A couple of days ago, we received a spam email sample that was reported to contain a malicious attachment. The email content poses as a piece of remittance advice for a specific BACS payment.
What is BACS Remittance Advice?
So, let’s explore the definition of BACS remittance advice. In essence, BAC remittance advice is a document that acts as proof of payment, which is sent by a customer to a business. Typically, it is used when customers want to let a business know that their invoice has been fully paid. Remittance slips are essentially the same as cash register receipts. They are especially helpful when it comes time to match invoices with payments.
Since online payments have become more and more popular, remittance advice slips have become more unnecessary. However, once an invoice is paid, sending a confirmation email is always a good idea.
What is a BACS Payment?
BACS also known as Banker’s Automated Clearing Services, is a scheme used for the electronic processing of financial transactions within the UK. A BACS payment is a very common bank-to-bank transfer within the UK. There are two more well-known types of BACS payment – direct debit and direct credit.
Direct debit is where one party has permission to pull their money directly from the bank account of the other party. Direct credit is where a party deposits money in the owed party’s account. Since this scheme is used mainly in the UK, this suggests that victims of this spam campaign would be concentrated in this country.
Identifying Fake BAC Remittance Advice
Let’s take a look at some of the emails that were sent, which mimicked BACS remittance advice emails and delivered Dridex malware:
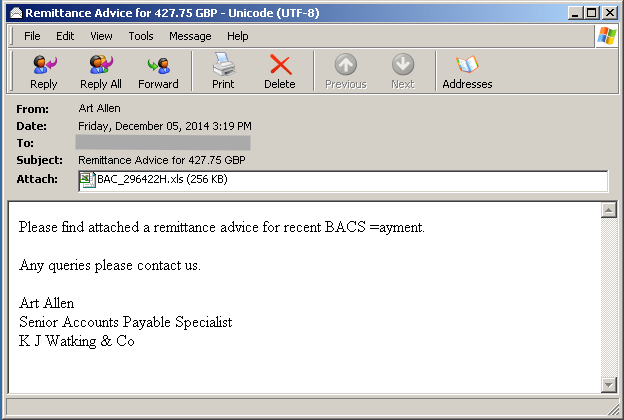
Figure 1. Email Snapshot
The attachment, BAC_296422H.xls, is an Excel document found to contain a malicious macro set to run automatically upon opening if macros have been enabled in Microsoft Office. Cyren detects this malicious document as X97M/DownldExe.A.
Once executed, the macro attempts to download and execute a WinPE file named “test.exe” from xx.xxx.xxx.xxx:8080/stat/lld.php. Cyren detects this downloaded executable as W32/DridLd.A.
W32/DridLd.A is a downloader component of the Dridex malware, dubbed as the successor to the Cridex family of banking Trojans, which steals online banking information via HTML injections.
The downloader component poses as a Windows component, which makes it more suspicious once you see it’s internal and original filename are of DLL type while its file type is Win32 EXE.
