Looking back on 2014, it has been an incredibly dynamic year in the world of cyberthreats. It takes only two names to sum up the impact the cybercriminal had on the 2014 headlines: Home Depot and Sony. The Home Depot breach yielded about 110 million stolen pieces of sensitive information, including social security numbers and email addresses. And, in a classic case of hacktivism, Sony lost more than just emails and employee social security numbers; it suffered significant brand damage.
For more information and in-depth analysis of the major cyber threats in 2014, download a copy of CYREN’s Cyber Threats Yearbook
For some, these headlines say everything that needs to be said about cyberthreats in 2014. The headlines lead you to believe that cybercriminals are only targeting the “big guys” for their money and profile, and that everyone else is safe because the criminals aren’t going to bother unless you’re a Fortune 1000 corporation. Well, not quite. Enterprises of all sizes are now besieged by cybercrime at an alarming rate. In fact, during the four year period between 2010 and 2014:
-
The number of successful cyberattacks on businesses of all sizes increased by 144%.
-
The cost of cybercrime per company increased by 95%.
-
The average time to resolve incidents increased by 221%.

The problem with making companies like Home Depot and Sony the poster-children for cybercrime is that it gives the vast majority of businesses in the world the false impression that they won’t be targeted. But this perception couldn’t be further from the truth. When it comes to cybercrime, businesses regularly misjudge their risk profile because they misunderstand what is valuable to the cybercriminal. The game is money- driven and value can be extracted from many different types of data. In fact, stealing personally identifiable information (PII)—such as email addresses and social security numbers—is actually more lucrative than credit card number theft. Social security numbers can yield criminals millions of dollars. Email address lists can be sold to spammers and malware distributors. And, ultimately every enterprise holds some amount of PII data. At the same time, cybercriminals are getting more creative in their approach. Today’s cybercriminals are well-educated, sophisticated “crime professionals” with highly developed business networks that focus their efforts on threat innovation geared towards penetrating corporate systems.
So, as threats continue to evolve, the challenge for businesses isn’t the massive volume of known hreats, it is the smaller volume of unknown threats, like the malicious socially engineered phishing email, designed to look like it came from the HR department and sent to a handful of select employees to test the corporate defenses. But ultimately, protecting the business enterprise is about more than just algorithms or software. It’s about the data that powers the solution. With rapidly evolving distribution and attack methods, to be effective security solutions must employ a detection-based methodology that combines high-quality threat data
CYREN cyber intelligence powers the security solutions of over 200 global partners; we are the security provider to the security industry, and we specialize in creating solutions that identify and block previously unknown threats. The people at CYREN work day and night to increase the size, scope, and value of our data, enrich the level of analysis, and enhance and expand our solutions to ensure that enterprises can be protected from ever- encroaching cyberthreats. The cybercriminal thrives on threat innovation; at CYREN, we are committed to identifying and stopping cybercrime by innovating cybersecurity solutions with an even greater opposing force. Some of our newest advances include:
-
Making the massive cyber-intelligence that already powers the security industry available direct to businesses or enterprises, through a cloud-based web security solution
-
Pioneering a detection method that leverages our massive database to identify and stop advanced persistent threats as early as possible
-
Using our deep and broad global threat data, to find new ways to understand the subtle differences between cybercriminal, legitimate user, and machine behavior patterns to create security solutions that protect the enterprise on all levels
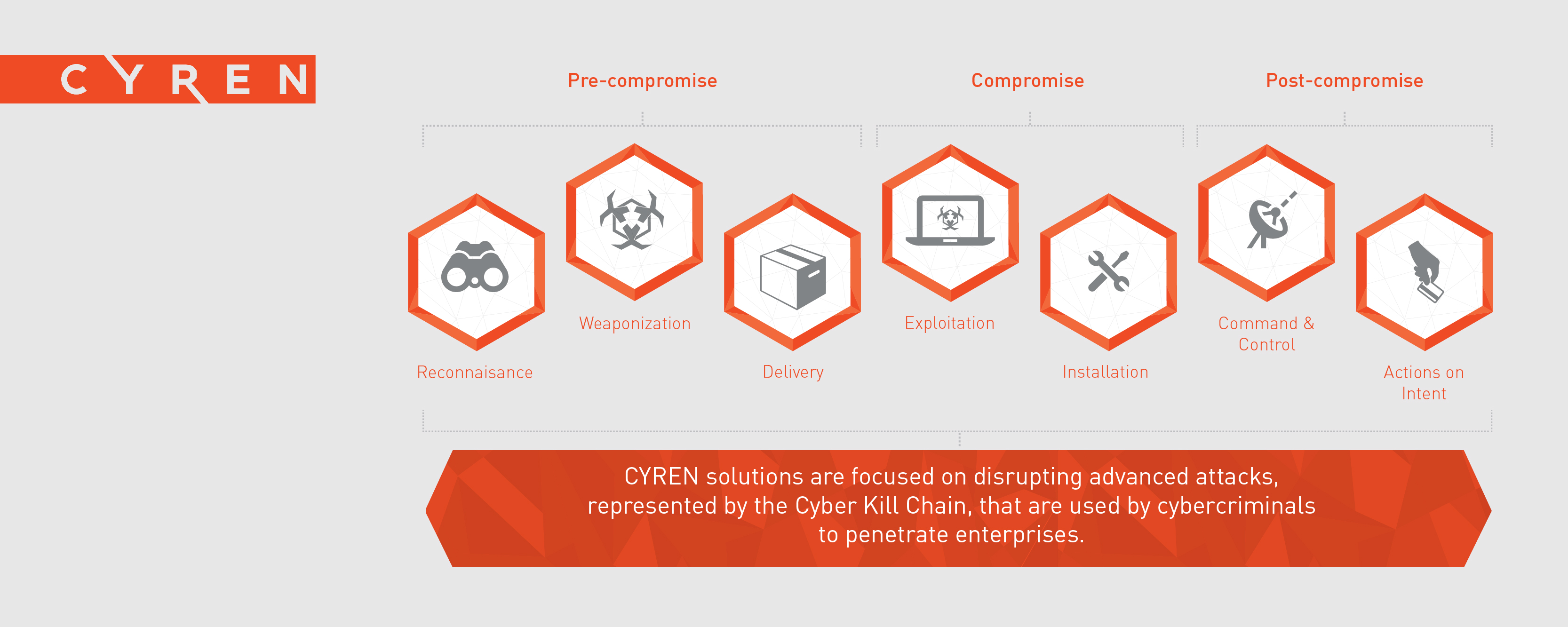
In CYREN’s Cyber Threats Yearbook, along with the numbers, we present an in-depth analysis of individual threats captured by CYREN in 2014 to illustrate how the cybercriminals engage in the business of crime, how they target the business enterprise, and what CYREN is doing to halt the advance of cybercrime in its tracks.