Phishing links are harmful or misleading links that are disguised in an attempt to make them look safe and normal. These links usually lead to a fake website and entice you to enter sensitive information. Other links can also contain malware, which could give cybercriminals access to all your stored data.
Earlier this month, we witnessed a phishing link attack on CIMB Clicks bank customers in Malaysia which combined some common social engineering techniques (scare tactics) with some newer technical misdirection techniques (TinyURL). We decided to provide a detailed blow-by-blow on how this particular TinyURL scam worked.
The CIMB Clicks site, which is the online banking portal for CIMB bank, offers customers online banking, insurance, and share trading services. Customers can also pay bills, inquire about account balances, and conduct other financial transactions.
Common Phishing Link Scam Tactics
The CIMB Clicks phishing scam employs two increasingly common techniques to entice the victim into participation. First, the language in the attached documents attempts to ‘scare’ the customer into thinking that access to their CIMB accounts has been restricted. Second, the scam obfuscates the fake phishing link by converting it into a shortened URL using a URL-shortening web service, like TinyURL.
Cyren detects these phishing documents as: “XML/Phish.H “ for the fake MSWORD CIMB Document and “PDF/Phish.EVZ “ for fake PDF CIMB Document.
Cyren Analysis—CIMB Clicks Phishing Link Scam
The following images show what the fraudulent MSWord and PDF documents look like when opened by the recipient.
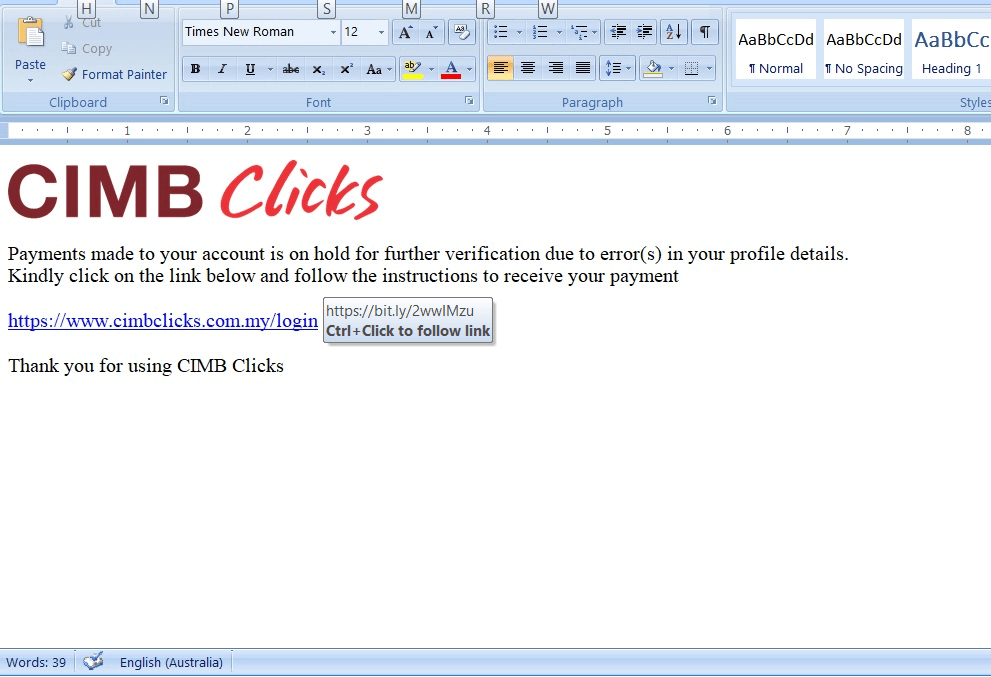
Figure 1: Fake MSWORD CIMB Document
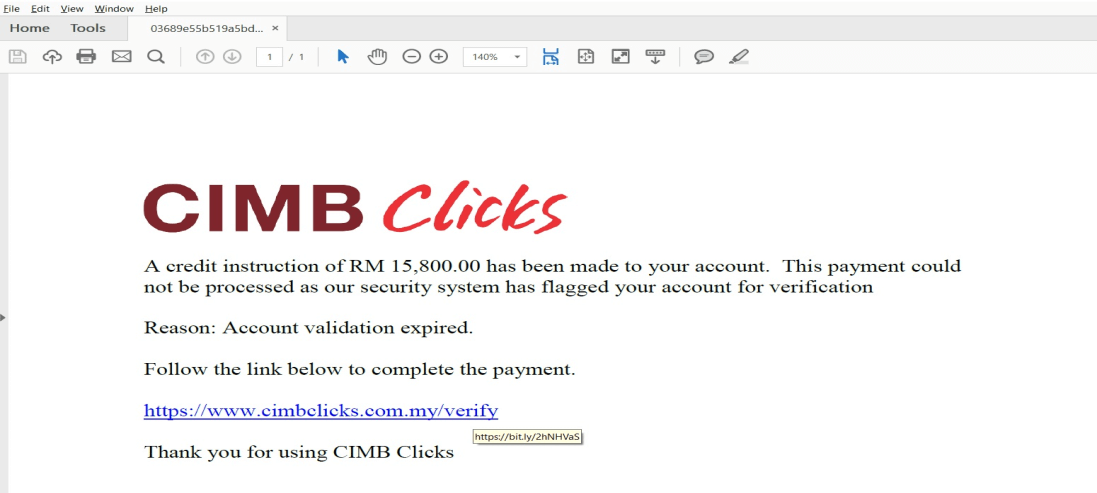
Figure 2: Fake PDF CIMB Document
HTTP Redirection Using URL Shortening Web Service
Clicking the highlighted URL link leads to the following HTTP redirection (Figure 3 below). You will notice that the URL link appears as a shortened URL via “bit.ly”. Increasingly, we are noticing that criminals are obfuscating their malicious links using URL-shortening web services, such as bitly.com and tinyurl.com. By using the shortened URL, the criminal is able to prevent the victim from hovering over the link to see that the URL destination is not actually the one intended.
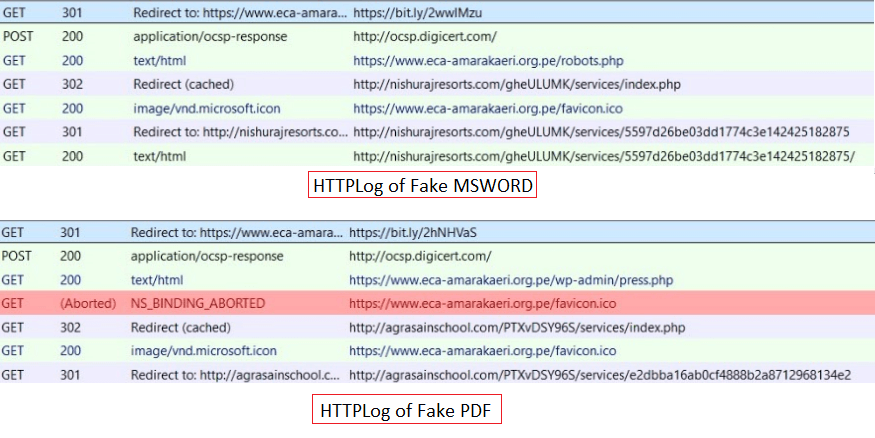
Figure 3: HTTPLog Redirection
A Neverending Loop
Following is the process once the victim arrives on the Fake CIMB Clicks site (Figure 3). Notably, during the last phase, there is an infinite loop while capturing the email address.