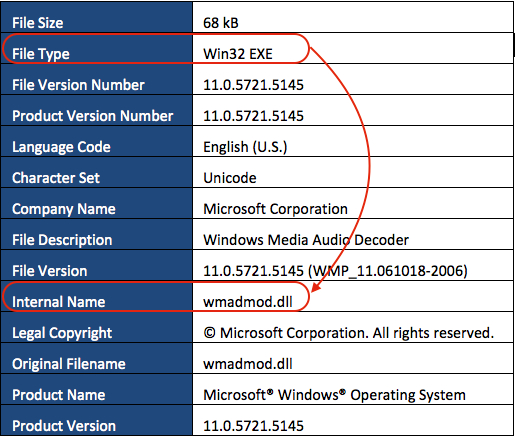
Table 1. W32/DridLd.A File Meta Information
Figure 2. Encrypted and compressed downloader binary
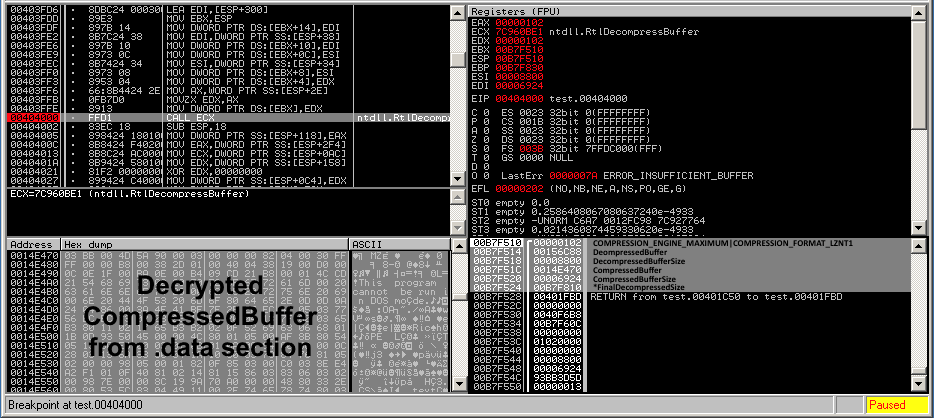
Figure 3. Downloader unpack Routine
The unpacked executable’s .sdata section contains the encrypted and compressed server config, which lists the servers where the main Dridex component would be downloaded from.
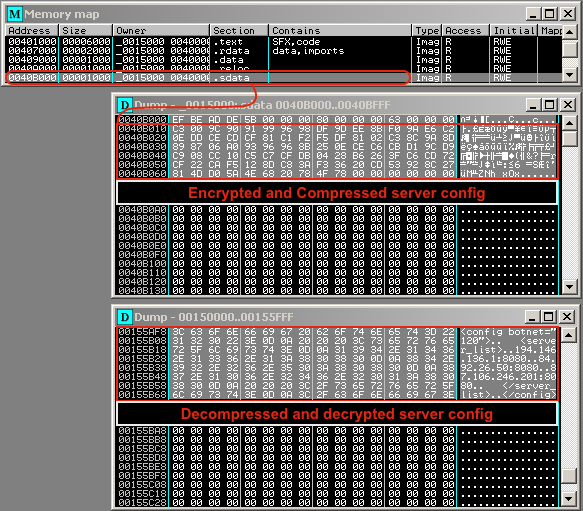
Figure 4. Decoded downloader server config
- Windows Version
- Computer Name
- User Name
- Installation Date
- Application names and versions enumerated from HKLMSoftwareMicrosoftWindowsCurrentVersionUninstall
The malware then builds a data buffer in XML format as shown below
<loader><get_module unique=”v1″ botnet=”v2″ system=”v3″ name=”bot” bit=”v4″/><soft><![CDATA[v5]]></soft></loader>
Where:
v1 = %ComputerName%_%MD5 of the checksum of UserName and InstallDate%
v2 = %Numeric Botnet ID% (125 in this case)
v3 = %Checksum(MajorVersion|MinorVersion|ServicePackMinor|ServicePackMinor|SuiteMask)%
v4 = %List of applications enumerated from Uninstall key delimited by “;”%
The malware now sends a POST request to a server listed in its server config, using the encrypted XML data containing the stolen information. The encryption uses simple XOR operation using “x” as the key.
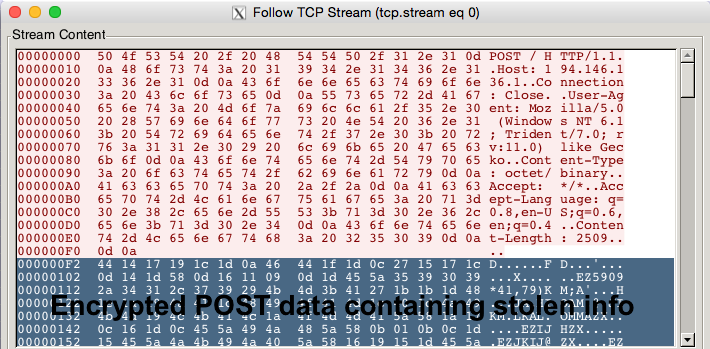
Figure 5. POST Request
It would receive a reply from the contacted botnet server with an encrypted XML data, which could be decrypted using the same XOR operation.
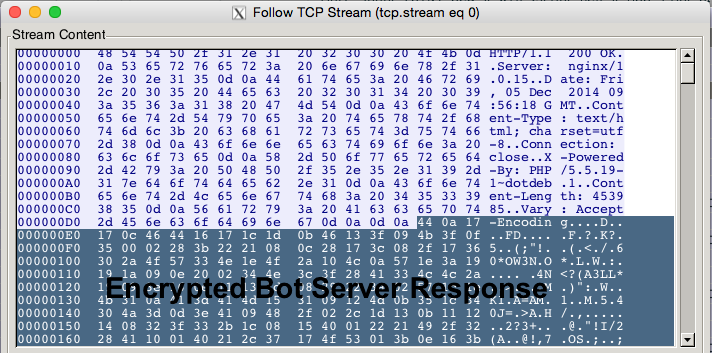
Figure 6. Bot server response
The decrypted response includes the main DLL component of the Dridex malware, which is then saved into the current directory where the downloader was executed as XX.tmp where XX are varying characters (15.tmp in this case).
The main component, which Cyren detects as W32/Dridex.A, poses as a Microsoft library named MFC110CHS.DLL as shown below:
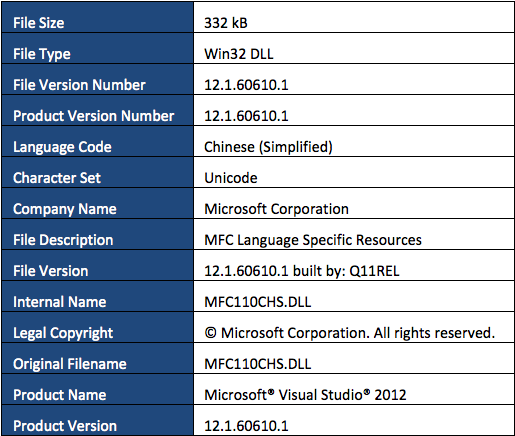
Table 2. W32/Dridex.A File Meta Information
Just like the downloader component, W32/Dridex.A’s main component is packed using the same compression method. Once unpacked the .sdata section also contains compressed data, this time a public key as shown below.
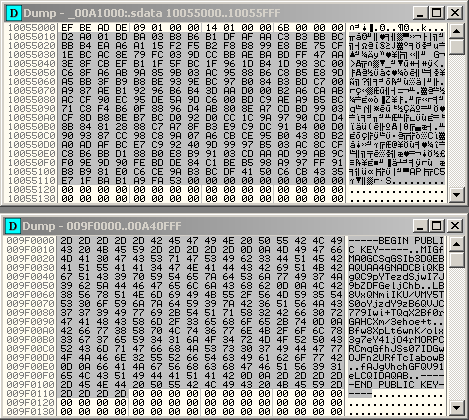
Figure 7. Decoded public key
The main component is loaded by calling rundll32.exe with the following syntax:
rundll32.exe %path to Dridex DLL% NotifierInit
Calling the main component’s exported function NotifierInit injects a copy of itself into explorer.exe before deleting its own file to further avoid detection from security scanners.
