There has been much speculation in the Internet Security industry about the status of Locky – the ransomware heavyweight of February-May 2016 which suddenly ceased distribution at the start of June. As we previously reported Locky was distributed in vast email outbreaks, many times exceeding 10 billion emails/day and often with hundreds of thousands of variants. The current theories for the sudden drop:
- The Necurs botnet responsible for Locky distribution was taken down or ceased activity. (see Proofpoint blog here)
- It was the result of the arrest by Russian authorities of 50 hackers involved in distributing the Lurk Trojan. This does not seem logical to us since the Lurk Trojan targeted Russian and Ukrainian financial institutions, but Locky was super careful to avoid Russian victims, uninstalling itself upon detection of a Russian language pack.
- One of the Locky “team” pulled out and the other team members needed to recover access to the relevant resources or create parts of their backend infrastructure anew.
In any event, Locky variants are once more being distributed as of June 22 – but with subtle “technological improvements”:
- The JavaScript (JS) downloader uses 3 layers of obfuscation. It is now very similar to that of Nemucod – a known JS downloader raising speculation that Locky is being distributed by another group, or that the Locky gang have adapted Nemucod, or that various groups are working together.
- The ransomware will only run as executed by the JS downloader – this prevents sandbox analysis of the ransomware on its own (it simply does not execute)
Detailed Analysis
On June 22, 2016 GMT+8, we started receiving these invoice-themed emails which had zipped javascript attachments. Shown below are some sample emails which belonged to this campaign:
