impacted inboxes
- Integrates with common Security Awareness Training solutions to turn user awareness into user engagement