Once running in explorer.exe’s context it starts to perform its malicious behaviors by monitoring the following browser activities:
- Internet Explorer
- Chrome
- Firefox
It has the capability to perform the following spyware behaviors:
- Grab screenshots
- Log keystrokes
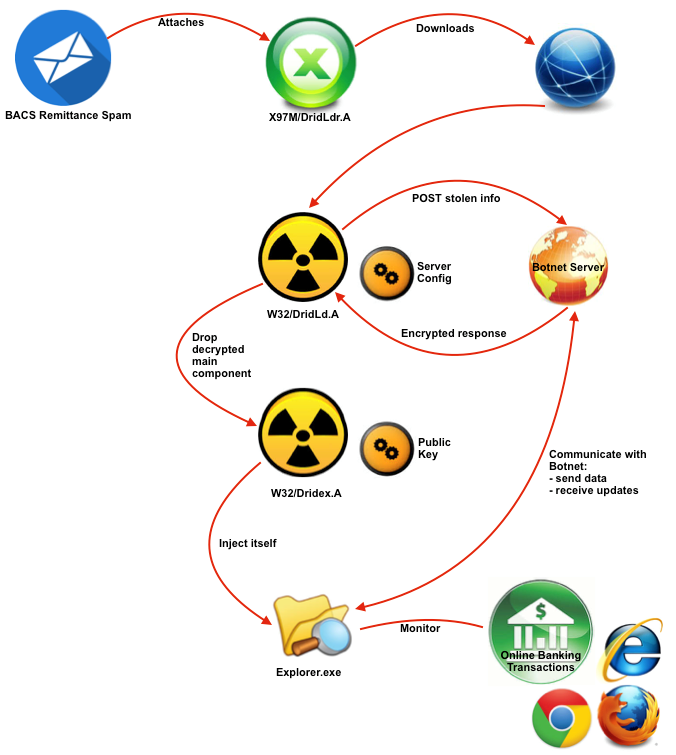
Figure 8. Dridex Infection Chain Overview
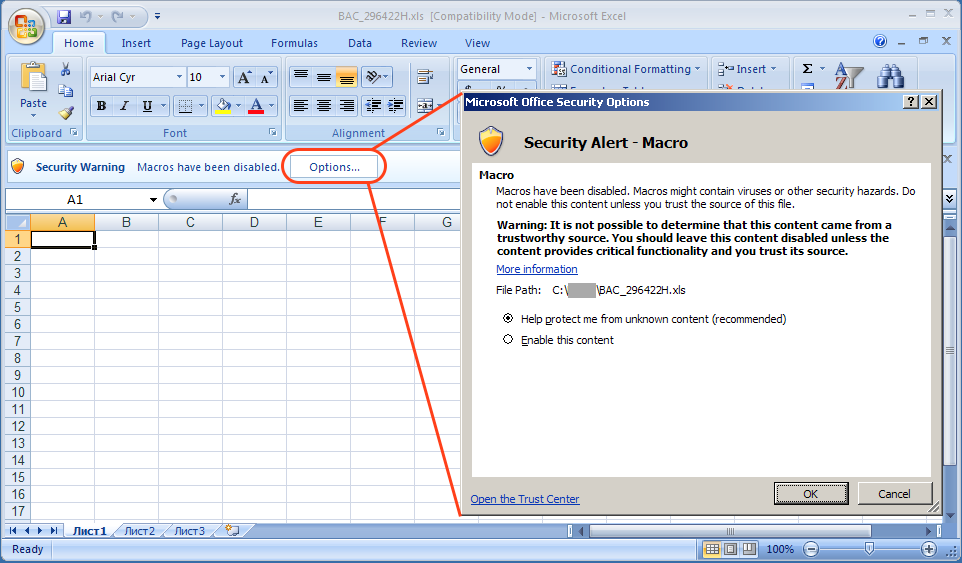
Figure 9. Microsoft Office Excel Security Alert for Macros
Avoid Future Malware Attacks From BAC Remittance Emails
In summary, the whole infection chain of Dridex relies on social engineering, which could be prevented by observing best practices in dealing with emails and documents.
Users can prevent macro-based malware from doing harm to their systems by making sure that macro security settings are enabled, IT administrators may also implement group policies to enforce these settings. Learn more about how Cyren Inbox Security for 365 can help your business avoid these types of malware attacks.