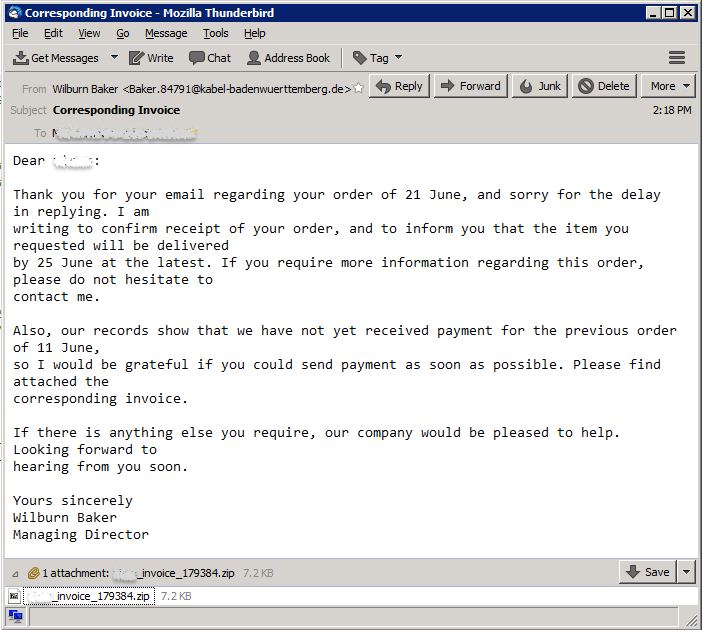
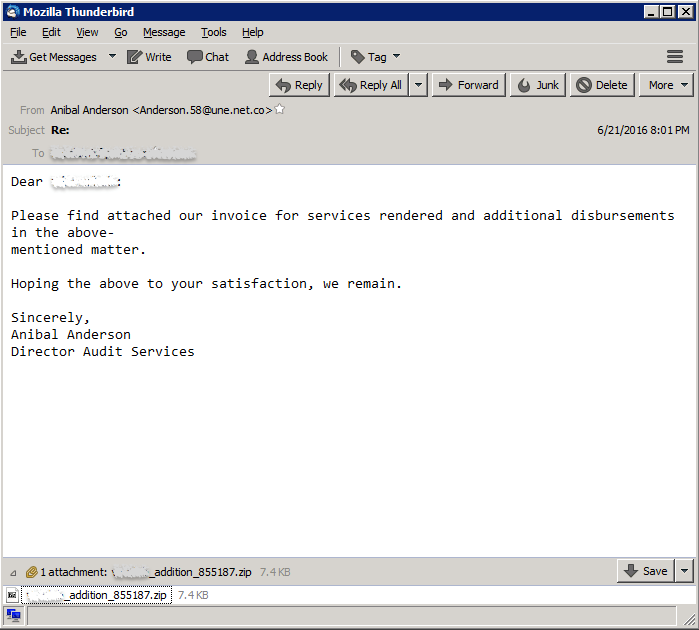
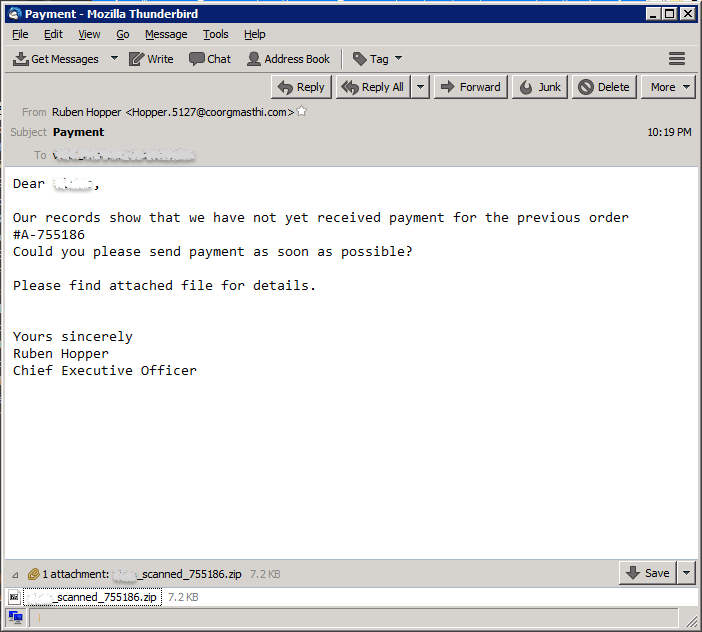
Extracting the javascript from the attached zip file, we find a structure similar to the Nemucod downloader scripts which were recently reported by ESET here: http://www.welivesecurity.com/2016/06/16/nemucod-ups-its-game/. Cyren detects these javascript malware as JS/Locky.AM!Eldorado and JS/Locky.AM1!Eldorado.
After clearing the first layer of obfuscation, it was indeed similar to the structure described in the report, and also employs the same method of download, which also used 3 layers of obfuscation. This obfuscation method obviously aims to prevent scanners from immediately blocking the malware payload which is downloaded and executed into the affected system.
After deobfuscating and saving the binary payload, the authors of this new wave of malware made sure that the binary payloads will only run properly when executed with a specific string argument, which in this case is “123”. This behavior presumably was added by the malware authors to prevent sandboxing systems from analyzing the binary payload if they were processed separately from the script.
After further analysis of the binary payload, which was found to be another custom packer which injects Locky malware code into another process. Cyren detects these variants as W32/Locky.GG and W32/Locky.GH.
Once injected and executed, Locky finds and encrypts files in the system, renaming the files with a unique identifier and adding the extension “.locky”. Similar to the earlier variants, it also drops HTML and PNG instructions on the user’s desktop and also a copy of the HTML instruction in folders where files have been encrypted.
