You receive an email (purportedly from Amazon.de) informing you that to protect your identity they would like to give you a new Amazon email address. Amazon.de assures you that their system is fraud-proof, as they use advanced filtering techniques to prevent unwanted emails. Further, they remind you that if you update your email address, Amazon will retain all emails sent to this new address, in accordance with their “A-to-Z Guarantee”. All you need to do is click below and respond to the email.
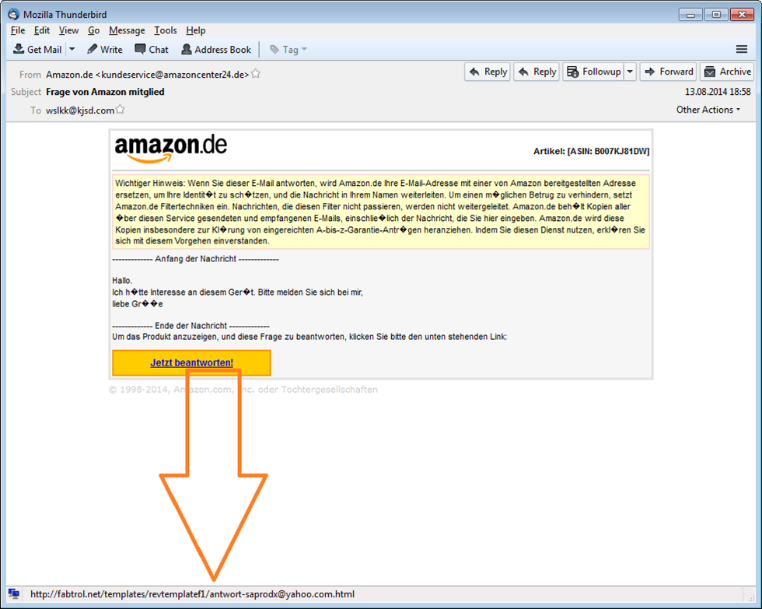
The email uses the same graphics as you typically see on the Amazon.de website and the message is well written. The A-to-Z Guarantee is a real Amazon service.
However, when you hover over the “Just Respond” button, you see a link to a company called Fabtrol. Fabtrol is, in fact, a legitimate company specializing in software for steel manufacturing.
The link goes to a HTML page which is base64 encoded:
<html>rn<head>rn<meta http-equiv=”refresh” content=”0;URL=data:text/html;base64,DQoNCg0KDQoNCiAgDQogICAgPCFET0NUWVBFIGh0bWw+IA0KICAgIDxodG1sPg0KICANCiAgDQoNCg0KPGhlYWQ+DQoNCg0KPHNjcmlwdCB0eXBlPSd0ZXh0L2phdmFzY3JpcHQnPnZhciB1ZV90MD11ZV90MHx8K25ldyBEYXRlKCk7PC9zY3JpcHQ+DQo8c2NyaXB0IHR5cGU9J3RleHQvamF2YXNjcmlwdCc+DQp2YXIgdWVfaWQgPSAnMThDQzg4S04yS1g0M1M4RzI2Q1MnLA0KdWVfY3NtID0gd2luZG93LA0KdWVfdXJsID0gJy9hcC91ZWRhdGEnLA0KdWVfcHIgPSAnMCcsDQp1ZV9tZCA9ICcvYXAvdWVkYXRhLz90cD0nLA0KdWVfbmF2dGltaW5nID0gMSwNCnVlX21pZCA9ICdBMVBBNjc5NVVLTUZSOScsDQp1ZV9zaWQgPSAnMjc1LTU0NTQzMjAtNzczNjczNycsDQp1ZV9mdXJsID0gJ2Zscy1kZXZvLnZpcGludGVnLmFtYXpvbi5jb20nOw0KDQoNCg0KdWVfY3NtLnVlX2hvYj11ZV9jc20udWVfaG9ifHwrbmV3IERhdGUoKTsoZnVuY3Rpb24oZixhKXt2YXIgYj0iRkFUQUwiLGM9e2VjOjAsZWNmOjAscGVjOjAsdHM6MCxlcmw6W10sbXhlOjUwLHN0YXJ0VGltZXI6ZnVuY3Rpb24oKXtjLnRzKys7c2V0SW50ZXJ2YWwoZnVuY3Rpb24oKXtmLnVlJiYoYy5wZWM8Yy5lYykmJmYudWV4KCJhdCIpO2MucGVjPWMuZWN9LDEwMDAwKX19O2Z1bmN0aW9uIGUoaSxoKXtpZihjLmVjPmMubXhlfHwhaSl7cmV0dXJufWMuZWMrKztoPWh8fHt9O3ZhciBnPWkubG9nTGV2ZWx8fGgubG9nTGV2ZWw7aWYoIWd8fChnPT1iKSl7Yy5lY2YrK31oLnBhZ2VVUkw9IiIrKGEubG9jYXRpb24/YS5sb2NhdGlvbi5ocmVmOiIiKTtoLmxvZ0xldmVsPWc7aC5hdHRyaWJ1dGlvbj1pLmF0dHJpYnV0aW9ufHxoLmF0dHJpYnV0aW9uO2MuZXJsLnB1c2goe2V4OmksaW5mbzpofSl9ZnVuY3Rpb24gZChsLGssZyxpLGgpe3ZhciBqPXttOmwsZjprLGw6ZyxjOiIiK2ksZXJyOmgsZnJvbU9uRXJyb3I6MSxhcmdzOmFyZ3VtZW50c307Zi51ZUxvZ0Vycm9yKGopO3JldHVybiBmYWxzZX1kLnNraXBUcmFjZT0xO2Uuc2tpcFRyYWNlPTE7Zi51ZUxvZ0Vycm9yPWU7Zi51ZV9lcnI9YzthLm9uZXJyb3I9ZH0pKHVlX2NzbSx3aW5kb3cpO3VlX2NzbS51ZV9ob2U9K25ldyBEYXRlKCk7DQoNCg0KDQoNCg0KDQoNCnVlX2NzbS51ZV9ob2I9dWVfY3NtLnVlX2hvYnx8K25ldyBEYXRlKCk7KGZ1bmN0aW9uKGYsbCl7Zi51ZWluaXQ9KGYudWVpbml0fHwwKSsxO3ZhciBjPXt0MDpsLmFQYWdlU3RhcnR8fGYudWVfdDAsaWQ6Zi51ZV9pZCx1cmw6Zi51ZV91cmwscmlkOmYudWVfaWQsYToiIixiOiIiLGg6e30scjp7bGQ6MCxvZTowLHVsOjB9LHM6MSx0Ont9LHNjOnt9LGllbDpbXSxpZWxmOltdLGZjX2lkeDp7fSx2aXo6W10sdjozMixkOmYudWUmJmYudWUuZCxsb2c6Zi51ZSYmZi51ZS5sb2csbHI6Zi51ZSYmZi51ZS5scn07Zi51ZT1jO2Z1bmN0aW9uIGgobSl7cmV0dXJuIGYudWVfZnBmK2VuY29kZVVSSUNvbXBvbmVudChtKSsiOiIrKCtuZXcgRGF0ZSgpLWYudWVfdDApfWYudWUudGFnQz1mdW5jdGlvbigpe3ZhciBtPVtdO3JldHVybiBmdW5jdGlvbihuKXtpZihuKXttLnB1c2gobil9cmV0dXJuIG0uc2xpY2UoMCl9fTtmLnVlLnRhZz1mLnVlLnRhZ0MoKTtmLnVlLmlmcj0oKGwudG9wIT09bC5zZWxmKXx8KGwuZnJhbWVFbGVtZW50KSk
When you click the link, you are taken to a site that looks like a standard Amazon login page. Of course, this isn’t a real Amazon login page. All the personal information you enter will go to the Fabtrol website.
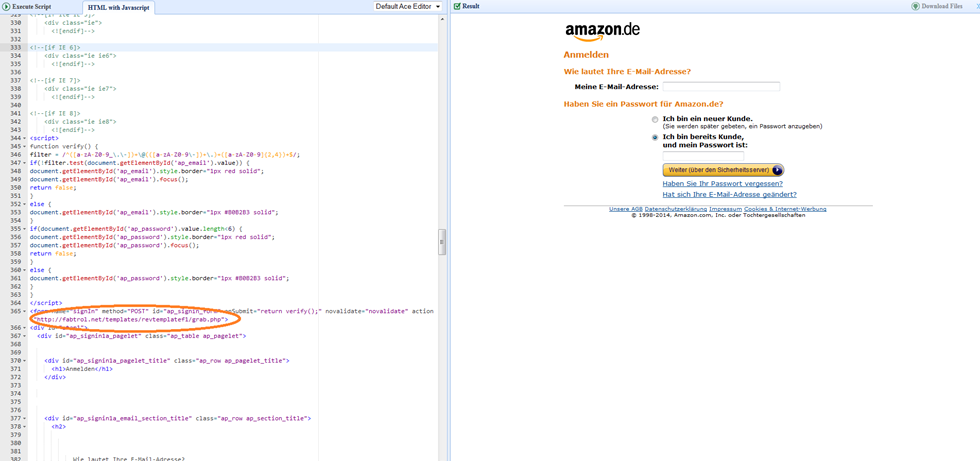
While Fabtrol may be a legitimate company, its cybersecurity systems have been compromised and the content management system on the Fabtrol website hijacked. Cybercriminals are now using the Fabtrol content management system to place automated software; in the foreground the Fabtrol system appears to run normally; in the background cybercriminals are using the Fabtrol content management system to collect the phishing script data entered by unsuspecting Amazon.de victims.
Always keep your CMS and plugins updated to avoid such site hacks.