Password Protected Docs
One of the most recent Emotet samples we received were emails with password protected attachments. Although the malicious document needs an extra step to be accessed compared to just being attached as it is, the additional layer of ‘security’ may cause an unsuspecting user to think that this came from a legitimate source.
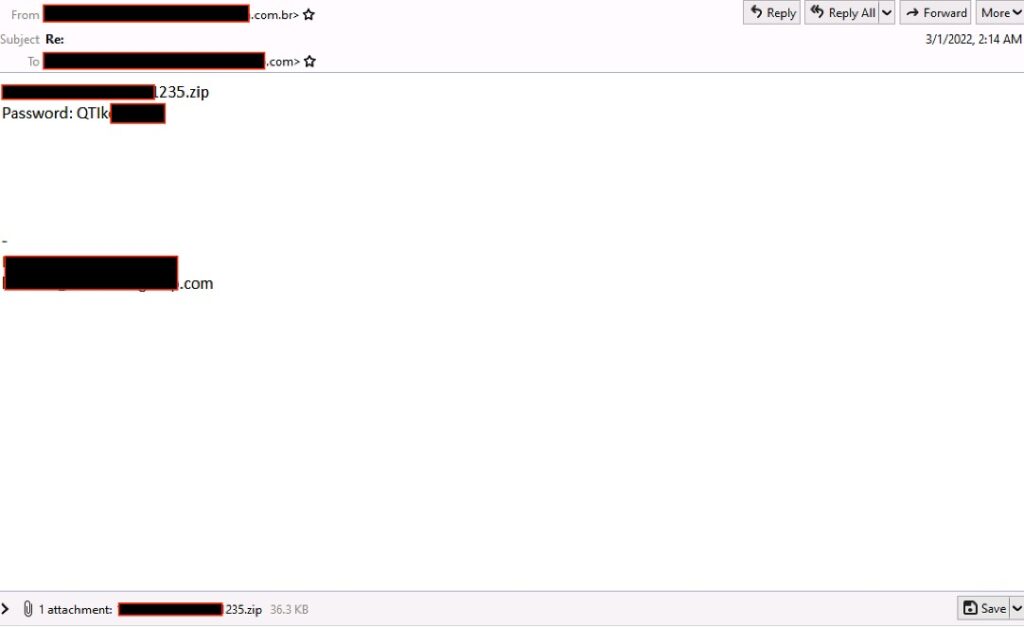
Figure 1. Email sample
Same Code, Different Types
Emotet downloaders are leveraging the different file types of excel. The two examples below have the same macro code but one is an OLE format Excel file (.XLS) and the other is an XML-based Excel file (.XLSM). The difference between the two is the URL list it will use to download the main Emotet payload. As for your typical macro malware, an image is used to convey the instruction to “enable macros”.
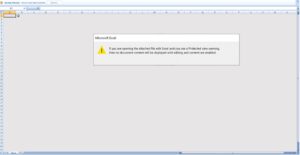
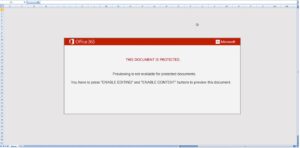
Figure 2. Both samples included prompts for the user to enable macros. The left image is OLE format and the right image is XML format.
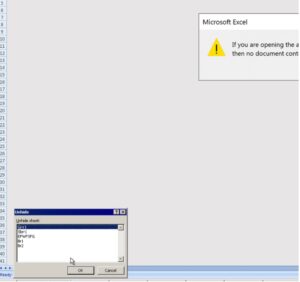
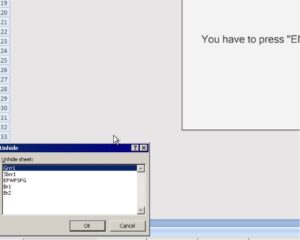
Figure 3. Both samples contained a hidden sheet with similar names


Figure 4. Macro source code
The font in red (Figure 4) is the malicious macro code found in the AUTO_OPEN of both Excel files. The font in green is the decoded excerpt of the code. They both have similar macro code but use differrent URLs to download the main binary payload.
Evasion
Aside from changing the download URLs of the emotet binary payload, the strings used by the malware are modified from time to time to evade detection that relies on matching strings to identify malware. The images below are from a sample associated with an earlier wave and the other sample is from a more recent wave of attacks. Both samples have the same instruction message and hidden sheets. The newer sample splits the string for regsvr.exe and joins the substrings upon execution.