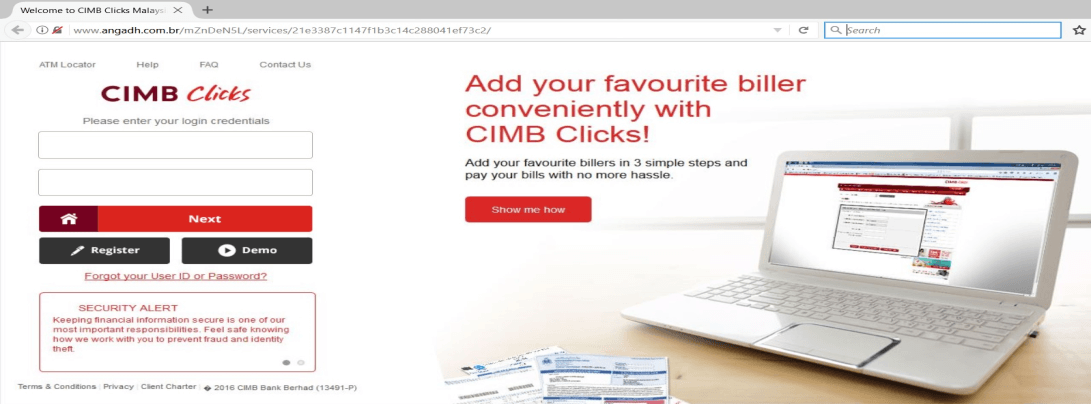
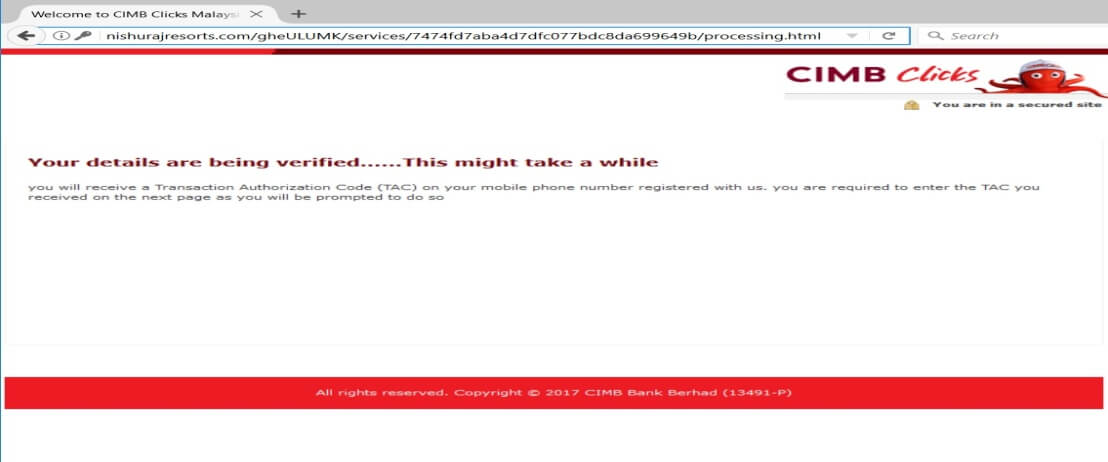
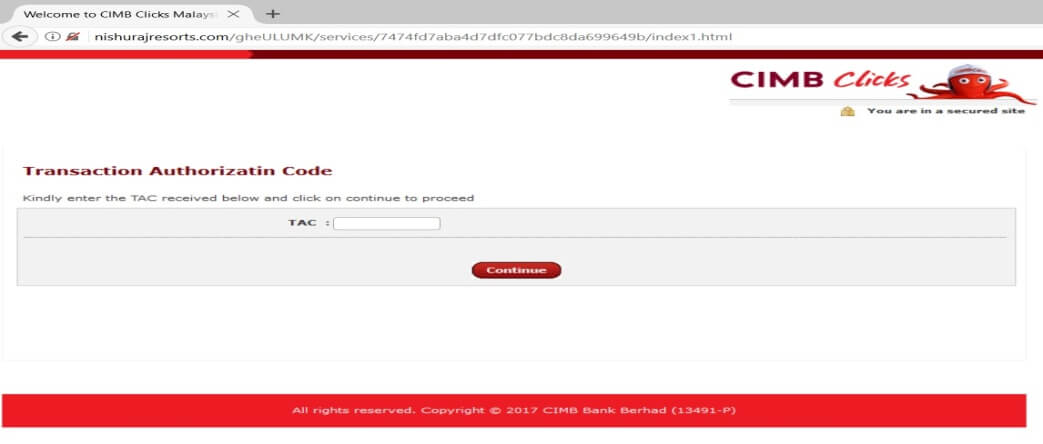
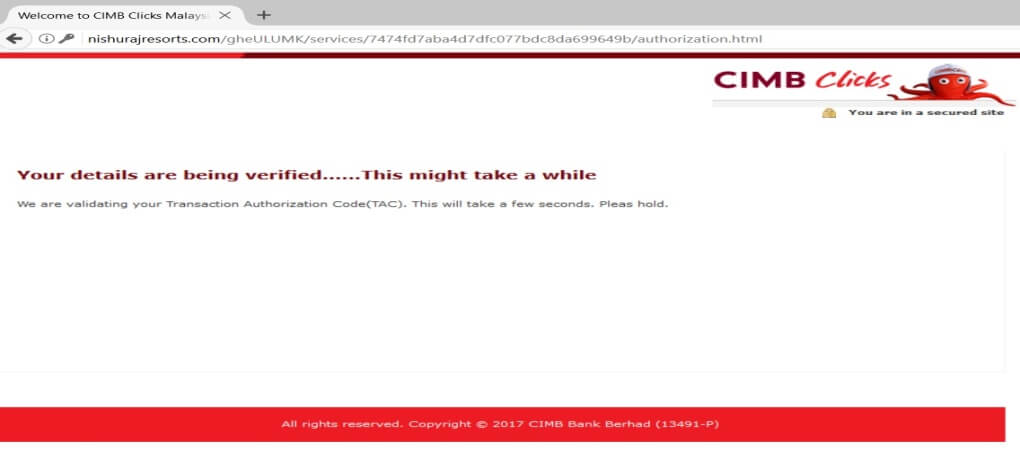
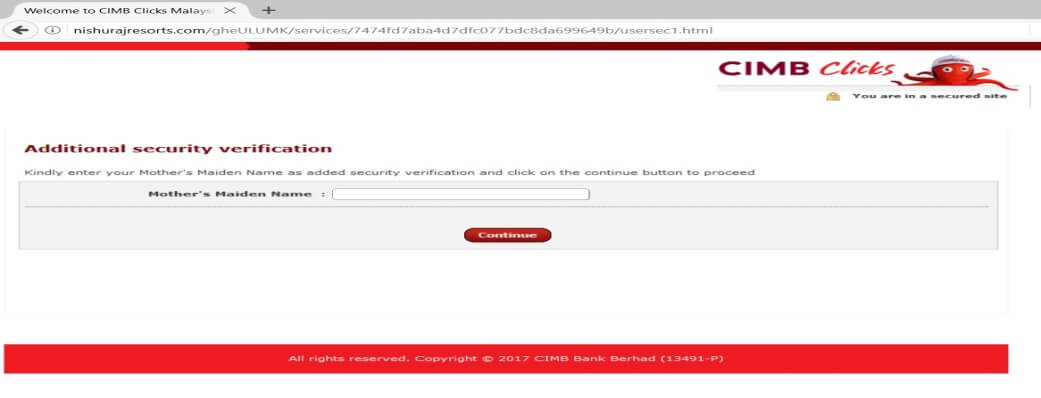
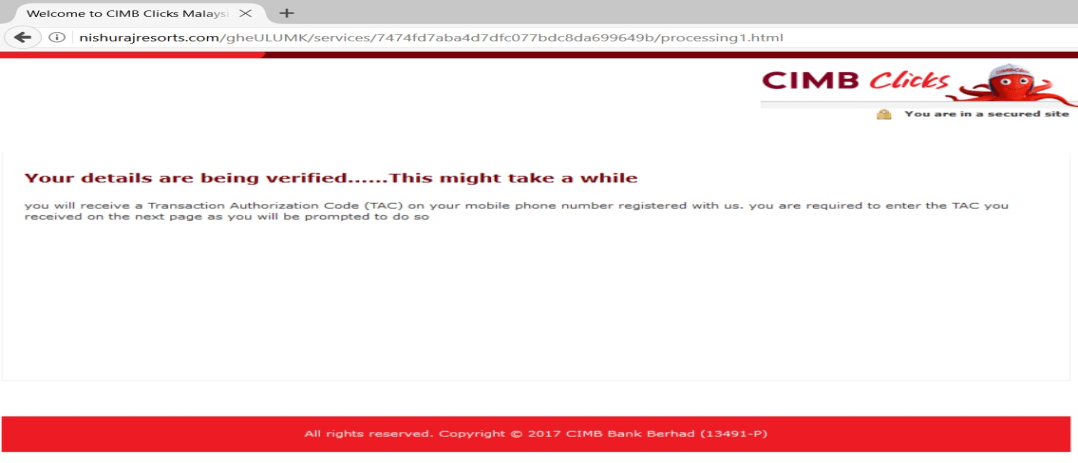
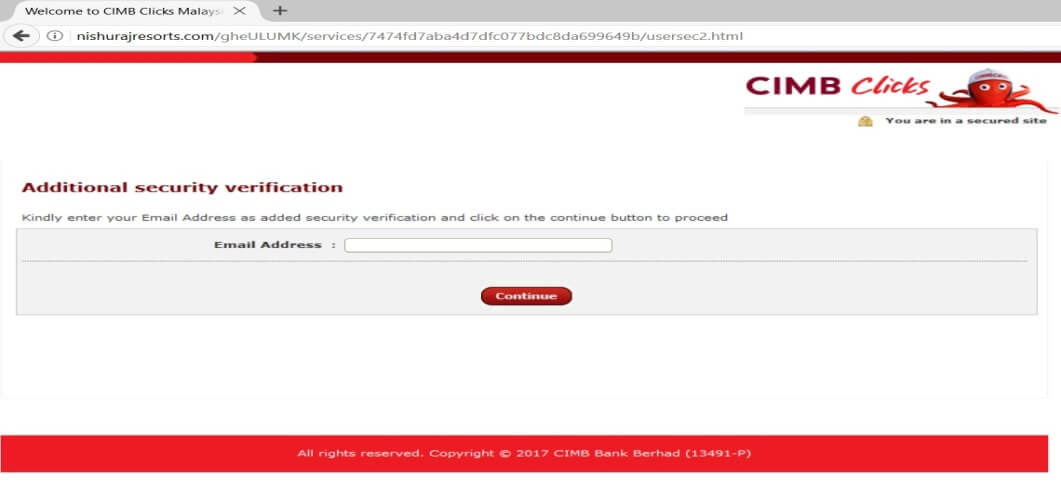
Figure 4: Infinite loop in the fake CIMB Clicks credentials capturing process
The phishing domains lead to these IP addresses 198.50.156.168 which belongs to OVH Hosting and 198.38.82.230 which belongs to “Mochahost.com” as seen in the images below.
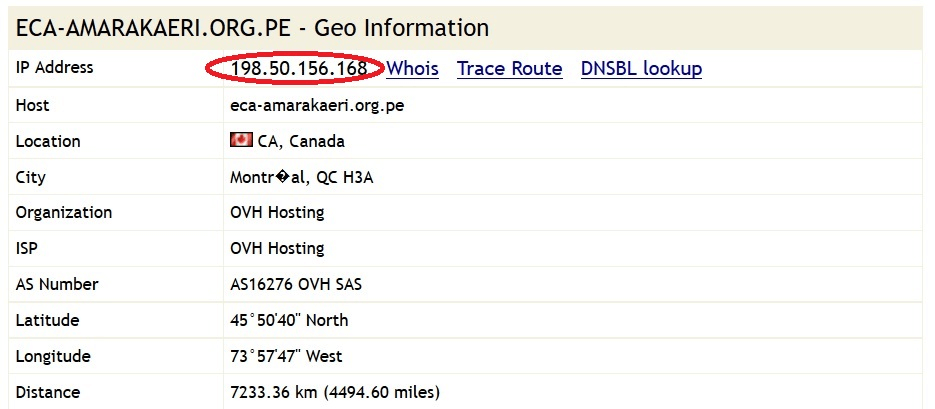
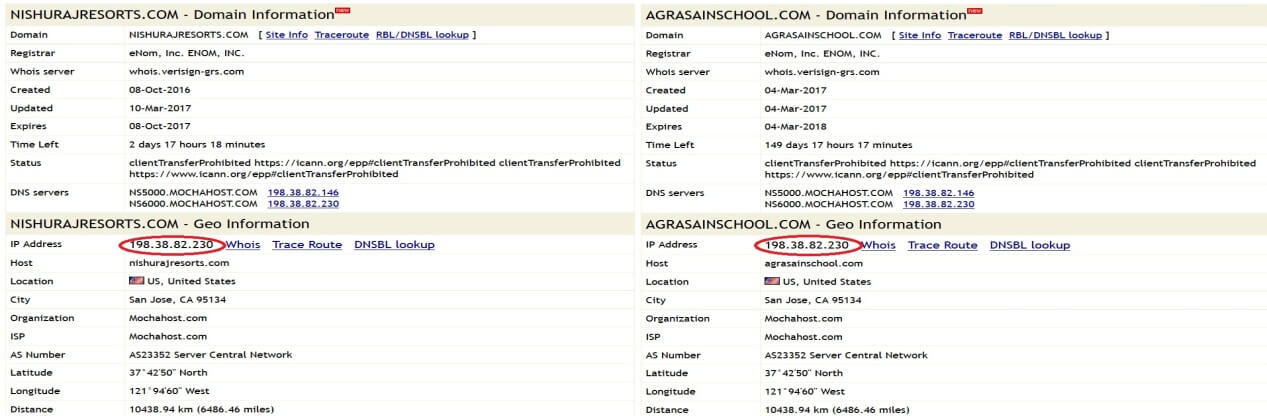
Figure 5: WHOIS IP of Phishing Domains
Key Takeaways on How to Identify & Spot Phishing Links
1. Check the URL
Make sure the URL starts with “https://”. The letter S at the end of HTTP means the website has an SSL certificate installed. You still have to be cautious because SSL certificates