Phishing attacks have seen considerable growth over the past few years. Here are just a few of the astounding facts:
- In 2013, CYREN observed a 264% increase in phishing scams.
- Almost 70% of all IT professionals observe and experience a phishing attack at least once a week.
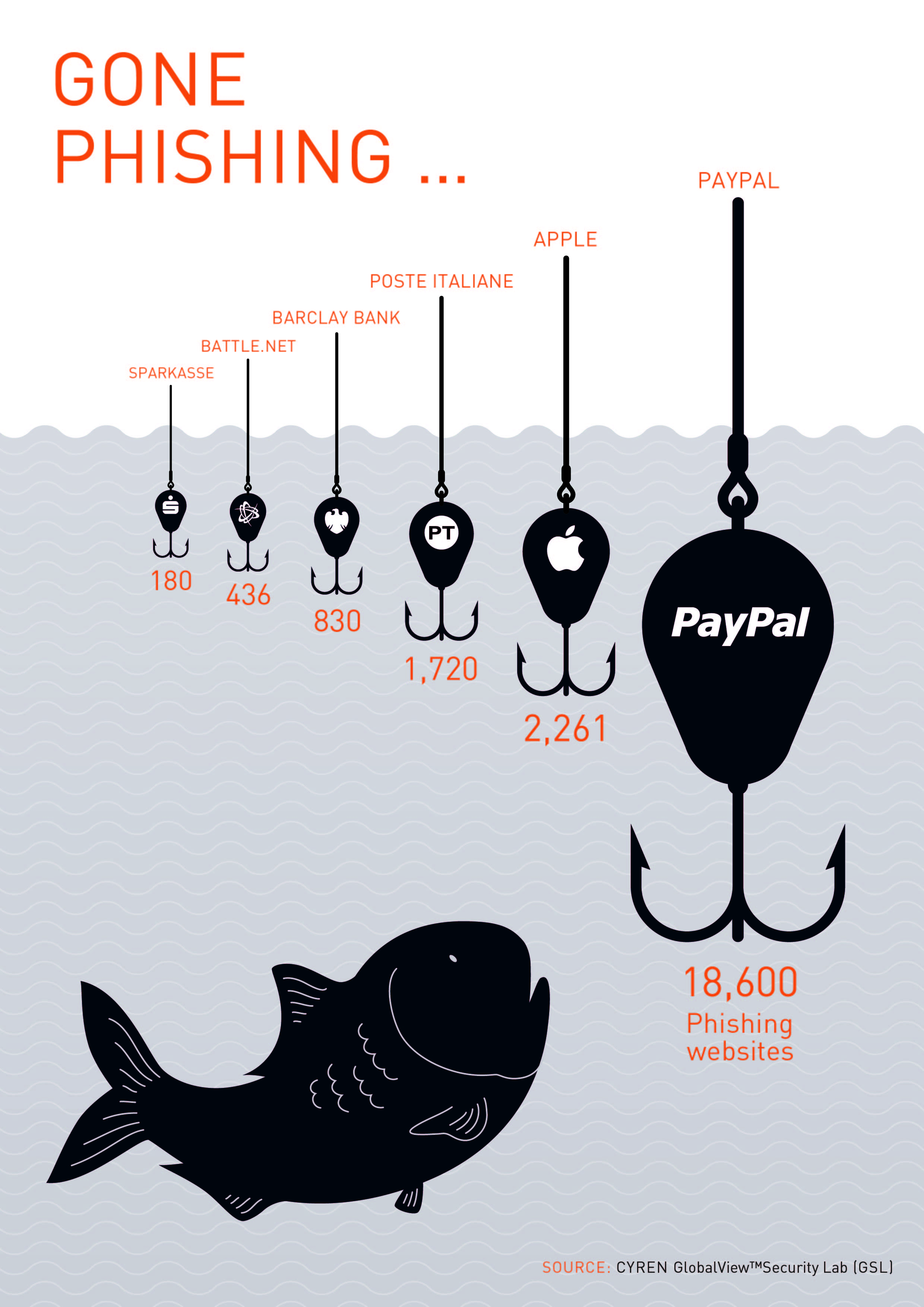
- PayPal remains the #1 target of phishing, with over 1,000 new PayPal phishing sites every day.
The total phishing-related losses for organizations can range from millions to billions of dollars, depending on the scope and scale of the data “phished.” Individuals are seeing personal and private information stolen and distributed across the Internet. Ironically, while the USA and China are the biggest targets of phishing attacks, they are also consistently among the top countries of origin for attacks.
Email is a critical vector of phishing scams. By faking messages from well-known services, social networks or financial organizations, phishers are able to significantly improve the chances of their phishing being successful. Increasingly though, phishing attacks are exploiting new channels, such as social media and mobile platforms, due to their large use by online users.
Awareness, information sharing, and education on how users can recognize phishing attempts are essential to mitigate this type of cyberthreat. Combined with the adoption of effective countermeasures and technologies, you can minimize the risks to you and your company.
Effective Solutions to Successfully Combat Phishing Attacks
Effective point solutions such as the CYREN Phishing URL Feed are extremely powerful and can be implemented within minutes. These solutions provide an organization with real-time updates on phishing site URLs. Whether you are an enterprise, SecaaS provider or appliance vendor, a phishing feed is instrumental in supplementing an existing threat intelligence database.
In addition to adding a phishing feed to your solution offerings, layering your cybersecurity with anti-spam and URL filtering technology can further block not only run-of-the-mill diet and pharmaceutical spam, but also stop phishing scams, and also categorize websites into various security categories.