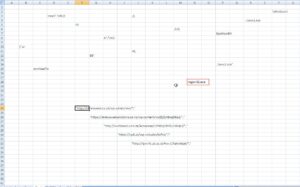
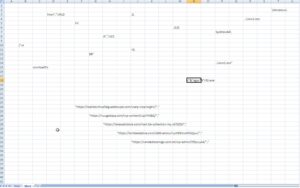
Figure 5. The left image is from an older sample. The right image is from recent samples.
Figure 6. The recent samples use a new image for the user prompt
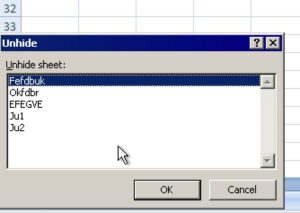
Figure 7. The recent samples also use new sheet names
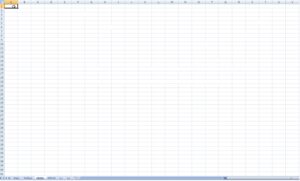

Figure 8. The left image is of the seemingly empty sheet. The right image reveals the hidden strings when the font color is changes from white to red.
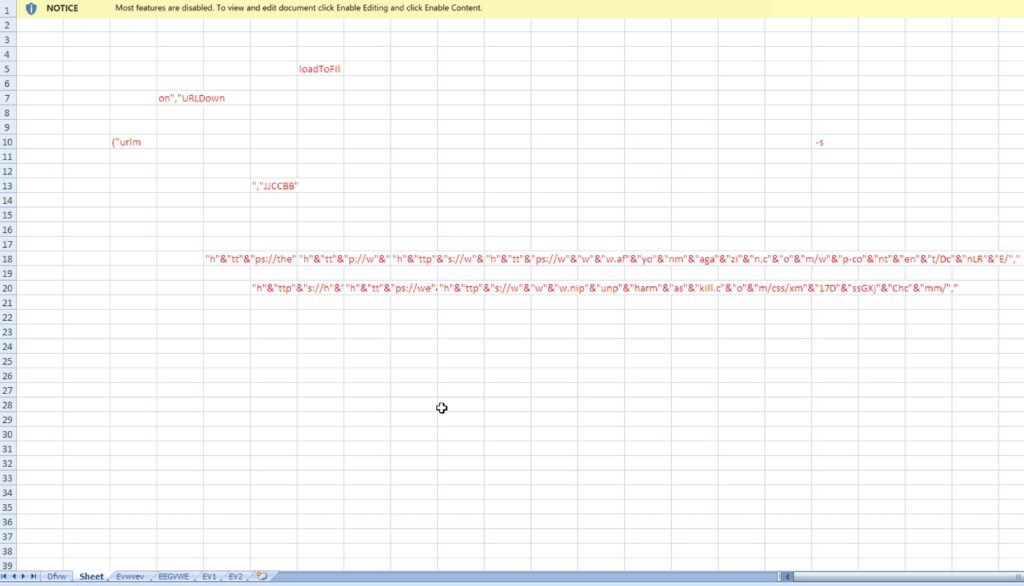
Figure 9. The URLs were placed in the “Sheet” tab with the image used to prompt the user to enable the macro. The URL and other strings were hidden using white font color.
Guidance, Detection and IOCs
It’s important to note this Emotet campaign includes the use of email to deliver the payload. It’s important to understand the limits of your current detection capabilities – including employees. If you haven’t evaluated your cyber threat intelligence providers recently, it’s never a bad time to survey the market for sources with more timely, more accurate, and more comprehensive malware threat intelligence. Make sure your malware detection engines are always using up to date definition files.
Cyren detects these samples as:
- XLSM/Downldr.A.aggr!Camelot
- XF/Emotet.B.gen!Eldorado
Indicators of Compromise (file hashes)
01019e5d292134b5cc7d04107e71eee5bbb96c9607686ad40a7092011593b5b3
6309a7e12e3647f12f50ff5bdf3450ffe9855ca062cf34fd5537bb91da74d22d
bbd95b19e8cf7b776b69062e99cb2609568ba23050a93904c46306827b82949d
234efc5c5c355aaa375461b56eef44a2b509dd25968fc76eb2e7f3e6396c2f40
db36207307284a28ac838dc4eb20ed98f2be8d31327504646229b0c11675efbd