are not hard to obtain. Phishing links will also resemble the legitimate website as closely as possible. Additionally, hovering over the link allows you to preview it without clicking.
2. Check the Content
Most legitimate websites will look like they’ve been lived in. Contact information should be present and grammar should be spot on. If it’s hard to find contact information and the content is written poorly, this is a red flag.
3. Who Owns the Website?
Doing a simple WHOIS lookup can help you find information about the website owner. Things to look for are creation date, IP address, and IP location. Many phishing attacks using brand new domains.
4. What Payment Methods Are They Using?
Never enter payment information on a website you haven’t vetted. Most websites will use popular payment services like PayPal. If a website only asks for a bank transfer, run for the hills.
5. Read Reviews
Simply type your search query plus the word scam or review into Google. People don’t like getting burned by phishing links and others will likely post their experiences online.
6. Check the Sender’s Email Address
A common tactic cybercriminals use is slightly altering the domain of a reputable company so they can convince you they are legitimate. They might use a combination of a popular company name alongside a public domain to lure you in. You’ll want to check twice for any errors or inconsistencies.
7. Are you Being Asked for Personal Information?
Be wary of emails or pages that ask for sensitive information such as social security number, bank details, or tax return information. Even personal questions such as your first pet’s name, favorite color, or the middle school you attended. Those questions are commonly asked when another form of authentication is required during a login attempt.
8. Sense of Urgency
Does the message urge you to take immediate action before it’s too late? This is a common play on your emotions and cybercriminals know its effectiveness. This is why we recommend enabling a 2FA (two-factor authentication) on all your accounts. This adds a second layer to an authentication process. A personal code will be sent to your cellphone and it has to be used in order to log in.
9. Are There a Lot of Pop-Ups?
In this day and age, very aggressive pop-up windows are not as common. A good practice is to never enter sensitive information on these pages. There should always be a secure page and a pop-up window screams non-professional.
Final Thoughts
Stop phishing attacks with an anti-phishing solution such as Cyren Inbox Security which continuously monitors mailboxes and automatically remediates advanced email threats that evade secure email gateways. Request a demo today!