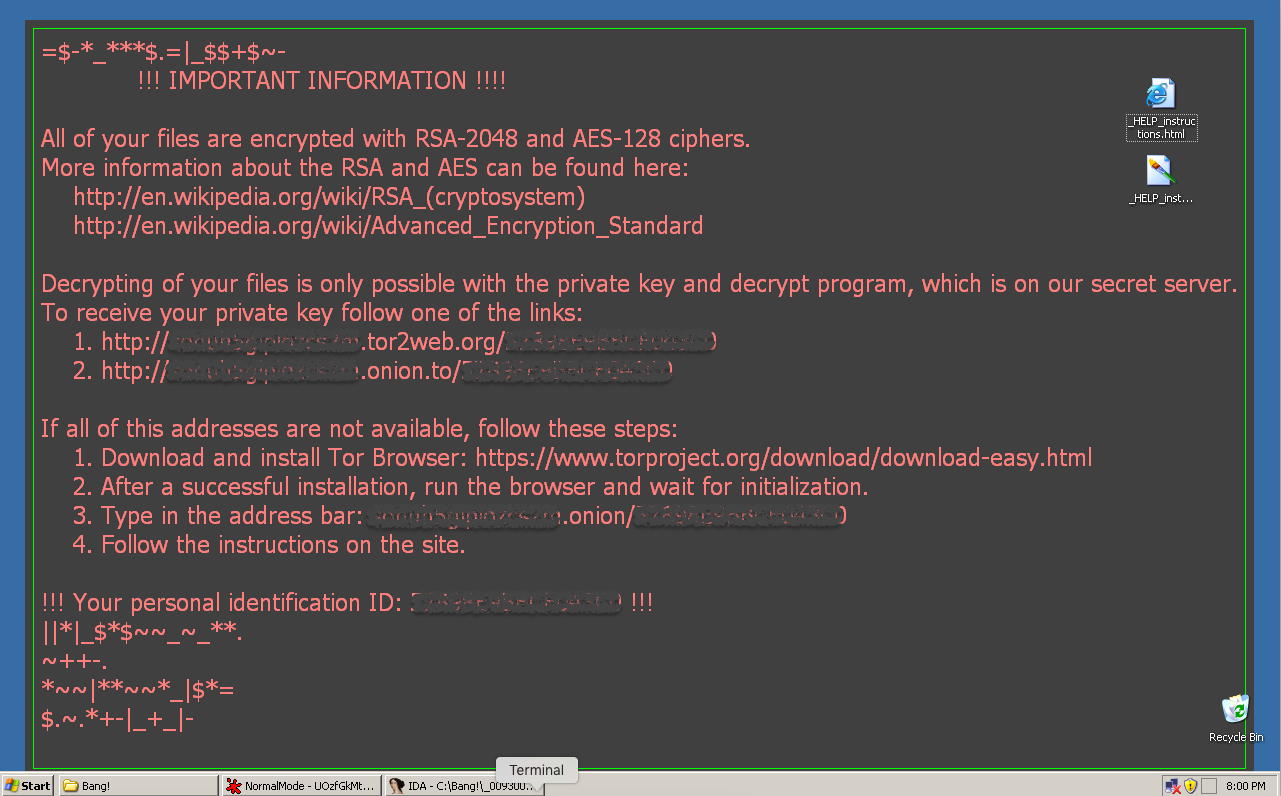
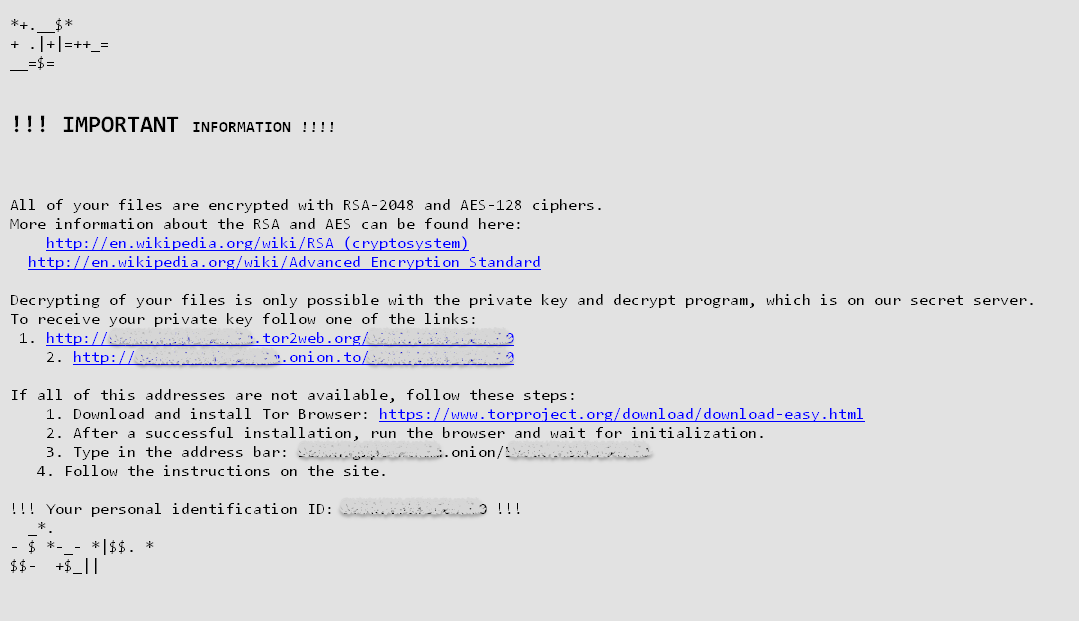
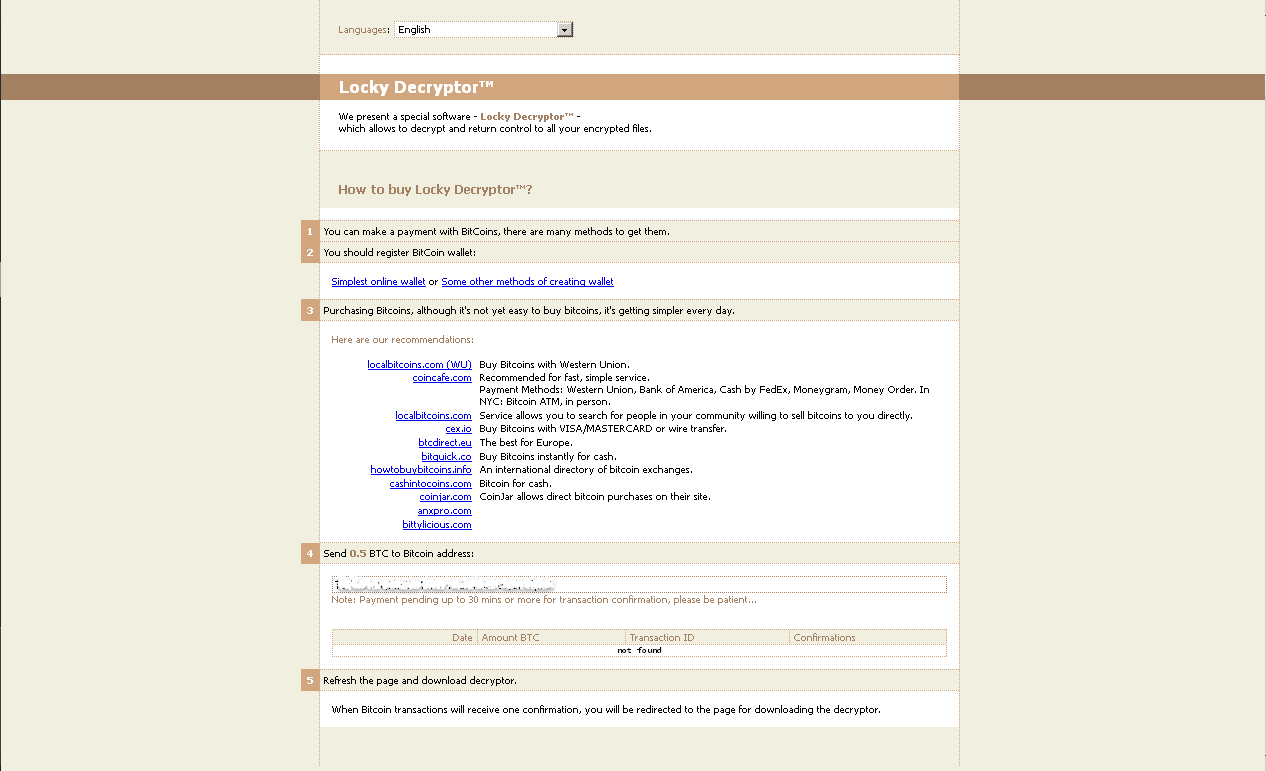
Clicking on the onion/torweb links redirects users to the ransom payment page, which instructs users to buy a decryptor for specific amount of Bitcoins – in this example 0.5 BTC – approximately $340.
As always we strongly advise users to avoid opening emails from unknown senders, and never open attachments that contain executable files like scripts (files using the following file extensions JS, VBS or WSF) and applications.